Cridex Trojan Infection System Forensic Analysis Report
Introduction
Forensics technique is one of the most important ways for analysing themalware. Combining with the static analysis, forensics can help us findthe evidence of a system being attacked and know how the malware infectsthe system step by step.
According to the MITRE ATT&CK framework, the common process ofan attack can be divided into several stages: Reconnaissance, ResourceDevelopment, Initial Access, Execution, Persistence, PrivilegeEscalation, Defense Evasion, Credential Access, Discovery, LateralMovement, Collection, Command and Control, Collection, Exfiltration andImpact.Each step can include several techniques.
In this report, we will use forensics tools Volatility3 to analyse aninfected Windows image and find some attack traces based on the MITREATT&CK framework.
Analysis Tasks
Task1
Processes Investigation
python3 vol.py -f infected-system.vmem windows.info
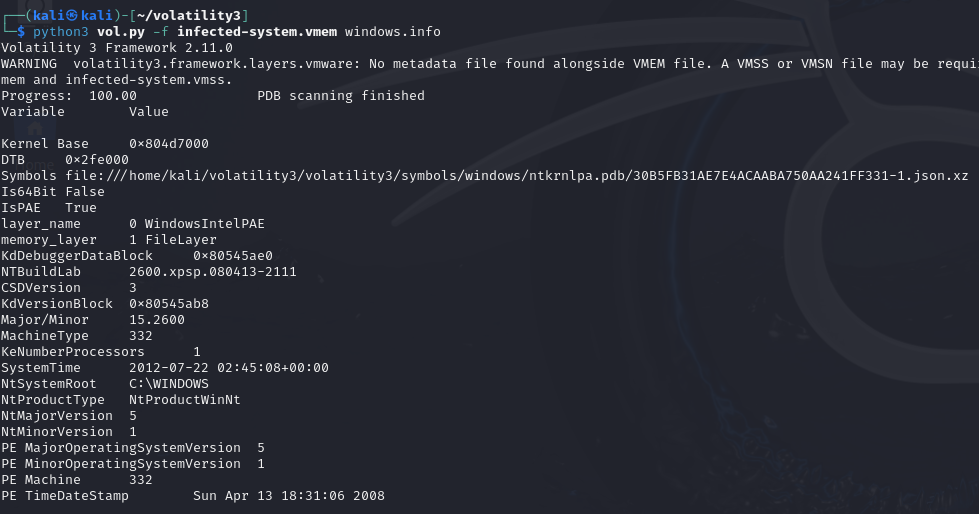
Analysing the system information by using the plugin: windows.info,information show as follows:
1.NTBuildLab shows that this dump uses the version of system: Windows XPSP3
2.MachineType shows that this machine uses X86 architecture 32 bit
3.SystemTime shows the time that create this dump Now, we can makesurethat this is a windows machine and we can use the corresponding pluginsfor further analysis.
python3 vol.py -f infected-system.vmem windows.pslist
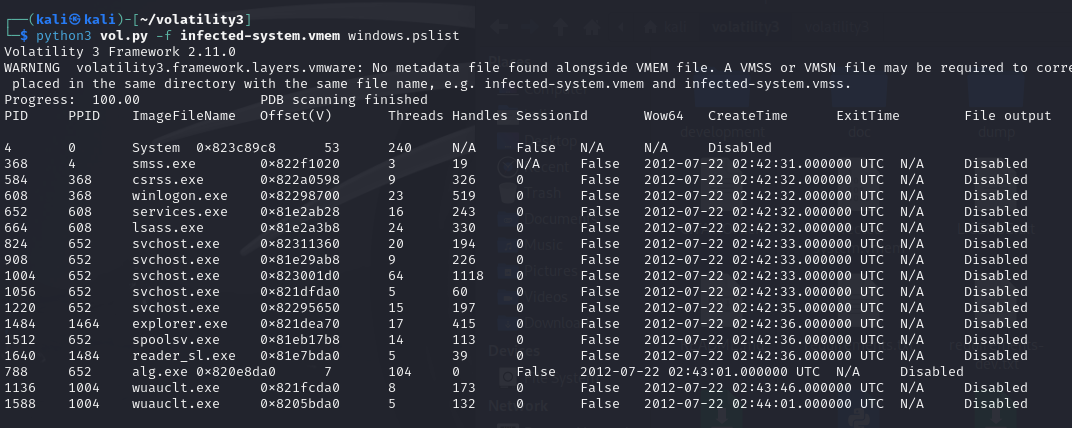
windows.pslist can show all the running processes when built this dump,we can find that all the processes are named as system processes expectreader_sl.exe. It is a little bit suspicious that reader_sl.exe startedvery early in the system startup, according to the CreateTime of theprocesses, which may be an auto-start evil program to persist itself.
python3 vol.py -f infected-system.vmem windows.pstree
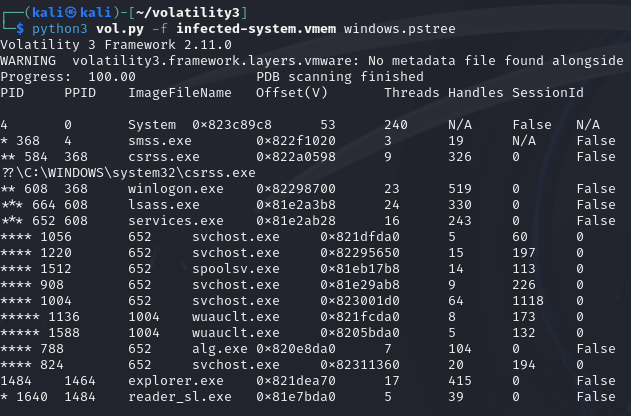
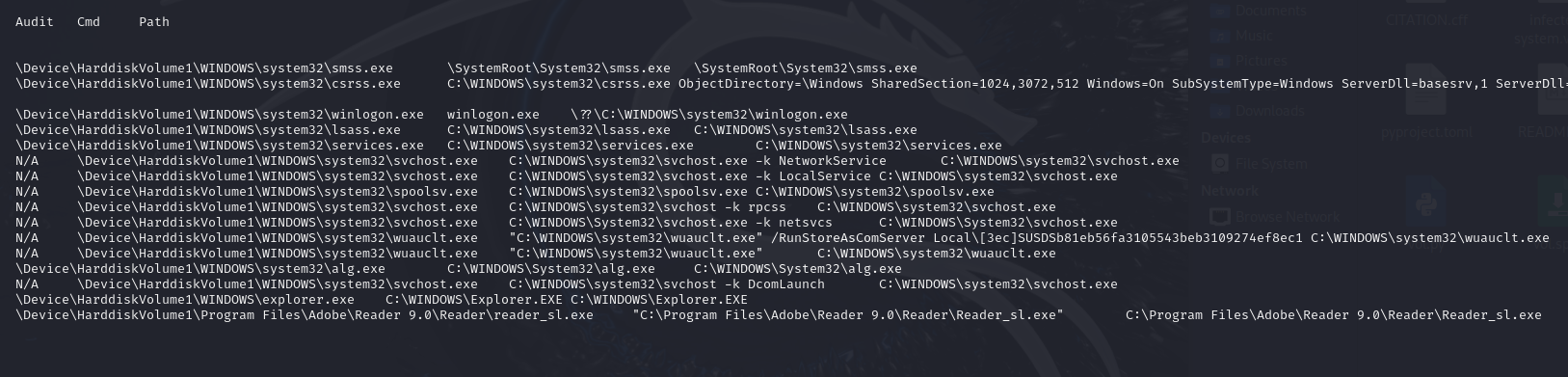
windows.pstree plugin can show the dependencies between processes byusing Process ID (PID), Parent PID (PPID) and show the executable pathof the programs, which can help us finding some suspicious processes.
All the processes can find their parent processes using PPID expectexplorer.exe(PPID 1464 can not be found in the processes list), whichprobably means that some malicious process spawned this process and haskilled itself. Besides, explorer.exe usually started by wininit.exe oruserinit.exe, but these two processes can not be found in this processeslist.
wuauclt.exe is a system update process, but there are two wuauclt.exeprocesses running together: PID 1136 and PID 1588, which is abnormal.
All the executable paths of processes are look right, which means thatthe malicious processes do not disguise themselves by simply changingtheir names.
Module Scanning
python3 vol.py -f infected-system.vmem windows.modules.Modules
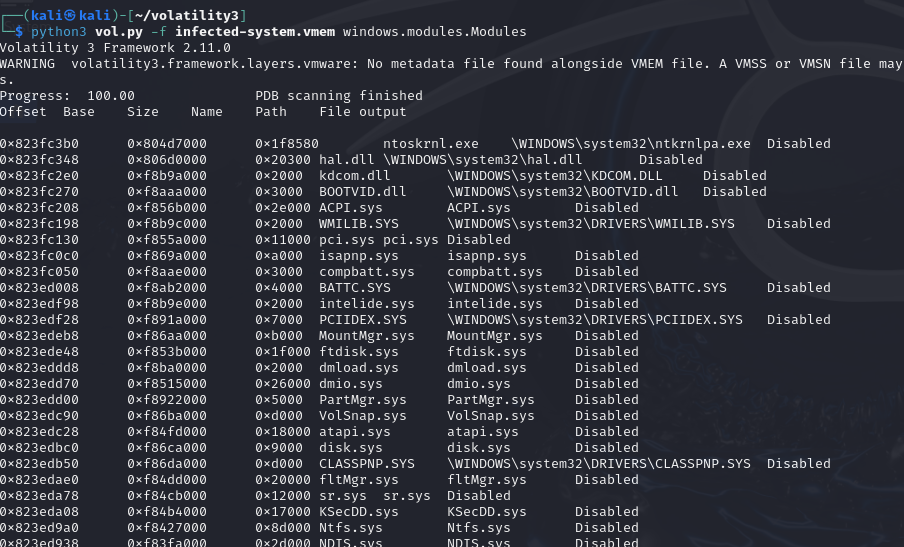
windows.modules.Modules plugin shows all the system driver files,responsible for managing hardware communication or providing core systemfunctionalities. Malicious programs often disguise as a driver file toelevate privileges.
From figure above we can find that there are some driver files that donot locate in the system path(such as System32) and all the file outputsare disabled, which is quite suspicious, maybe there are something wrongwith these outputs, or there are some core modules are disabled bymalicious processes.
At the same time, i use dlllist plugin to test two suspicious programsabove PID 1484 and PID 1640
python3 vol.py -f infected-system.vmem dlllist --pid 1484 python3 vol.py -f infected-system.vmem dlllist --pid 1640
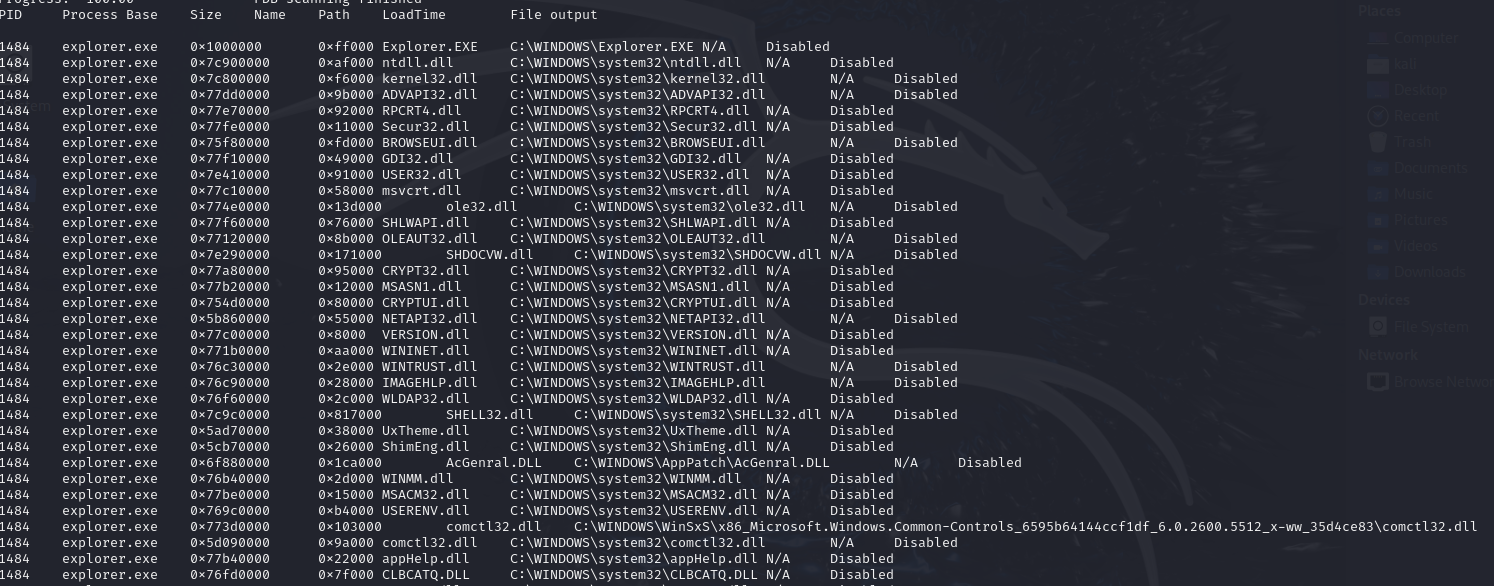
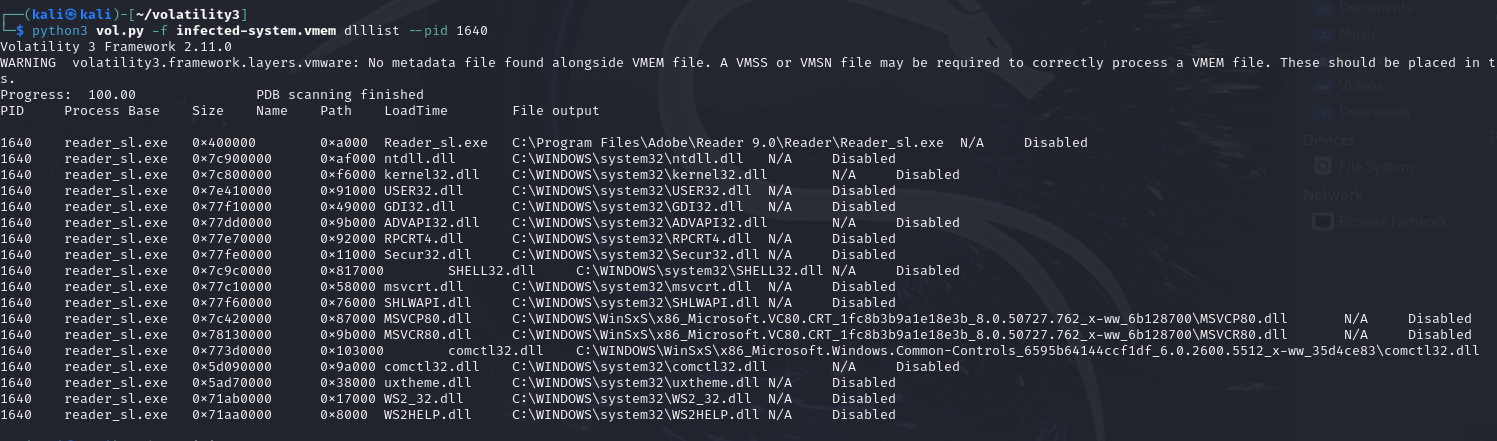
Figures above clearly shows that these two programs load the evil dllfile named comctl32.dll, containing "commad-controls" path keyword,which means that these two programs were infected and can be used toconnect with Command and Control(C2) servers.
python3 vol.py -f infected-system.vmem dlllist|grep comctl32.dll
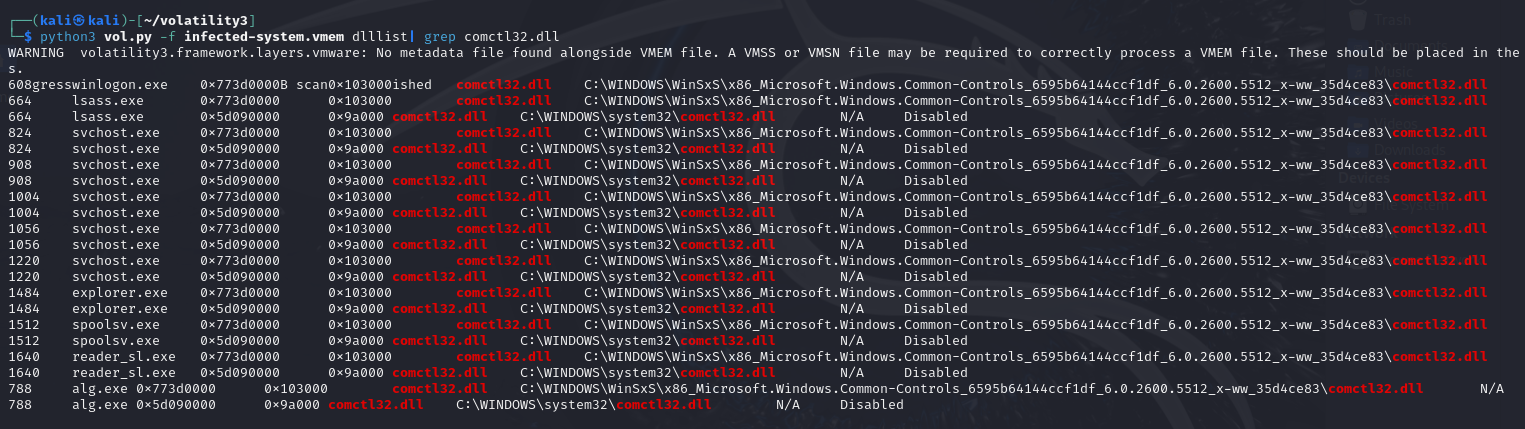
If we search comctl32.dll from dll list, we can find that many processeswere infected by this evil dll, which could allow attackers control thiscomputer from remote addresses.
Detection and Mitigation
Based on the MITRE ATT&CK Navigator,the progress of trojan attack contains several steps, such as: InitialAccess, Execution, Persistence, Privilege Escalation, Command andControl (C2) and Data Exfiltration. In this task, we mainly focus on thefirst two stages: Initial Access and Execution.
(1) Initial Access:
There are several methods that can gain the initial access of asystem,such as phishing attack and valid accounts, we will talk aboutsome detection and mitigation methods below:
1. Phishing attack
Phishing attack is the most common attack methodused in initial access. We can use the following method to preventPhishing:
a. Email filtering and anti-phishing protection: Before emails arereceived, security email gateway will filtrate some suspicious emails.If users open the attachment file, file will be scaned and open in thesandbox environment to protect the local PC.
b. Network Attack Defense: If users’ PC connect to IP or URL, thesecurity of IP or URL will be detected as IoC. If the IP or URL aresigned evil or malicious, connection will be stopped.
c. Security training and report mechanism: Every employees in thecompany should be trained regularly to have the awareness of emailsecurity, which could stop them from opening the malicious emails andthen report this events to the security engineer.
2.Valid accounts:
Attackers always try to collect valid accounts from internal or outsideand try to gain access privileges, we can use strategies relatedaccounts to detect and mitigate this kind of attack.
a.Account abnormal monitoring: Monitor the behaviors of users’ accountsand try to find some abnormal login behaviors such as login from auncommon IP address.
b.Multi-Factor Authentication(MFA): Any uncommon login behavior will bedouble checked.
(2)Execution:
There are some common ways that can be used to execute the maliciousprogram, such as user excution, scheduled tasks, processinjection and so on, we will talk about detection andmitigation methods below:
1. Anti-Virus(AV) defender:
AV can detect the known malware file based on the IoC such as file hash.If evil files are downloaded or executed, they will be detected by AVengine.
2. Endpoint Detection and Response(EDR):
EDR can detect malicious behaviors such as process injection, processhijacking, service creating, network connection and file access, notjust depend on the static characteristics.
3. Network Attack Defense:
If users’ PC connect to IP or URL, the security of IP or URL will bedetected as IoC.If the IP or URL are signed evil or malicious,connection will be stopped.
Task2
SIDs Check
python3 vol.py -f infected-system.vmem windows.getsids.GetSIDs
We use windows.getsids.GetSIDs plugins to find Security Identifiers(SIDs), we find that there is a user called Robert who can start asystem process wuauclt.exe(PID 1588), which is noticeable. Firstly, Ifthis Robert is not a nomoral user, it may be created by hacker and usedto do something evil. Besides, a system process that can be executed bya user account means that this process is a disguised as evil process.
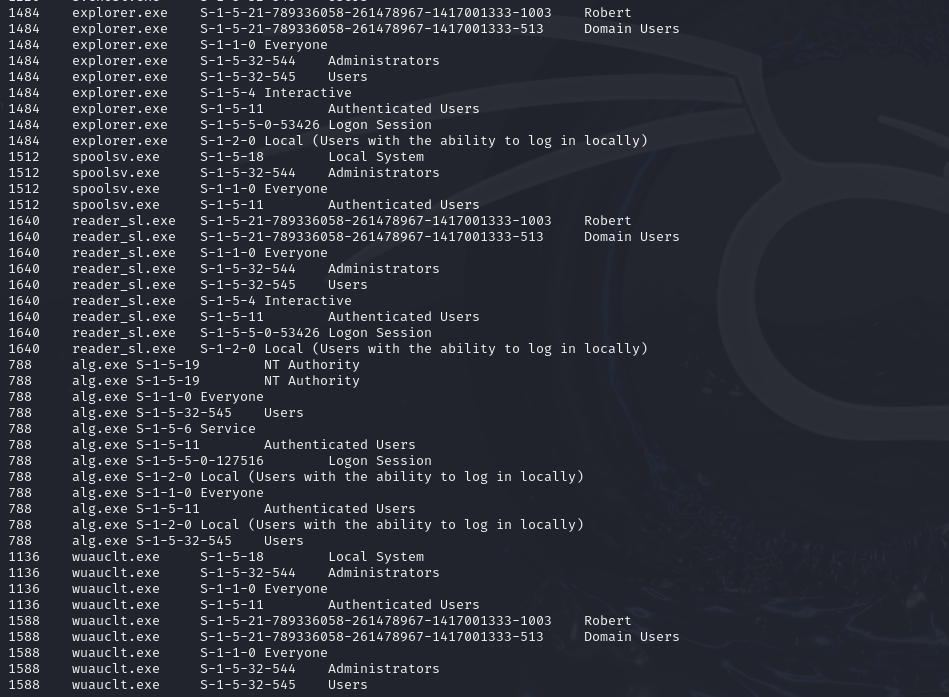
We filtrate the processes that can be executed by Administrators group.We can see the result from the figure below, which shows that most ofthem are system processes except reader_sl.exe and wuauclt.exe(PID1588). This is exactly the suspicious processes that we analyse earlier,if they can be executed by the account that has administratorprivileges, it can be used to elevate the privileges.
python3 vol.py -f infected-system.vmem windows.getsids.GetSIDs | grep Administrators
Privileges Check
python3 vol.py -f infected-system.vmem windows.privilege | egrep -i "1640|1588"
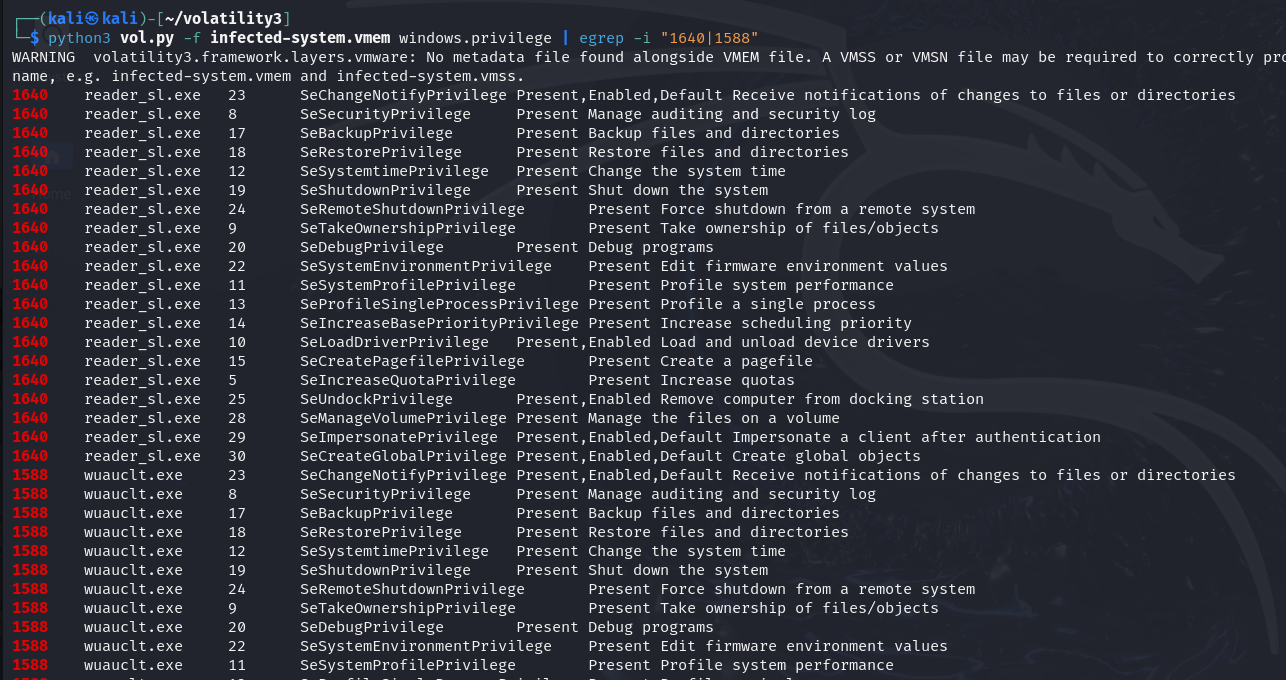
We use windows.privilege plugin to detect the privileges of the programand find some suspicious points that reader_sl.exe has extramely highpermissions such as SeDebugPrivilege, SeTakeOwnershipPrivilege,SeImpersonatePrivilege and so forth, which do not belong to a normaluser progam. The wuauclt.exe is the same. From the analysis, we can getthe conclusion that some processes have been used to elevate privileges.
Environment Variables
In this section, we will check the environment variables of theprocesses to find some potential abnormal paths.
python3 vol.py -f infected-system.vmem windows.envars.Envars | egrep -i "Path|HOMEPATH"
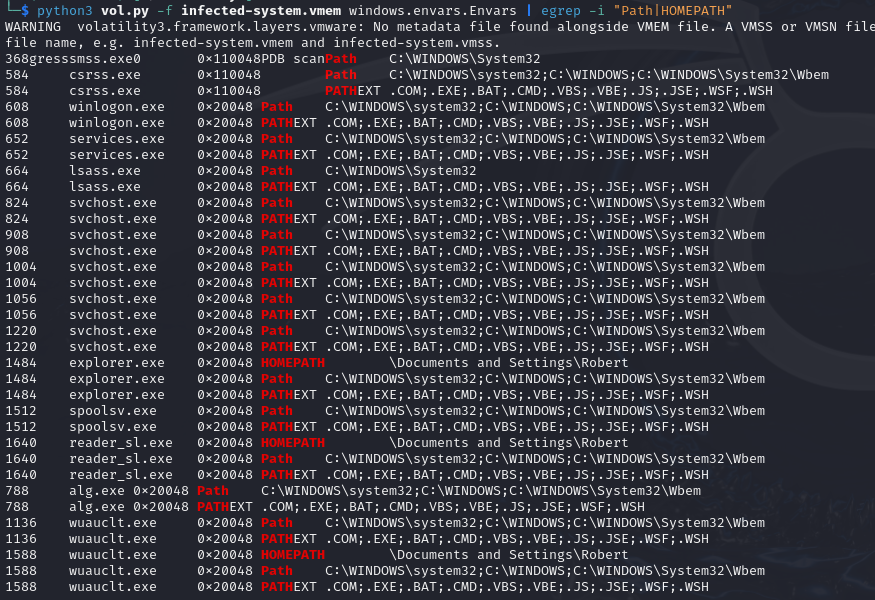
We find that wuauclt.exe is a system process, but wuauclt.exe(PID 1588)has an environment variable called HOMEPATH which means that it is auser process. This confilication indicate that this process is likely amalicious software disguised process.
We filtrate the TEMP folder, which always used by malicious software todownload or store some file.
python3 vol.py -f infected-system.vmem windows.envars.Envars | egrep -i "TEMP"
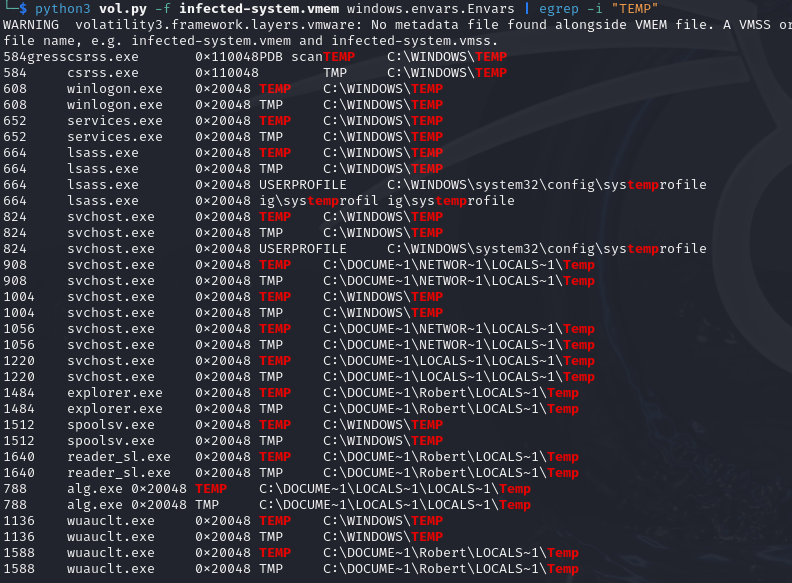
We also find that the system process wuauclt.exe(PID 1588) used thelocal user temp folder, which once again confirms the judegment before.
python3 vol.py -f infected-system.vmem windows.handles --pid 1588
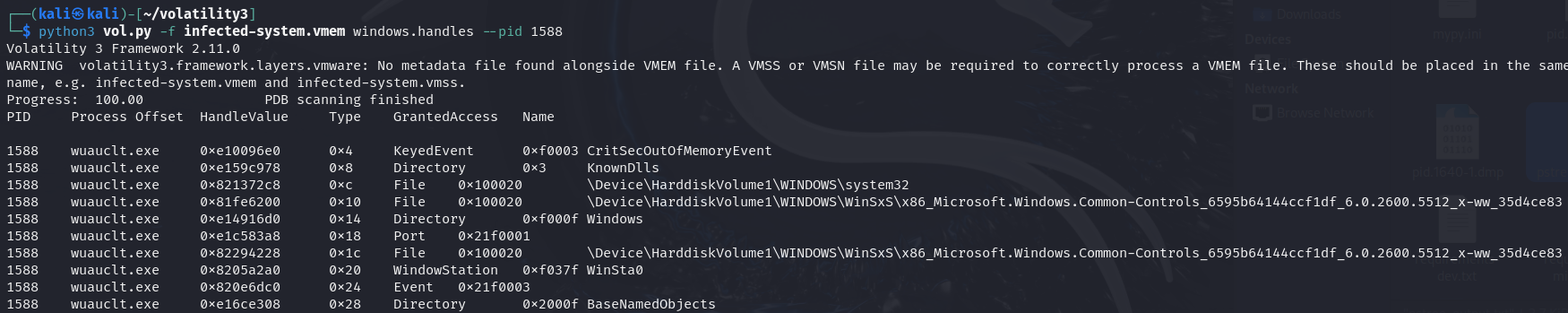
We can check the handles of the PID 1588, and found that it has beeninjected by the C2 dll.
Detection and Mitigation
In this task, we mainly focus on the next stage: PrivilegeEscalation. There are four common methods thatcan be used to elevate the privileges: credential exploitation,vulnerabilities and exploits, misconfigurations and malware, and we willtalk about some detection and mitigation ways below:
(1) Credential exploitation:
Multi-Factors Authentication(MFA): Attackers always try to collectand use some system account to pass the authentication. So we may findsome attempt records in system logs. If we use the MFA, system will askuser for further information to verify the identification, which is astrong way to stop attackers from gaining access to the system.:::
(2)Vulnerabilities and exploits:
Update and Patch the system on time: Make sure that the system issecure and do not have any known vulnerability, which can make it moredifficult for attackers to escalate privileges by exploiting knownvulnerabilities.:::
(3)misconfigurations:
Strictly manage changes to accounts and configurations: Real-timemonitoring and event log analysis can detect the changes of the accountsand configurations. IF abnormal changes occur, the alarm will betriggered.:::
Least privileges: Make sure any account can only get theprivileges that it needs.:::
(4)Malware:
Comprehensive log analysis: Use Security Information and EventManagement(SIEM) to collect and analyse many kinds of log informationgenerated from the system, such as firewall, network equipment andservers, which can find some evil behaviors like privilege escalation.:::
Processes monitoring and isolation: Monitoring the processes,which belongs to system or have high privileges, if there are systemprocesses that have the same name or some abnormal privilegesmodification, these processes will be isolated to stop them from furtherexploiting.:::
Task3
Malware Detection
We used windows.malfind plugin to detect processes that contain segmentshaving the privilege "PAGE_EXECUTE_READWRITE", which is the skill thatcommonly used by malicious programs to modify and execute codedynamically.
python3 vol.py -f infected-system.vmem windows.malfind | grep "PAGE_EXECUTE_READWRITE"
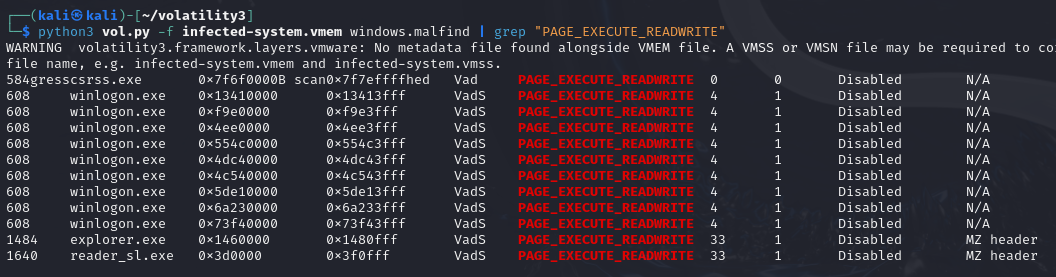
From the figure above we can see, process explorer.exe and reader_sl.execontain MZ header, which means that Windows executable program hidden inthese two processes. This is a obvious sign that processes have beeninjected by malicious code.
Registry Persistence Analysis
In this section, we will check the common registry key always used bymalicious processes to persist privileges.
python3 vol.py -f infected-system.vmem windows.registry.printkey --key "SOFTWARE\Microsoft\Windows\CurrentVersion\Run"
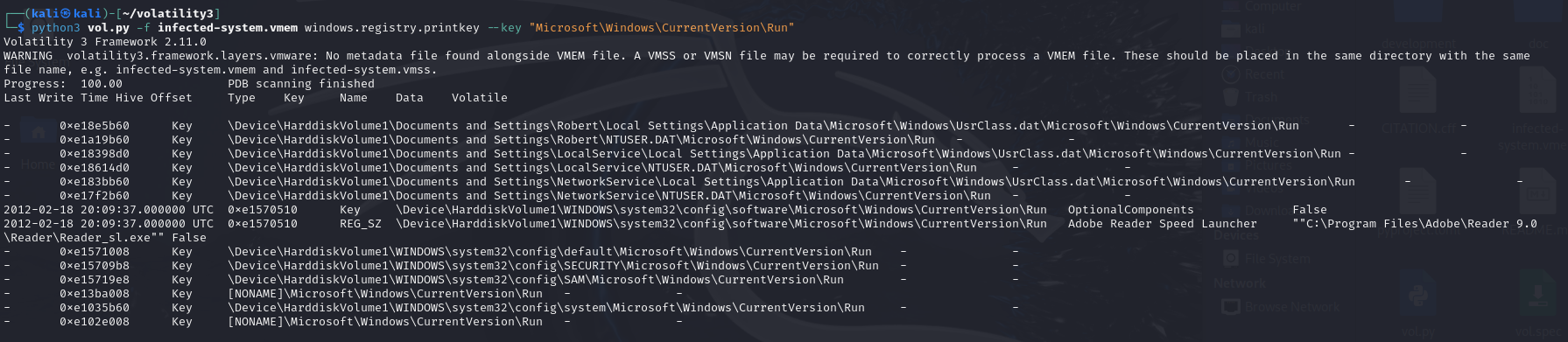
Using the plugin windows.registry.printkey and filtrate the"SOFTWARE\Microsoft\Windows\CurrentVersion\Run" key, we can findthat there is a last change that set KB00207077.exe in auto-start path.This is definitely not a normal program and should be a maliciousexecutable file. When system start up, this executable file can beexecuted, which can make sure its persistence.
python3 vol.py -f infected-system.vmem windows.registry.printkey --key "SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer"
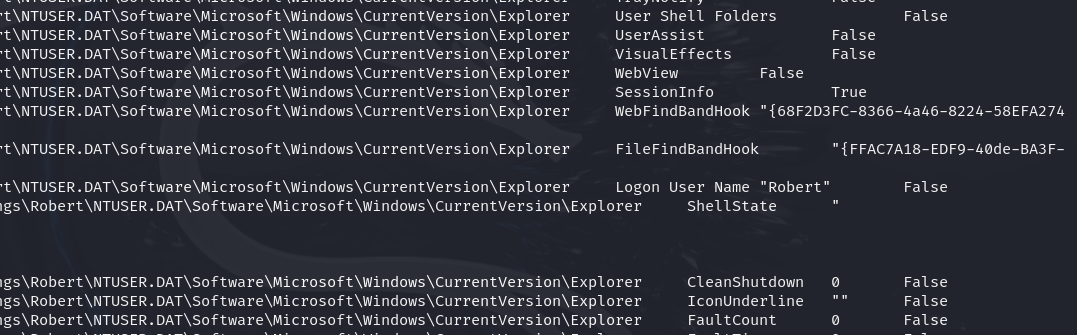
By searching the key"SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer" we can findthat there are some hook points in web-find and file-find. These areabnormal behaviors, which are always used to hijack users’ normalactions. When users search for something in the browser or in filesystem, malicious code can be triggered.
Command Records
Plugin windows.cmdline can be used to analyse the process command tofind some abnormal behaviors.
python3 vol.py -f infected-system.vmem windows.cmdline
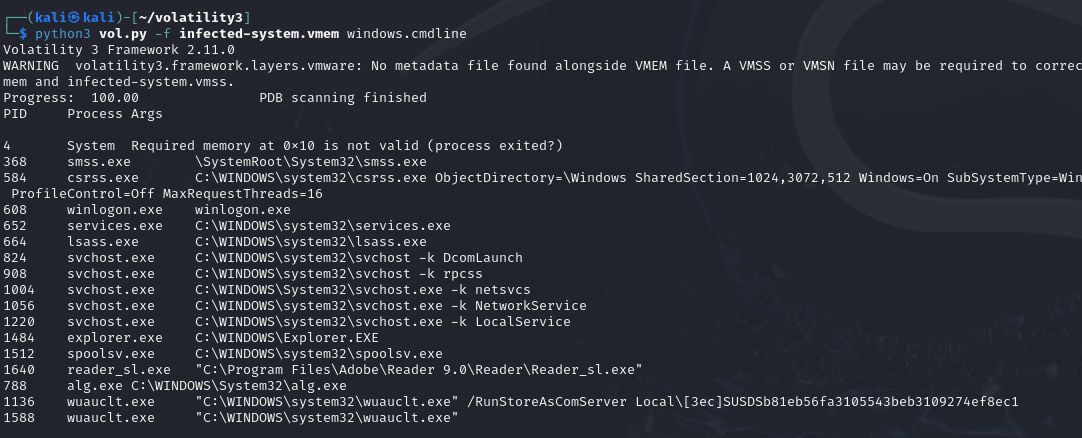
We could see that process wuauclt.exe(PID 1136) use the/RunStoreAsComServer command and follows a file as parameter which nameis hash format. This is abnormal and is probably a some kind ofinjection and persistence behavior.
Persistence Mechanism Identification
In this section we will discuss persistence technologies, which is asiginficant way for attackers to gain the control of the systempersistently. The common ways of persistence include:accounts creation, scheduled tasks, services/drivers masquerading,processes injection, registry modification and so on.
(1)Accounts creation:
1. Regularly check for additions and modifications to accounts andaccount groups, identify the evil changes.
2. Follow least privilege principle to restrict the privilege that canmodify or create accounts.
3. MFA: Using MFA to stop attacker from using collect accountsinformation continuously.
4. Remove inactive account: Removing dormant accounts regularly canreduce account exploitation.
(2)Scheduled tasks and registry modification:
1. Monitoring the creation and modification of the scheduled tasks andregistry.Stop any unauthorized access.
2. Use SIEM to collect and analyse corresponding logs, if anythingabnormal occur, triggers the alarm.
(3)Services/drivers masquerading:
1. Check services/drivers list reguarly to find unsigned or unknownservices/drivers
2. Implement a mandatory signature mechanism and control the creationpermission strictly.
(4)Processes injection:
1. EDR monitor: Use EDR to detect the abnormal behaviors of processeslike injection, connecting to known IP or URL.
Task4
User Activities Tracking
We use the windows.registry.userassist plugin to show the executionrecords in the Windows GUI.
python3 vol.py -f infected-system.vmem windows.registry.userassist | grep UEME_RUNPATH
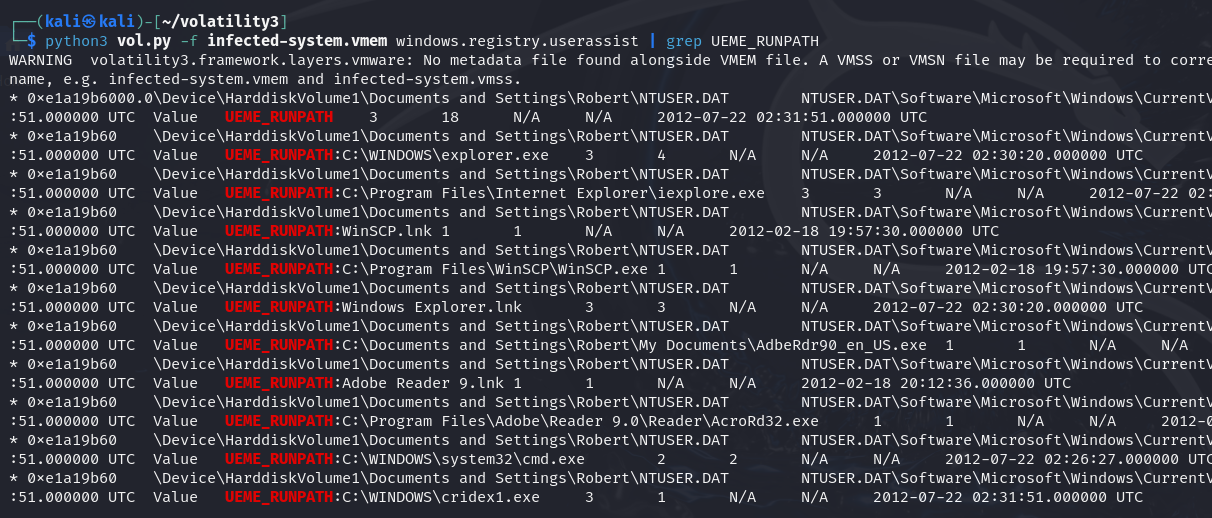
We can clear see that WinScp.exe was executed, which is a file transfertools probably used to download some evil file from remote evil server.Besides, the executable file called cridex1.exe was executed finally,which is a classic Trojan file.
Hidden Processes
python3 vol.py -f infected-system.vmem windows.psxview
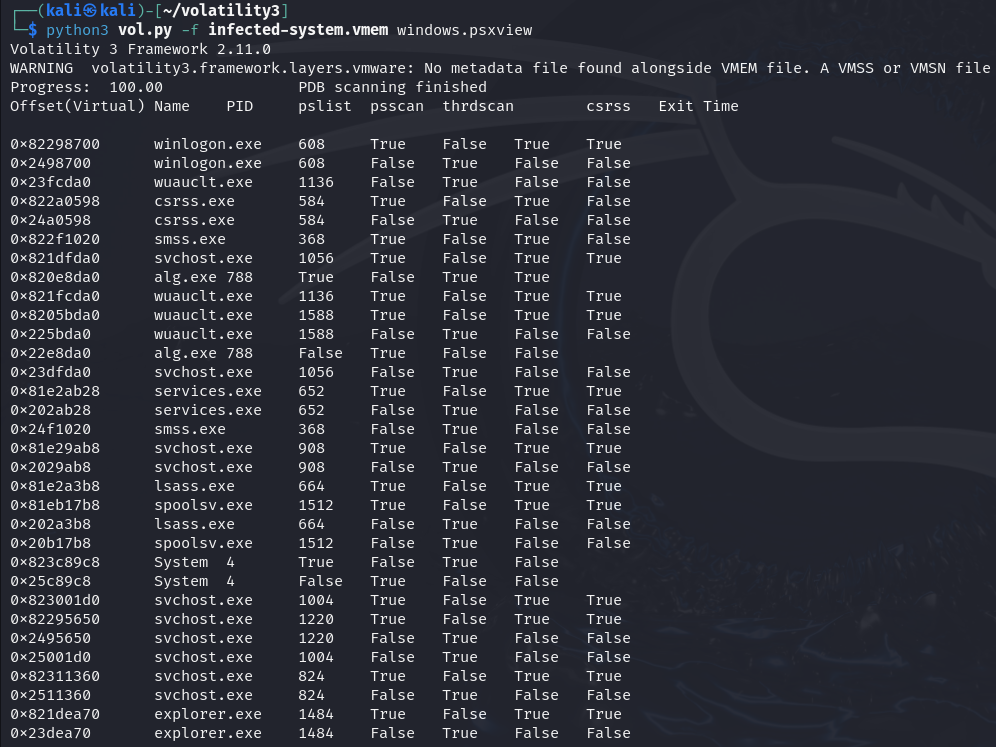
According to the investigation we did before, we can find two maliciousprograms: cridex1.exe and KB00207077.exe, but we can not find them whenwe use the pslist or psscan plugin, so maybe they were hidden , and wewill try to find them from the memory dump.
python3 vol.py -f infected-system.vmem windows.filescan | egrep -i "cridex|KB"
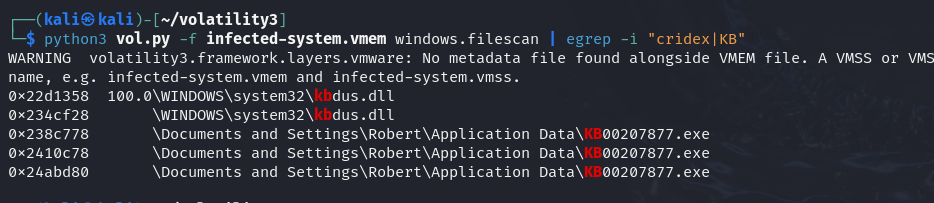
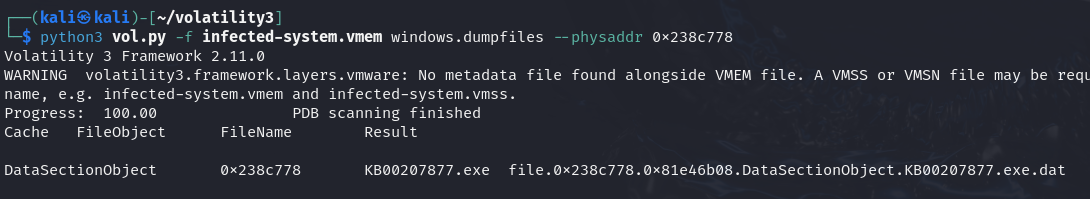
Now, try to dump this file from the memory and make sure what thefunction is.
python3 vol.py -f infected-system.vmem windows.dumpfiles --physaddr 0x238c778 python3 vol.py -f infected-system.vmem windows.dumpfiles --physaddr 0x2410c78 python3 vol.py -f infected-system.vmem windows.dumpfiles --physaddr 0x24abd80
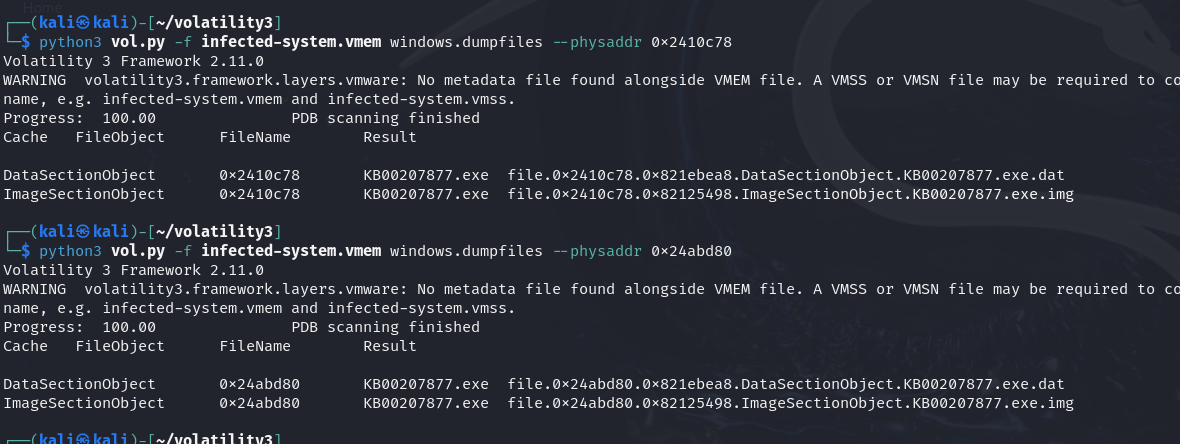
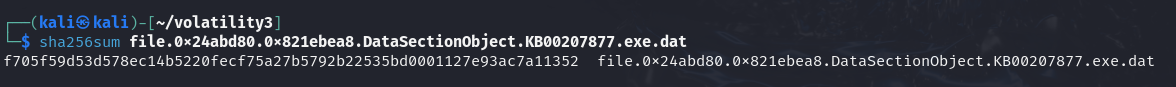
Then, we use sha256sum to generate the hash, and search them in Virustotal
sha256sum file.0x2410c78.0x821ebea8.DataSectionObject.KB00207877.exe.dat
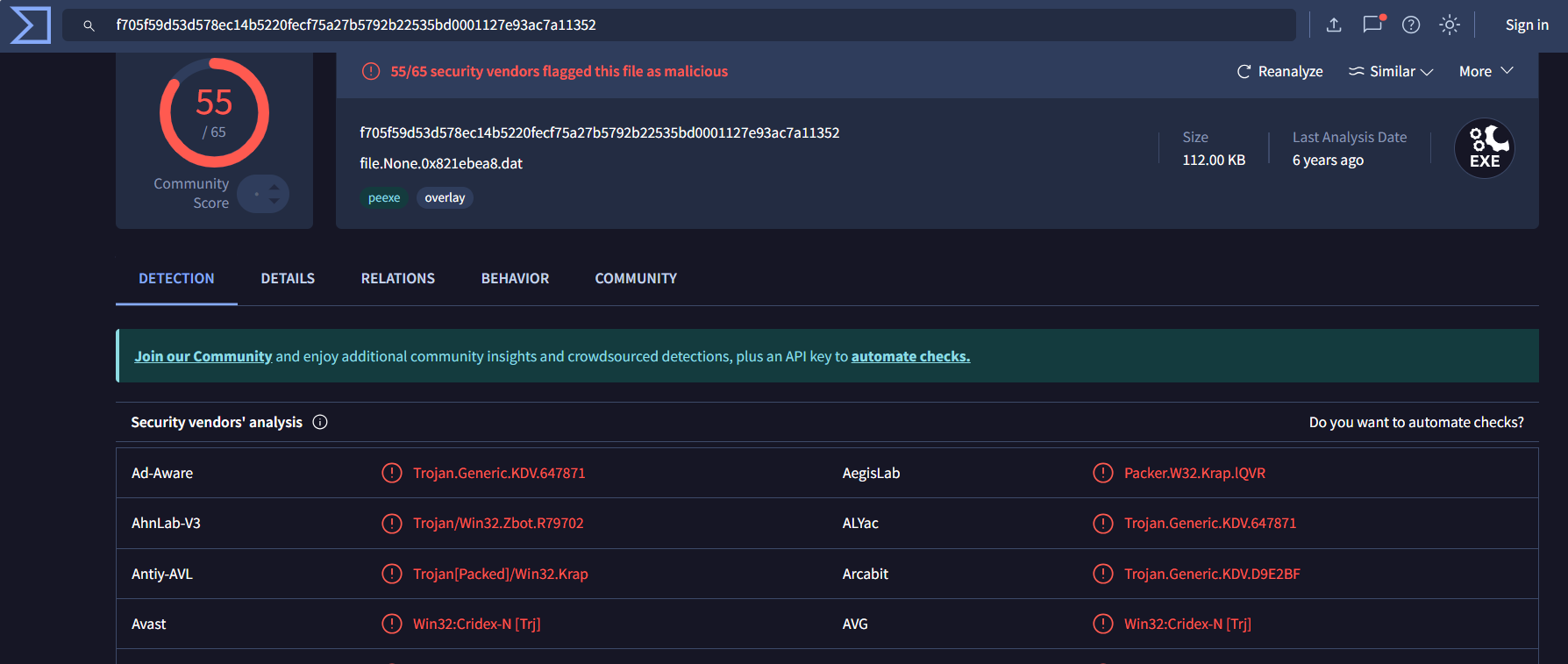
We can see that this file is exactly malicious and is identified asCridex, which is a classic bank Trojan, same as what we found in thesection above. Besides, in the above section, we tried to usewindows.malfind plugin and found explorer.exe, reader_sl.exe has beeninjected in a Windows executable file segment, which is a common methodthat a evil process hide itself.
Search Strings
We choose the process of explorer.exe, reader_sl.exe and wuauclt.exe asthe objects of our analysis.
python3 vol.py -f infected-system.vmem windows.memmap --pid 1484 --dump python3 vol.py -f infected-system.vmem windows.memmap --pid 1640 --dump python3 vol.py -f infected-system.vmem windows.memmap --pid 1588 --dump
We use strings command combined with egrep command to filtrate somesuspicious strings from dump files.
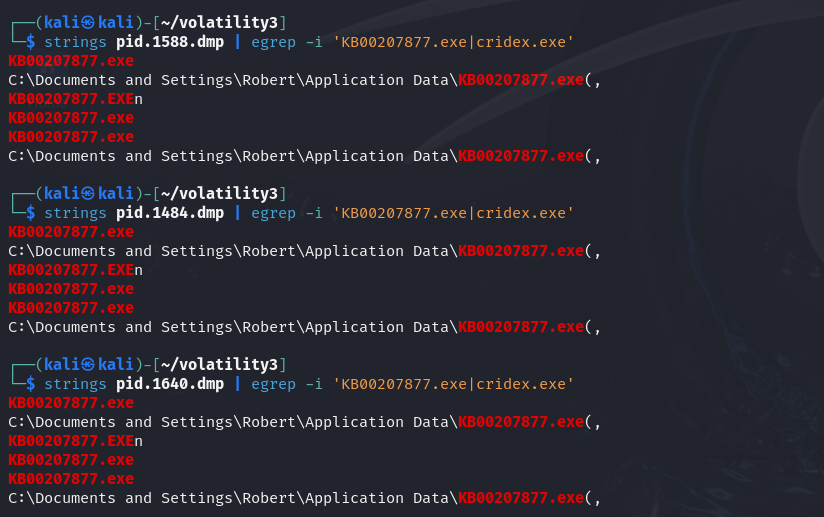
We can find from the result that these three processes all related tothe evil KB00207877.exe, so they are all infected or injected.
Now, we will try to combine these three dumps together and use stringscommand to find some suspicious strings.
strings pid.1640.dmp pid.1484.dmp pid.1588.dmp > suspicious.dmp
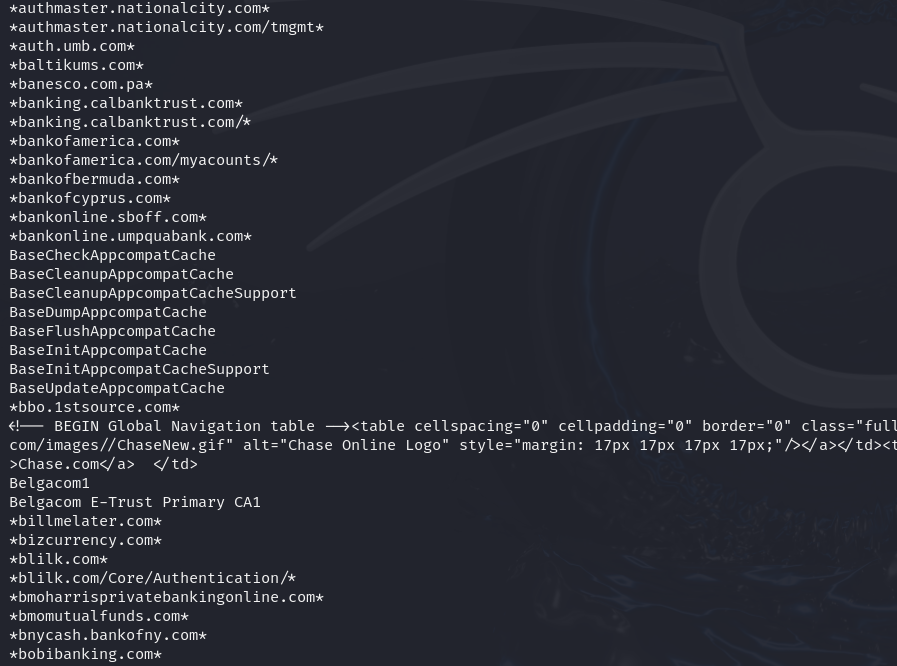
We try to grep string ‘.com’ and find that there are lots of stringsrelated to banks, which means that this Trojan targets banks forattacks.
strings suspicious.dmp | grep '.com'| sort -u
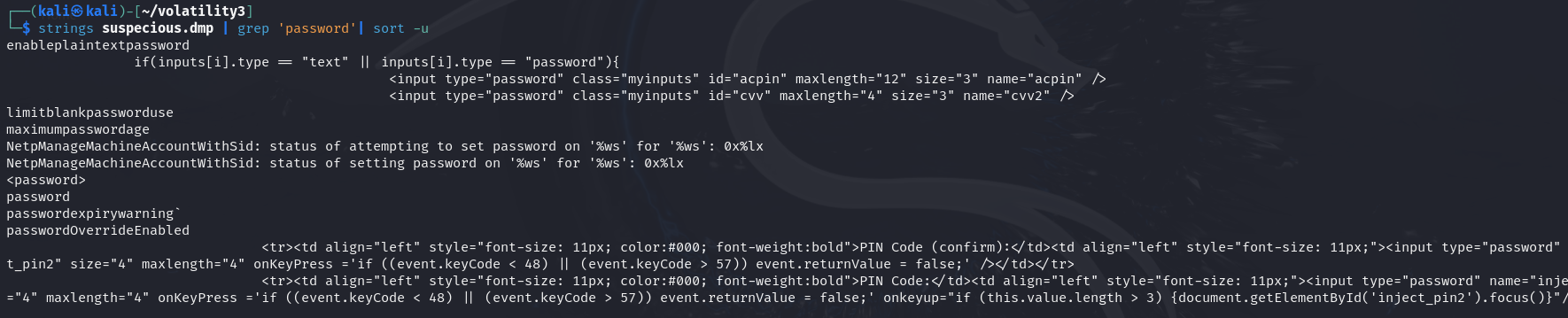
We also search the keyword "password", and the result shows that thisTrojan tries to pretend a page of receiving PIN code.
strings suspicious.dmp | grep 'password'| sort -u
IP address is another important information that can show the address towhich the Trojan connects.
strings suspicious.dmp | grep -P -o '(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)' | sort | uniq
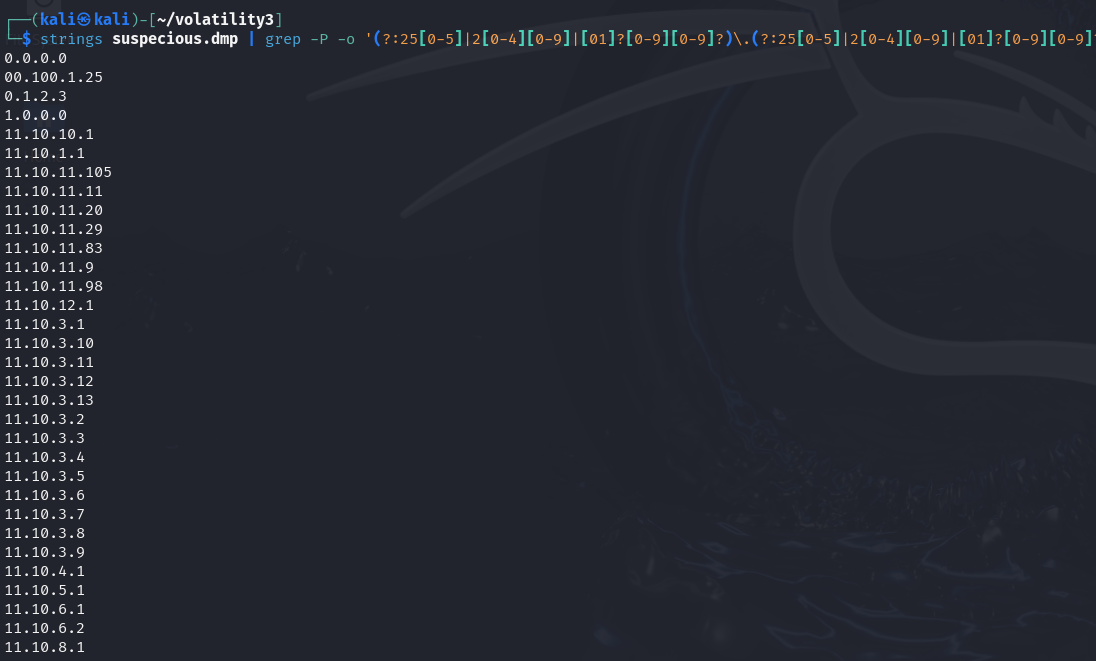
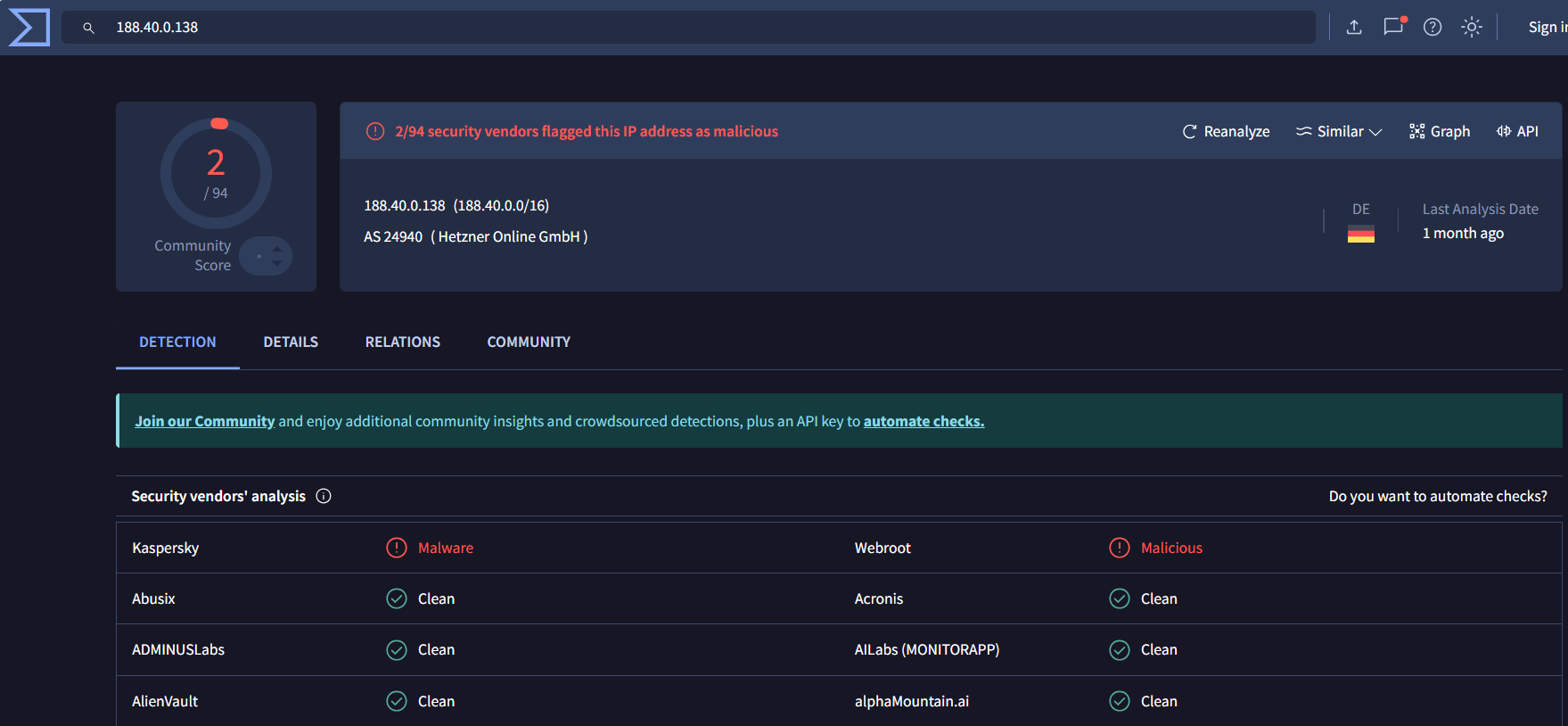
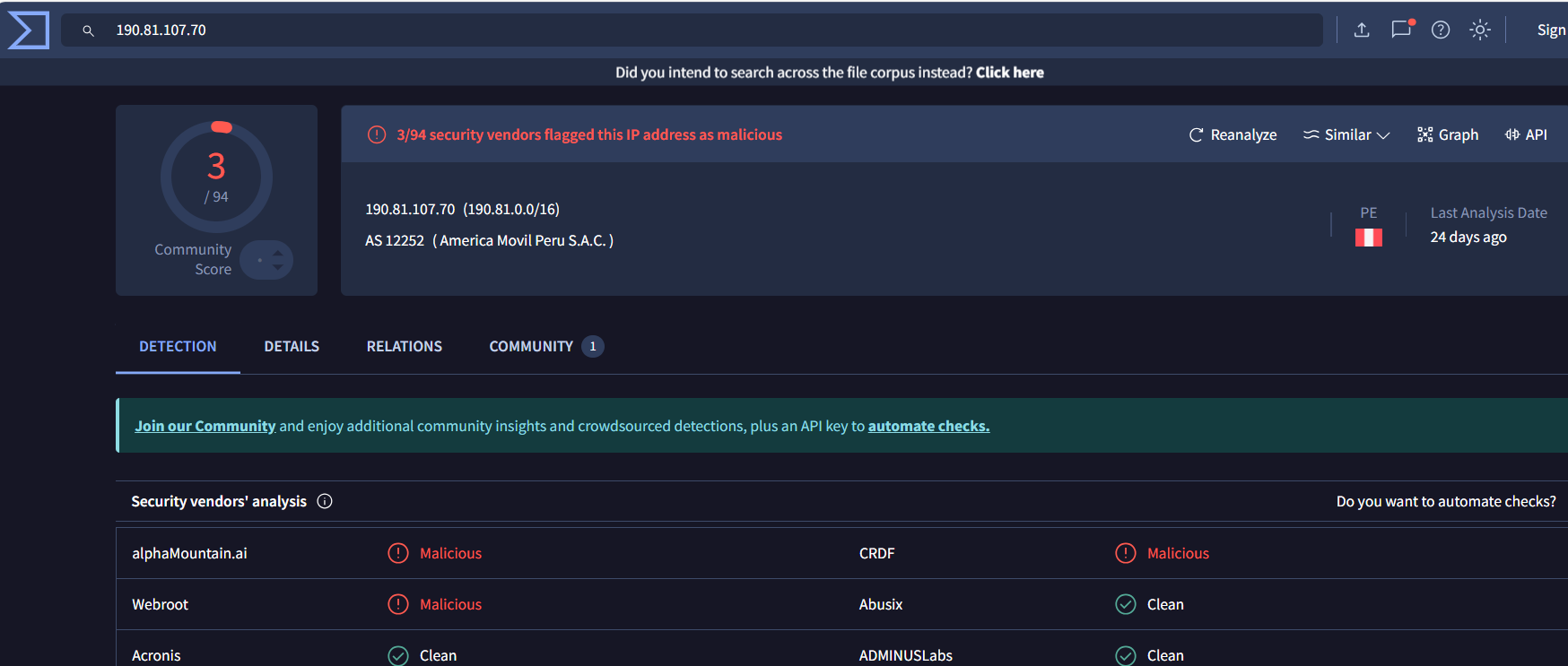
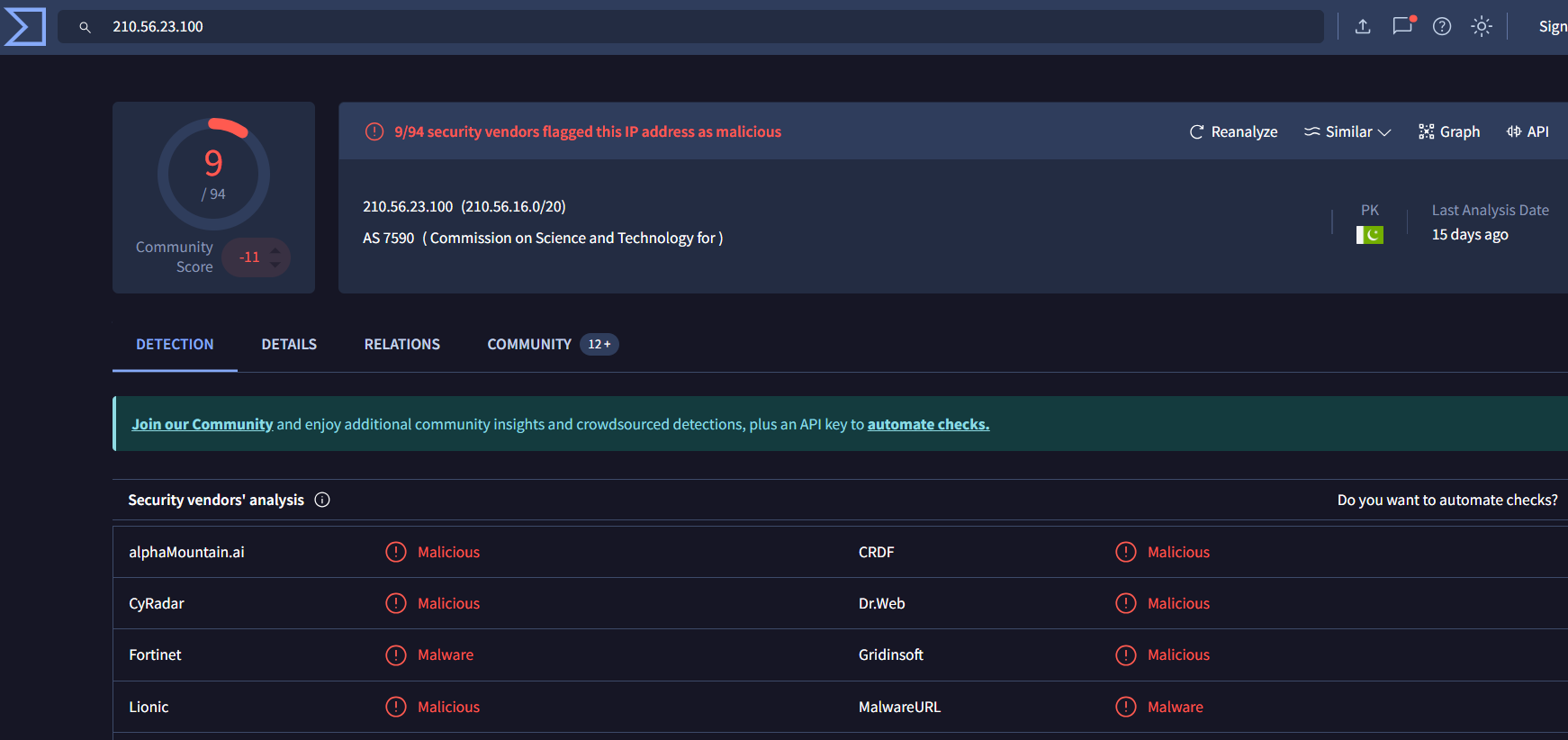
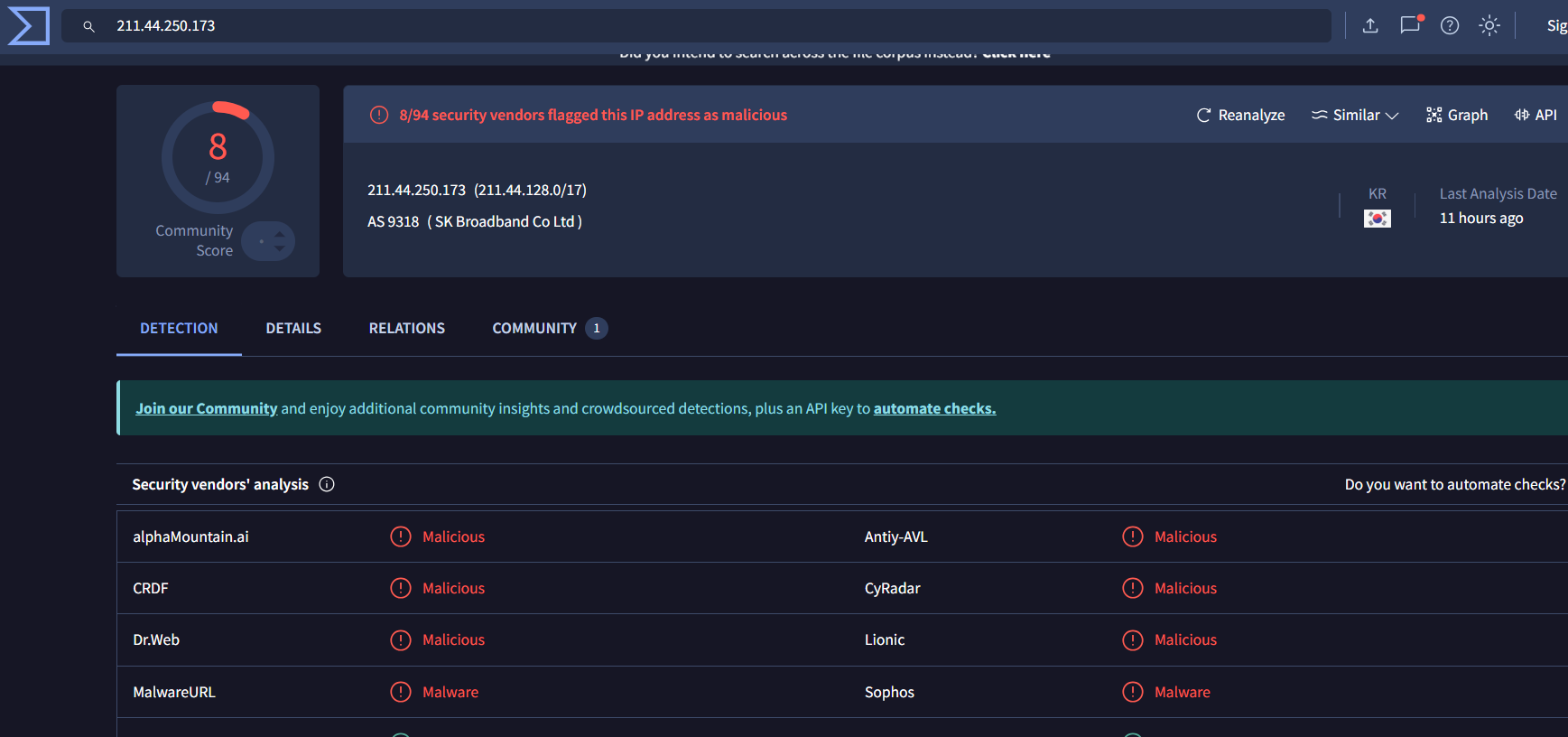
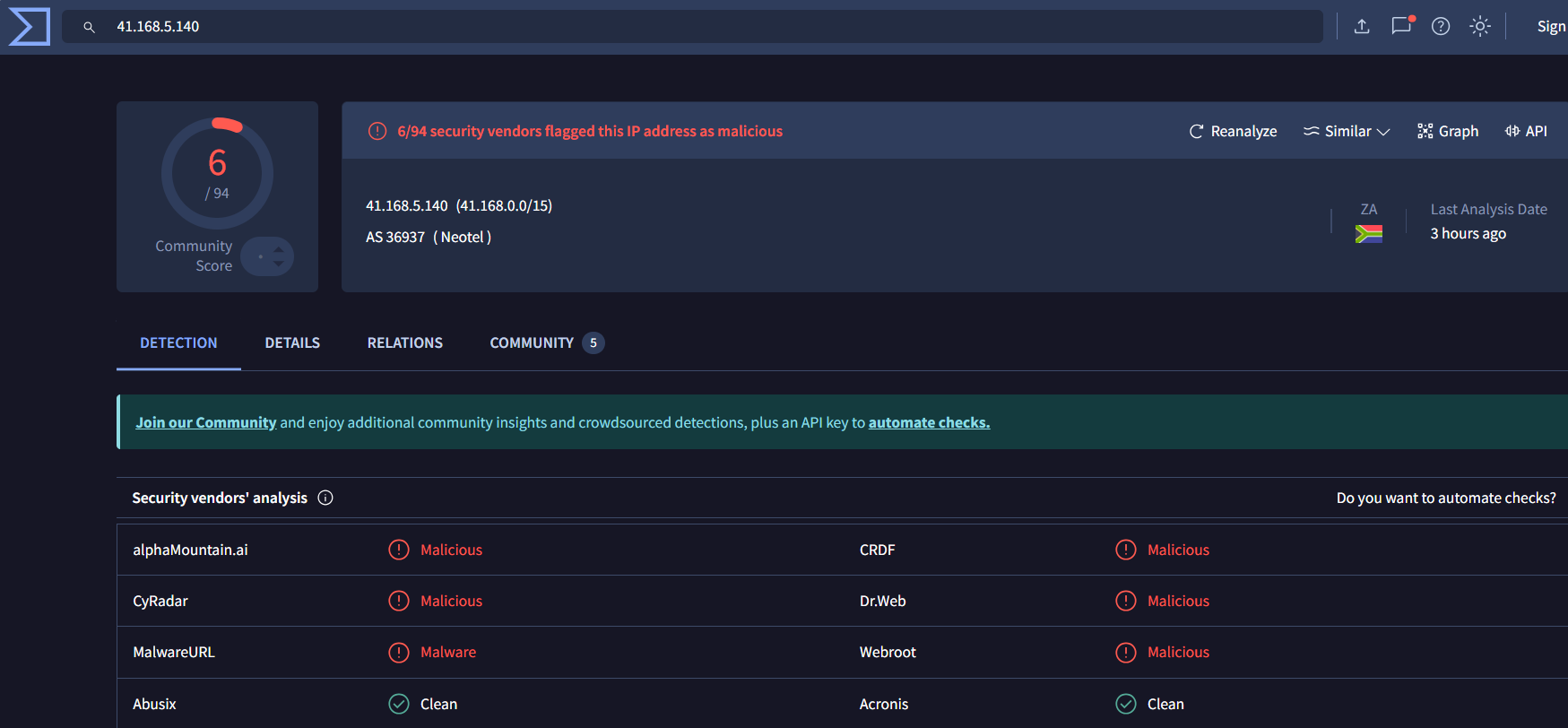
... 125.19.103.198 ... 188.40.0.138 190.81.107.70 ... 210.56.23.100 211.44.250.173 ... 239.255.255.250 41.168.5.140 ... 85.214.204.32
Cross-reference Analysis
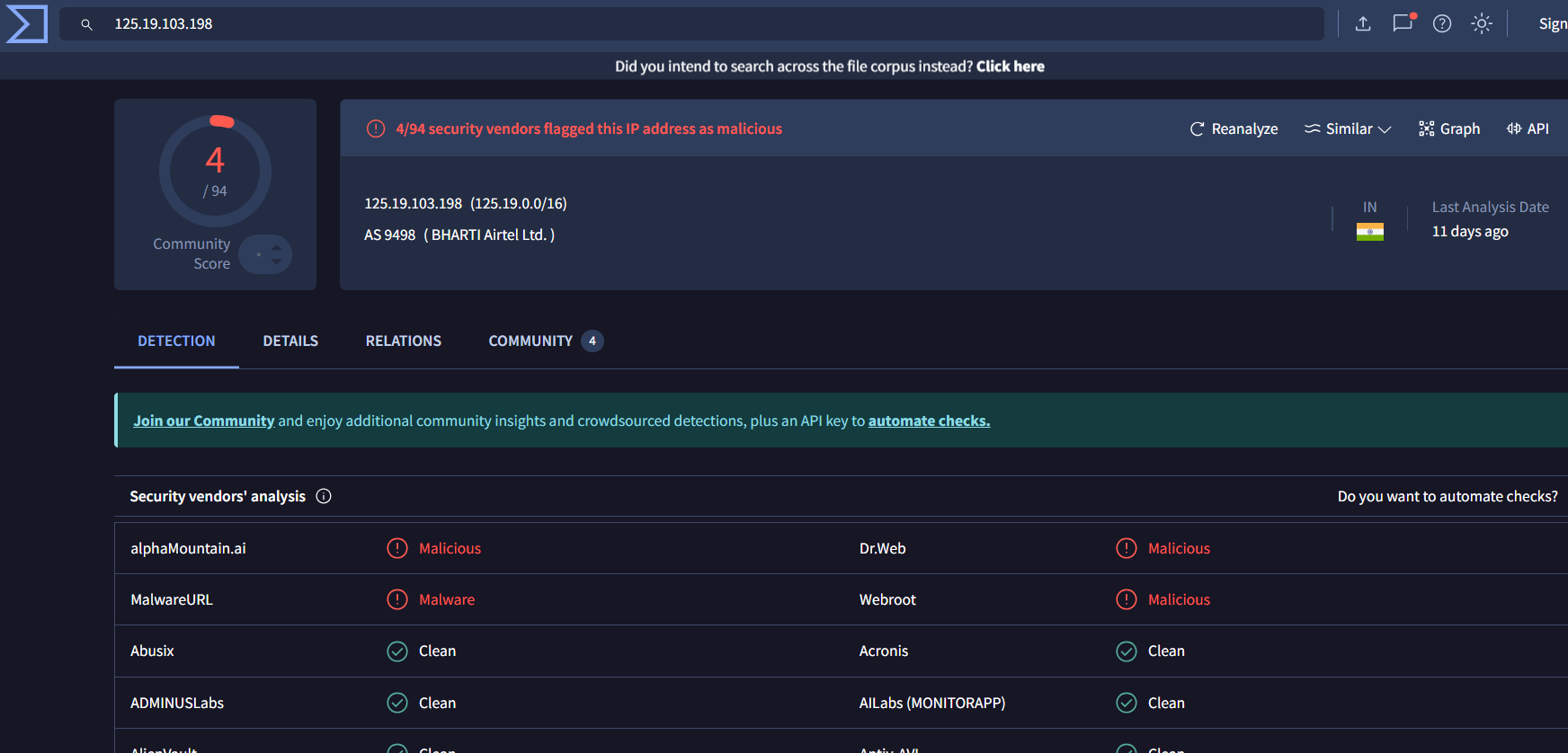
In this section ,we will use two Threat intelligence platform to checkthe IP address(IoC) collected from the evil programs to confirm the typeof the malware.
Virus Total
**AlienVault OTX **
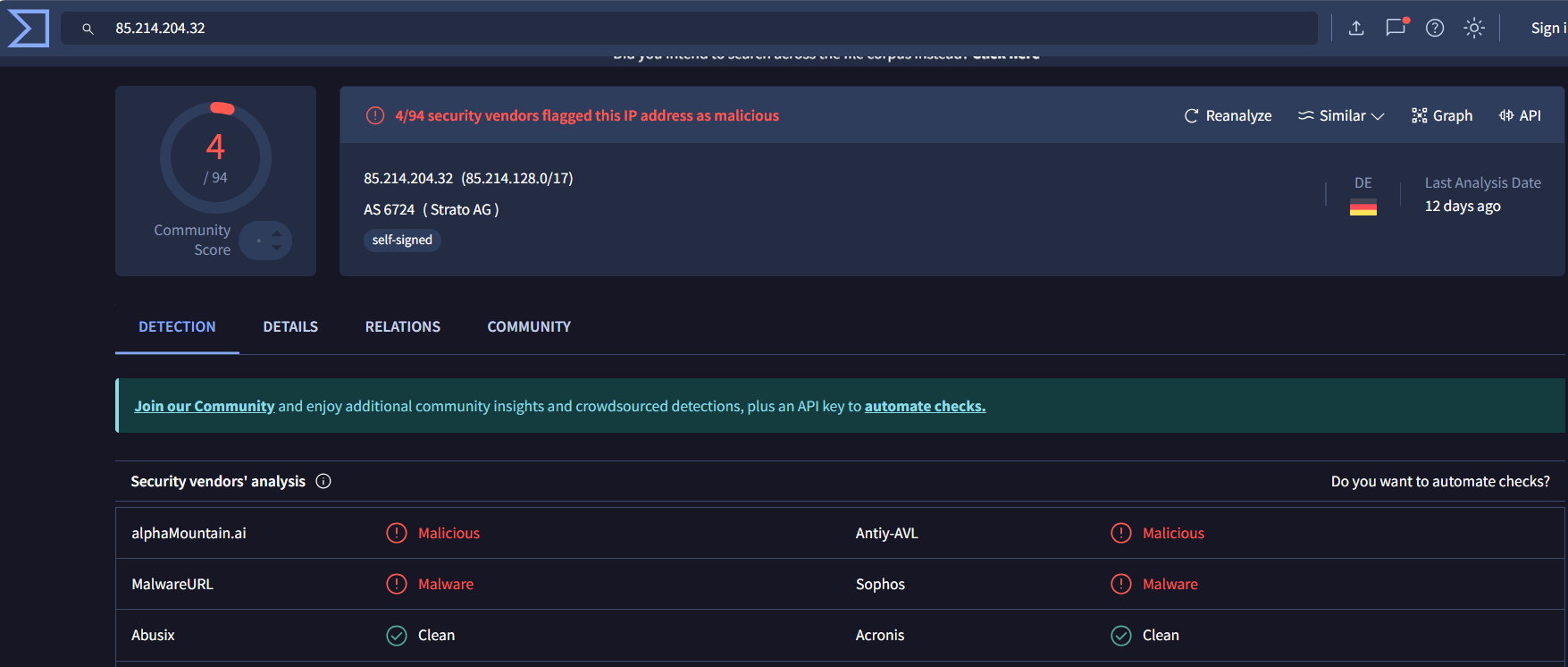



From the results above, we can find that these IP all as Trojan agentand associated with Cridex Trojan.
Real Impacts
Cridex is a quite famous Trojan targeting banks,which was spread widely via spam emails. Once Cridex was planted on aPC, it waited for users to log in to their online banking site andinjected code onto the site to switch in a login form connected to theattackers’ servers. From there, the hackers stole usernames andpasswords and then people’s money.
The UK has been one of the biggest targets of the Cridex, with as muchas £20 million ($30 million) lost. The FBI said at least $10 millionin direct loss domestically could be attributed to Cridex. Given nearly30 countries were targeted, the likely intake of Cridex is beyond $50million.
IoC Input and Output Table
| IoC | Virus Total | AlienVault OTX |
|---|---|---|
| 125.19.103.198 | 4/94 malicious | Worm:Win32/Cridex.E |
| 188.40.0.138 | 2/94 malicious | Unknown |
| 190.81.107.70 | 3/94 malicious | Worm:Win32/Cridex.E |
| 210.56.23.100 | 9/94 malicious | Worm:Win32/Cridex.E |
| 211.44.250.173 | 8/94 malicious | Worm:Win32/Cridex.E |
| 239.255.255.250 | a CnC by ENEMYBOT | Unknown |
| 41.168.5.140 | 6/94 malicious | Unix.Trojan.Mirai-7640640-0, Worm:Win32/Cridex.E |
| 85.214.204.32 | 4/94 malicious | Worm:Win32/Cridex.E |
| f705f59d53d578e c14b5220fecf75a 27b5792b22535bd 0001127e93ac7a11352 |
PEEXE 55/65 malicious Win32:Cridex-N |
Unknown |
Table : Indicators of Compromise (IoC) comparison
IoC Identification and Mitigation
An Indicator of Compromise (IOC) is a pieceof forensic data that suggests an information security system may havebeen breached. IoC commomly contains several types:
1. IP Addresses:
a. Unusual outbound communication to known malicious IPs canindicate a compromised system.
b. Monitoring for unexpected network traffic is an significantmethod of identifying potential breaches.
2. Domain Names and URLs:
a. Access to suspicious or malicious domains/URLs may indicate a C2connection and distribution attempts
b. Combine the white list and black list to restrict the outboundconnection to domain
3. File Hashes:
a. Unique hashes for files can help detect the existence of knownmalware or other malicious programs.
b. Regularly updating hash databases with newly discovered threatsensures that organizations have the most up-to-date information toprotect their systems.
4. Email Addresses:
a. Used in phishing attacks, suspicious email addresses can be avaluable IoC for identifying potential breaches.
b. Use security email gateway to detect and filtrate the suspiciousemails
c. Train employee to have the awareness of identify the phishingemails to protect themselves.
5. Registry Keys:
a. Unusual changes to registry keys can be a sign of systemcompromise.
b. Use EDR or SIEM to monitor the unexpected modifications tocritical system settings can help detect and respond to potentialthreats quickly.
Conclusion
This report analyses an image infected with the Cridex Trojan, which isnotorious malware targeting banks for attacks. From Task 1-4, we mainlyfocus on several attack stages such as: Initial access, Execute,Privileges Escalation and Persistence. During the analysis, we know thatCridex Trojan can siphon users’ bank accounts and PINs by hijacking thewebpage of payment and persist itself by modifying the registry andprocesses injection. Besides, it may turn infected PCs into part of abotnet.
Through the analysis of the malware text content, we found several IoCsand confirmed their malicious intent by searching them from Virus totaland AlienVault OTX. Moreover, within each task, we also discussed somedetection and mitigation mechanisms of these attack stages.
Static analysis is an another strong technique that can help us analysemalware combined with memory analysis, which can show the specific logicand control flow of the code. We could know how malware get theadministrator privilege or how they inject other processes. In thisreport, we do not contain this part, but i really want to practisestatic analysis in the future.