Smart Washing Machine Threat Modeling
Background
The development of IoT and cloud technology are driving thetransformation of people’s lifestyles. Smart cars, smart furniture,smart washing machines and robotic vacuum cleaners can easily becontrolled by users from anywhere at any time, which is quite convenientfor users and provides better experience. However, at the same time,security and privacy threats are overlooked generally. Huge number offlaws are exposed to attackers, security problems such as inappropriatenetwork exposure, unencrypted data transition, weak password and so on,including the compliance violation could cause risks that leak a vastnumber of users’ information or even constitute a botnet that can causelarger chaos in society. In this report, we will analyze security andprivacy threats using STRIDE andLINDDUN model in a scenario where smart washing machineis used at home and provide the corresponding countermeasures.
System Architecture Introduction
Based on home-use washing machine scenario, we draw an architecturediagram to introduce it.
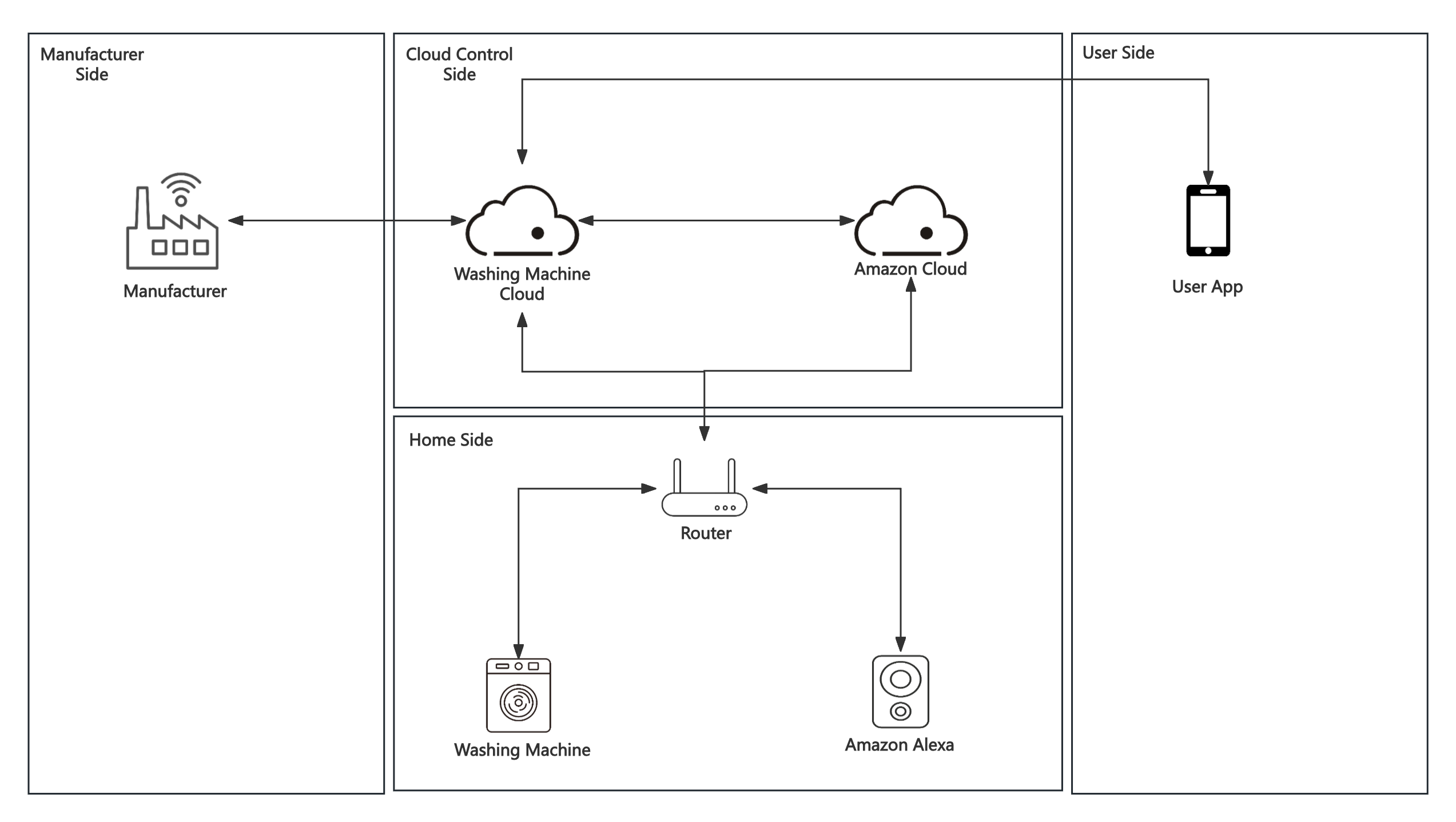
1.Washing machine and Amazon Alexa can connect to the Cloud servers byusing home router, which could let them receive control commands fromoutside.
2.Washing machine manufacture can check machines status and pushfirmware updates through the washing machine cloud.
3.User can control washing machines, such as start, stop, model choiceand so on, by using app, which connects to the Washing Machine Cloud.
4.User can also use Alexa, which is an Amazon smart sound that can becontrolled by voice, to control the washing machine. When user speak thecommand to sound, command can be transmitted to Amazon Cloud service andthen be sent to Washing Machine Cloud by cloud-side interaction, whichcan further control the performance of washing machine.
Data Flow Diagram and Introduction
Based on the architecture diagram before, we can abstract the keyelements (processes data flows and storages) and draw a data flowdiagram to show the significant data flows between these elements.Besides, we draw the trust boundary and administrative boundary, helpingto understand the trust zone and analyze the security and privacythreats among the system.
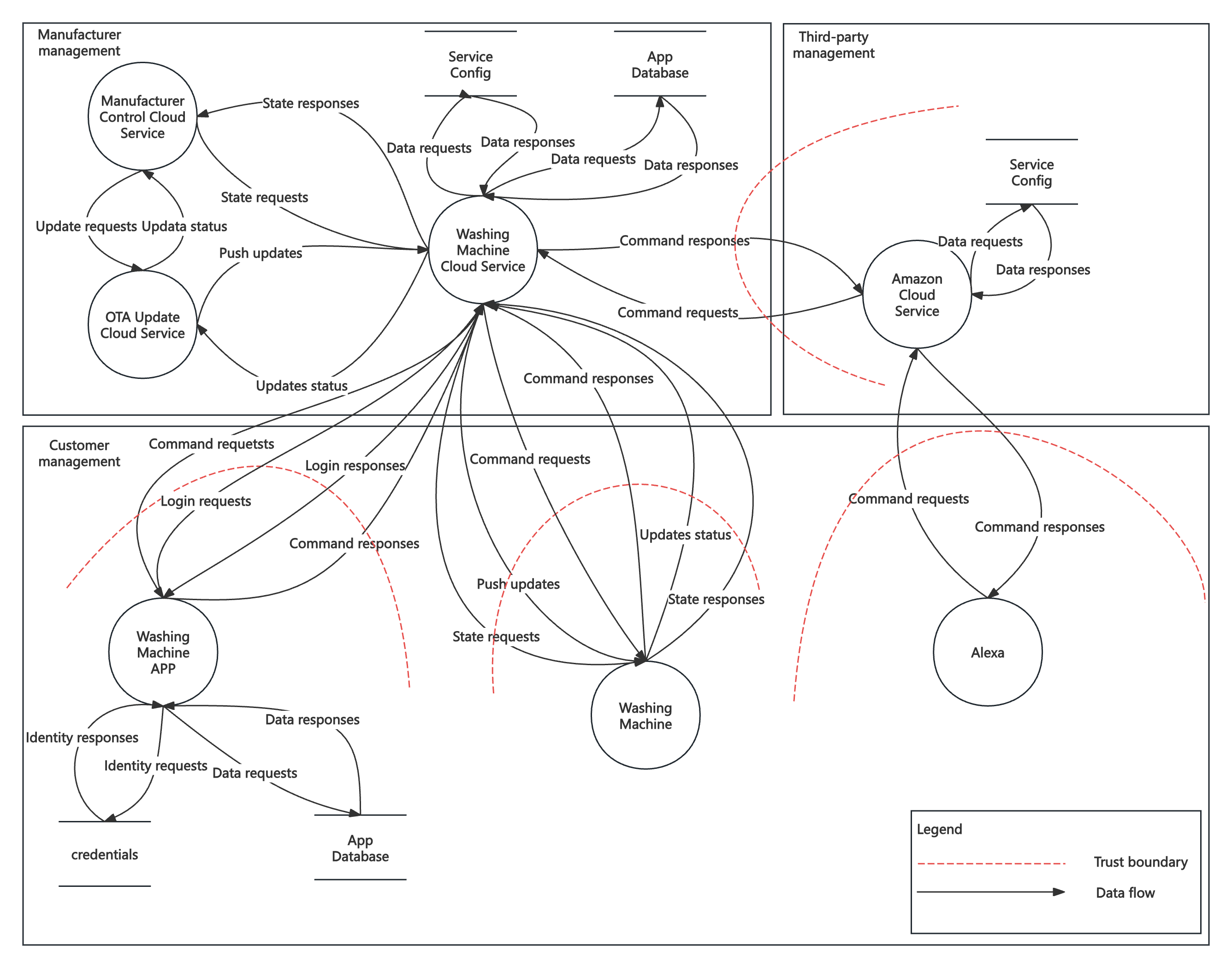
The whole system can be divided into three administrative boundaries:Manufacturer management, Third-party management and Customer management,which demonstrates the division of responsibilities by areas and showsthe possible data transition between different principals. This is thekey point to analyze privacy and compliance threats.
Trust boundaries are demonstrated by red dotted lines, illustrating theboundary between different security control policies and trust levels,which is the key point to analyze security threats.
Unlike the previous architecture description, in manufacturer managementarea, cloud services are divided into three parts: control service,update service and washing machine service, though they belong to onetrust boundary. The control service can trigger update service to sendfirmware update to washing machines.
Threat Modeling and Analysis
In this part, we will implement threat modeling towards the data flowdiagram before to analyze the security and privacy threats based onSTRIDE and LINDDUN, which are two famous threat analysis models.
First, we will introduce these two models, and then we will list all thepossible threats and map them to these models. Finally, we will discussthese threats in an easy-to-understand way.
Threat models introduction
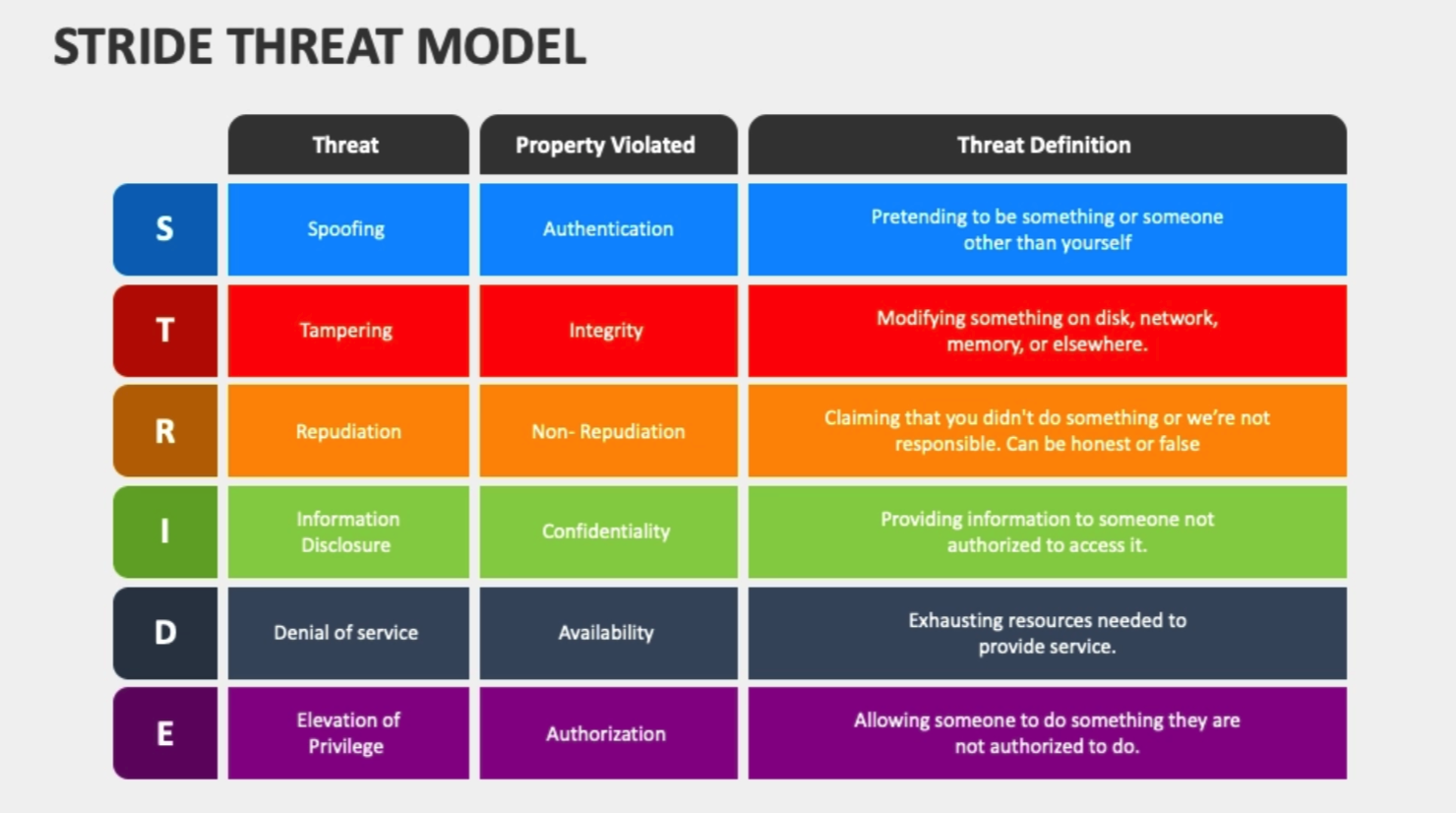
The following picture is the description of meaning of STRIDE model,which can be separated into six parts: Spoofing, Tampering, Repudiation,Info disclosure, Denial of service and Elevation of privilege.
These six parts are a highly abstraction of cyber-attack ways, which canbe used as a mindset to analyze the possible security risks of a system.
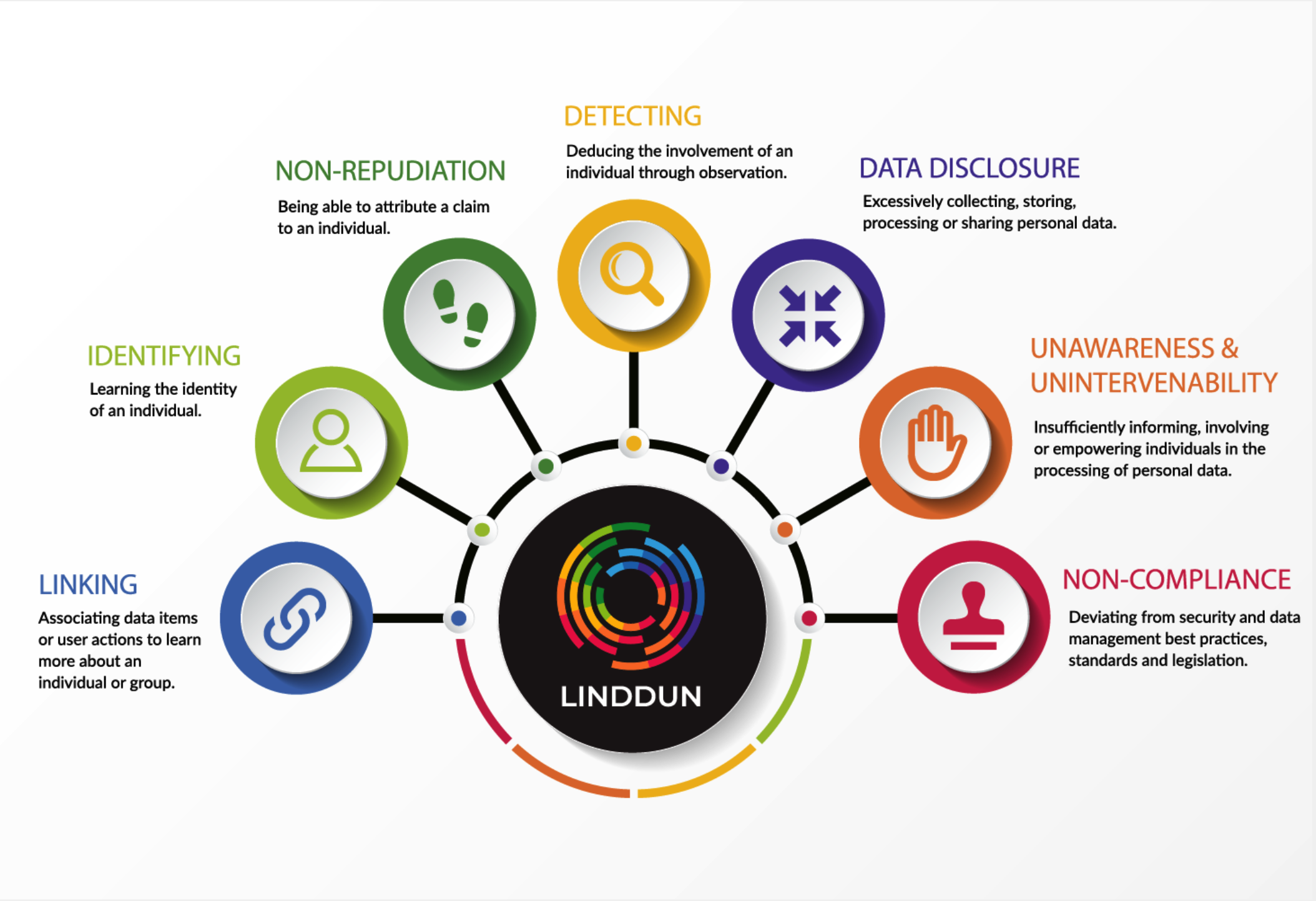
The following picture shows the description LINDDUN. The acronym LINDDUNrepresents 7 main threat types in privacy: Linking, Identifying,Non-repudiation, Detecting, Data disclosure, Unawareness &Unintervenability and Non-compliance, which could help us think aboutprivacy concerns in systemtic and structured way.
Threat analysis
This part, we will perform a holistic threat analysis to the home-usewashing machine scenario based on the STRIDE and LINDDUN models. Wetotally list 10 types of threats in the table 1, and the detaileddescriptions and discussions are below the table.
| Threat | Threat Name | Model Mapping |
|---|---|---|
| 1 | App username and password brute-forcing | Spoofing, Detecting |
| 2 | App over-collects customers’ information without notification | Unawareness & Intervenability, Compliance |
| 3 | Lack of encryption between App and Cloud Service | Spoofing, Tampering, Info Disclosure, Linking, Identifying, Data Disclosure |
| 4 | Lack of authentication or authorization between App and Cloud Service | Spoofing, Tampering, Info Disclosure, Elevation of Privilege, Data Disclosure, Unawareness, Non-compliance |
| 5 | Lack of authentication between Washing Machine and Cloud Service | Spoofing, Non-compliance |
| 6 | Lack of signature and integrity verification during the OTA (Over the Air) update | Spoofing, Tampering |
| 7 | Lack of signature between Amazon and Washing Machine Cloud Service | Spoofing, Tampering |
| 8 | Manufacturer Cloud Services expose unexpected sensitive services | Spoofing, Tampering, Elevation of Privilege |
| 9 | Manufacturer Cloud Service lacks DDOS protection | Denial of Service |
| 10 | Manufacturer Cloud Service lacks necessary service logs | Repudiation |
Threat 1: App username and password brute-forcing
Scenario description: When login to the washing machine app,the attacker can enumerate usernames and passwords, at the same time,observing the system responses to determine whether the user exists andwhat the corresponding password is.
Threat mapping: Spoofing, Detecting
Threat discussing: When the app does not limit the frequency of thelogin attempts based on devices fingerprints and response excessiveinformation, this kind of threat can happen. Attacker can login thesystem using guessed username and password and spoof a legitimate user.Even attacker can not login successfully, with the excessive informationlike “The user exists but wrong password”, attackers can make sure thatthis user are using this app, which violates the privacy principle ofunobservability.
Threat 2: App over-collects customers’ information without notification
Scenario description: App collect users’ location informationin real time, but users even do not know.
Threat mapping: Unawareness & Intervenability, Compliance
Threat discussing: Customers’ must have the right to know and refusetheir personal information collection and use. If they do not know, thiscondition has violated the content awareness and compliance
Threat 3: Lack of encryption between App and Cloud Service
Scenario description: When communication between App andCloud Service does not have proper encryption, attackers can implementMITM(Man-in-the-Middle) attack, which can sniff all the informationtransmitted and can even make some changes to the commands.
Threat mapping: Spoofing, Tampering, Info Disclosure, Linking,Identifying, Data Disclosure
Threat discussing: Attackers can get all information from thecommunication, so if customers personal information is being sent, suchas phone number, home address, username, password, email, commands andso on, that will be a big information disclosure, which violateconfidentiality. Attackers can do anything they want; they can spoofcustomers to send command and tamper any command that customer send.Besides, they can know who you are based on this information, whichviolates anonymity & pseudoanonymity principle. Then, if thegeographical location is sent, they can combine them with the map tolocate which community you are living in and even the specific building,which violate the unlinkability principle.
Threat 4: Lack of authentication or authorization between App and Cloud Service
Scenario description: When the interface lacksauthentication, attackers can send any request without any loginprocess; When the interface lacks authorization, attackers just need alogin process, but do not need to bind the washing machine, so they cansend command to any existing machine.
Threat mapping: Spoofing, Tampering, Info Disclosure, Elevation ofPrivilege, Data Disclosure, Unawareness, Non-compliance
Threat discussing: In this scenario, attackers can deceive serverthat they have privileges even higher privileges and then tampercommands or get sensitive information, which cause informationdisclosure, violating confidentiality. They can play as another customerto control other machines. Besides, the real customer can not awarethese actions, which violates content awareness privacy principle andpolicy and consent compliance.
Threat 5: Lack of authentication between Washing Machine and Cloud Service
Scenario description: When communication between WashingMachine and Cloud Service does not have proper authentication orauthorization, attackers can pretend to be the server to send commands.
Threat mapping: Spoofing, Non-compliance
Threat discussing: In this scenario, attackers can deceive washingmachine that they are servers and then send commands, which violatesauthentication security principle. . Besides, the real customer can notaware these actions, which violates least-privilege principle andcompliance.
Threat 6: Lack of signature and integrity verification during the OTA update
Scenario description: Attackers can make changes to the patchfiles during the transit. If the washing machine does implementintegrity verification, this evil patch can be installed to thefirmware, which could let attacker fully control the washing machine.
Threat mapping: Spoofing, Tampering
Threat discussing: Attackers need to change files during this kindof attack, so this violates integrity security principle. Besides, ifthe washing machine lacks integrity verification to the patch file,attackers can deceive washing machine that this file is coming from theofficial server, which violates authentication security principle.
Threat 7: Lack of signature between Amazon and Washing Machine Cloud Service
Scenario description: If the communication between them lackssignature, attackers can send forged requests to the Washing MachineCloud Service to pretend to be the Amazon Cloud Service.
Threat mapping: Spoofing, Tampering
Threat discussing: The communication between two different systemscannot use account to identify the identity, but signature can be thebest solution. Without signature, attackers can easily change or sendany request by themselves, which violates authentication and integritysecurity principles.
Threat 8: Manufacturer Cloud Services expose unexpected sensitive services
Scenario description: Manufacturer Cloud Services may exposesensitive ports to external network, such as 22(SSH), 80(HTTP),443(HTTPS), 5900(VNC) and so on, which could give attackersopportunities to control the whole network and break the trust chain. Atthat time, attackers can send any command to any device and change patchfiles from origin.
Threat mapping: Spoofing, Tampering, Elevation of Privilege
Threat discussing: The washing machine control services should onlyopen to the internal network to let engineers operate the system. If itopens to external network, it means that anyone can access it, whichviolates least-privilege security principle.
Threat 9: Manufacturer Cloud Service lacks DDOS protection
Scenario description: Attackers can use botnet to send alarge volume of network traffic to attacks Manufacturer Cloud Services,which could interrupt the cloud services.
Threat mapping: Denial of Service
Threat discussing: Denial of Service can make a big chaos in thewhole society, because all the smart washing machine cannot be usedduring the attack, which violates the availability security principle.
Threat 10: Manufacturer Cloud Service lacks necessary service logs
Scenario description: Without necessary server operationlogs, attackers can make some critical changes in services, but nobodycan know who did these changes.
Threat mapping: Repudiation
Threat discussing: Without necessary server operation logs, securityengineers cannot do some forensic works to analyze who did the anomalyactions, which violates non-repudiation security principle in STRIDE.
Technical Countermeasures
In this part, we will mainly talk about the countermeasures we shouldtake towards the threats that we have analyzed before.
Threat 1: App username and password brute-forcing
Technology solution:
(1) Return the same error message, like “Username or password iswrong”, even just username or password wrong to stop the usernameenumeration.
(2) Use robot-check SDK to stop the brute-forcing attack
(3) Use MFA to avoid the scenario that attackers try to login usingguessed right username and password.
Refactoring cost: Need to change the logic of login module, installnew SDK and use MFA.
Threat 2: App over-collects customers’ information without notification
Technology solution: Only collect necessary information fromusers and describe why we collect this information in the consent.
Refactoring cost: Need to review information collected and removeunnecessary field and change the consent content.
Threat 3: Lack of encryption between App and Cloud Service
Technology solution: Use HTTPS as the communication protocolto ensure the encryption.
Refactoring cost: Need to change the communication protocol to HTTPSin source code.
Threat 4: Lack of authentication or authorization between App and Cloud Service
Technology solution: Ensure each API interface has the properauthentication and RBAC authorization.
Refactoring cost: Need to change the configuration of the APIGateway and the source code logic of each interface.
Threat 5: Lack of authentication between Washing Machine and Cloud Service
Technology solution: Washing machine should verify thecertificate of the Cloud Service and negotiate the key.
Refactoring cost: Cloud Service should apply a certificate from aCA, and let the Washing Machine trust this CA.
Threat 6: Lack of signature and integrity verification during the OTA update
Technology solution: Patch file should attach a signature,and when the Washing Machine install the patch, it should verify thevalidity of the signature.
Refactoring cost: OTA update Cloud Service should apply acertificate from a CA and sign every patch file using its private key.Let the Washing Machine trust this CA and use the public key incertificate to verify the file.
Threat 7: Lack of signature between Amazon and Washing Machine Cloud Service
Technology solution: When Washing Machine Cloud Servicereceive the requests from Amazon Cloud Service, Washing Machine CloudService verify the signature from the Amazon.
Refactoring cost: Config Washing Machine Cloud Service to get thepublic key from a trusted interface provided by Amazon and verify thesignature of requests.
Threat 8: Manufacturer Cloud Services expose unexpected sensitive services
Technology solution: Stop all ports exposed to externalnetwork and only all the access from internal network.
Refactoring cost: Config the VPC ACL or the ECS security group.
Threat 9: Manufacturer Cloud Service lacks DDOS protection
Technology solution: Add the DDOS protection to the network,such as CDN, traffic scrubbing and so on.
Refactoring cost: Buy the security service such as CDN, DDOSprotection form cloud provider.
Threat 10: Manufacturer Cloud Service lacks necessary service logs
Technology solution: Add service logs to the necessaryfunctions, such as OTA update, command and control.
Refactoring cost: Add log printing and storage logic to the sourcecode of services manually.
UK Code of Practice Analysis
In this section, we will analyze some UK Code of Practice to mitigatethe threats above.
British National Cyber Security Centre (NCSC) published a Code ofPractice for Consumer IoT Security, whichprovides practical steps for IoT manufacturers to improve the securityof consumer IoT products. This practice provides thirteen guidelinescontributing to protecting customers’ security and privacy.
The following picture shows the thirteen guidelines.
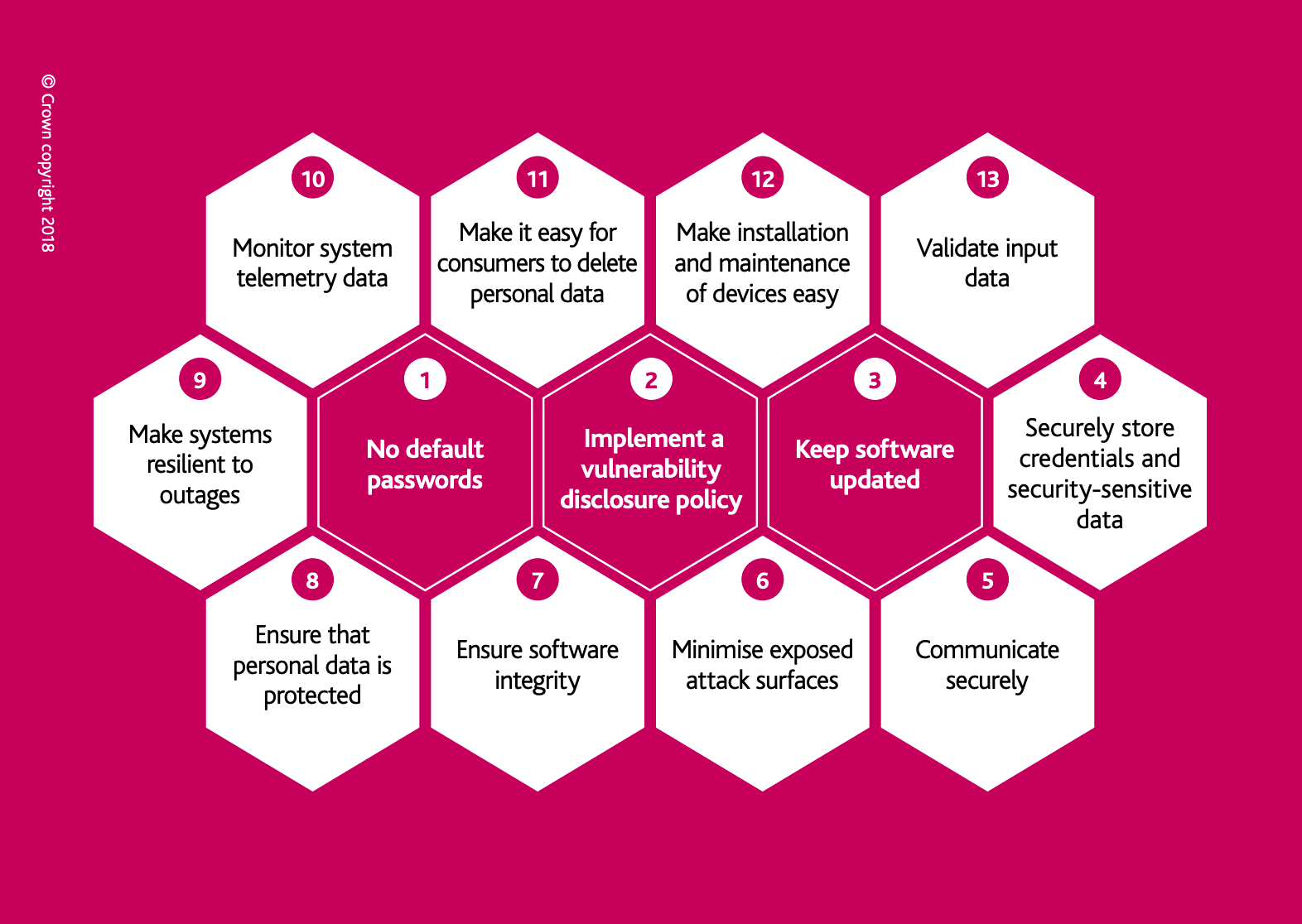
Practice 2: Implement a vulnerability disclosure policy
Solve problems: Threat 1,2,3,4,5,8
Analysis: This policy allows security researchers and others toreport issues, which means that most of the application securityproblems and network traffic security problems can be found by them.
Practice 5: Communicate securely
Solve problems: Threat 3,4,5,7
Analysis: This policy means that the communication through thenetwork should have security mechanism such as encryption, signature,authentication and authorization.
Practice 6: Minimize exposed attack surfaces
Solve problems: Threat 8
Analysis: This policy means that do not expose unnecessary servicesto the external network
Practice 7: Ensure software integrity
Solve problems: Threat 6
Analysis: This policy means that we should monitor any unwantedchanged to devices, such as anomaly OTA update.
Practice 8: Ensure that personal data is protected
Solve problems: Threat 3,4
Analysis: This policy means that we need to ensure the personal datawill not be leaked from the servers or during the communication.
Practice 9: Make system resilient to outages
Solve problems: Threat 9
Analysis: This policy means that the system’s availability cannot beinfluenced by the DDOS or any other incident.
Practice 10: Monitor system telemetry data
Solve problems: Threat 10
Analysis: This policy means that we need to monitor and collect allthe necessary system log data to contributing to the security analysis.
Practice 11: Make it easy for costumers to delete personal data
Solve problems: Threat 2
Analysis: This policy means that we should give customers the fullcontrol of their personal data, including collection acknowledge anddeletion right.
Practice 13: Validate input data
Solve problems: Threat 1,4,5,6,7
Analysis: This policy means that every input from outside should beverified the legitimacy, which can stop the threats such asauthentication, authorization, signature and so on.\Based on analysis above, we could see that we can successfully solve allthe threats that we have analyzed before using this UK Code of Practicefor Consumer IoT Security.
Comprehensive Comparison of Multi-Country Regulations
In this section we will discuss other regulations in IoT security area,such as Europe and USA.
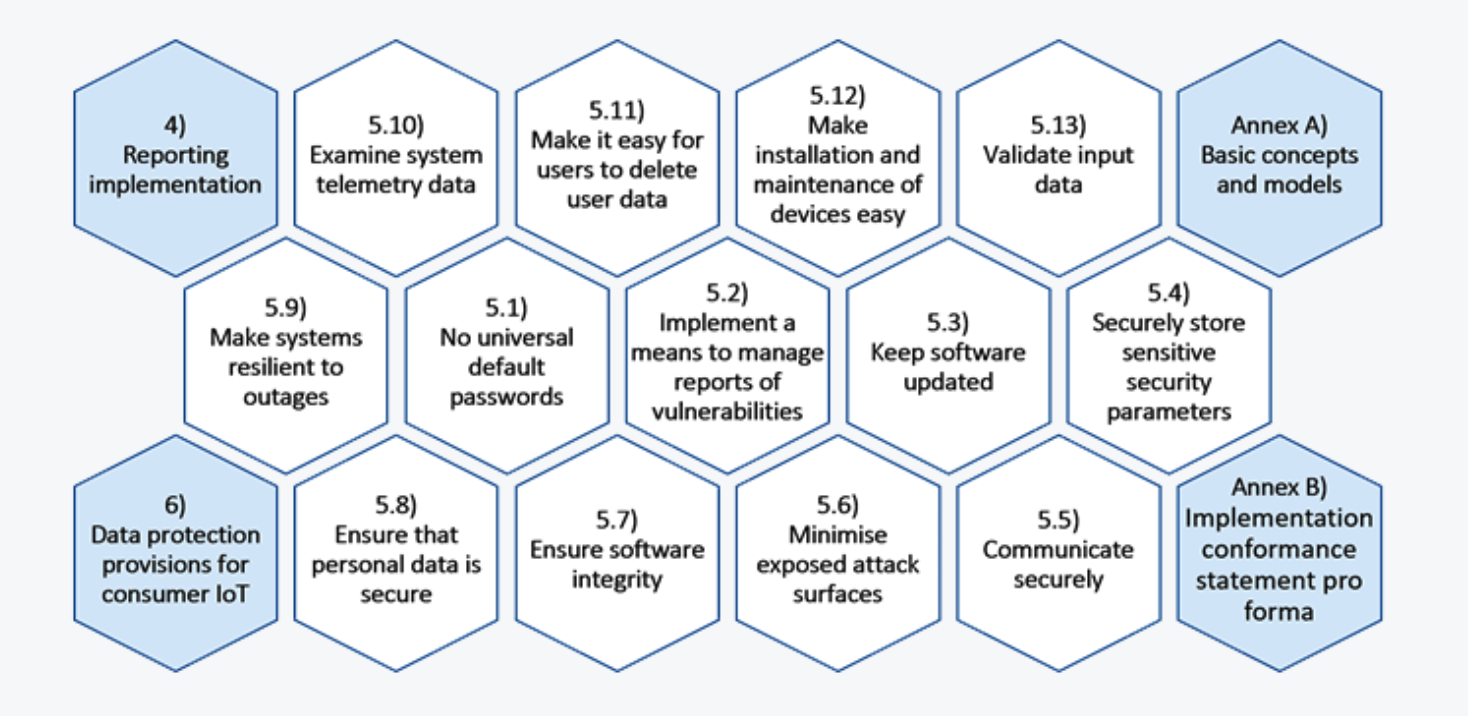
The following picture shows the ETSI EN 303 645standard, which is European standard for customerIoT. It has thirteen principles same as the standard in UK.
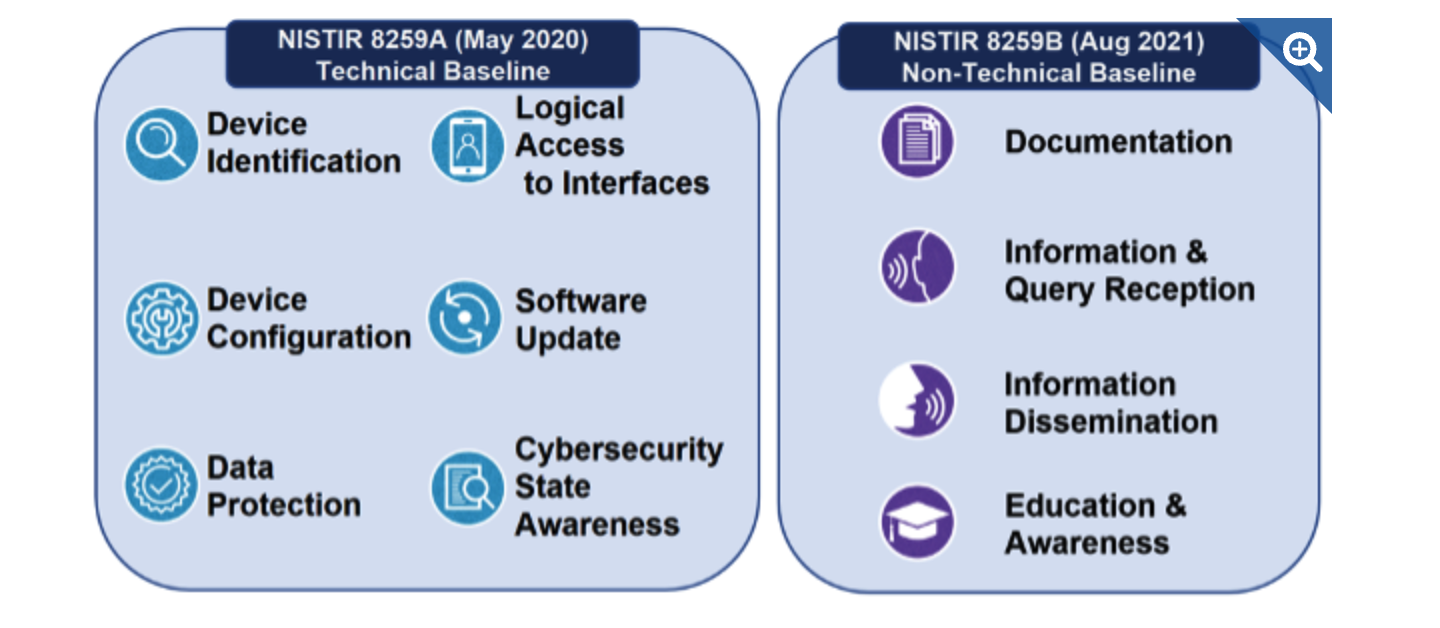
The following picture is the USA NIST IR 8259 seriesstandard, which identifies the securitybaseline of the IoT devices.
The UK, EU, and US have all introduced IoT security standards, but theydiffer in focus, scope, and level of technical detail.
The UK’s Code of Practice for Consumer IoT Security was one of theearliest frameworks. It is policy-oriented and aimed at manufacturers ofconsumer IoT devices. It outlines 13 high-level security principles,such as avoiding default passwords, ensuring devices can be updated, andproviding vulnerability disclosure mechanisms. The language is simple,making it suitable for policymakers and product managers. For example,it recommends avoiding default passwords but doesn’t specify how toimplement that technically.
The EU’s ETSI EN 303 645 builds on the UK’s principles with moretechnical depth. It includes the same 13 principles and adds fiveadditional recommendations focused on data protection. It not only bansdefault passwords but also requires each device to have a uniquecredential or force the user to set one during initial setup. ETSI alsoincludes privacy-related measures like data minimization, user controlover data, and secure deletion mechanisms. This makes it more suitablefor engineers and technical implementation, and it has been adopted inseveral countries as an official standard.
The US NIST IR 8259 series is more focused on technical baselines andsystem integration, especially in enterprise and government procurementcontexts. It defines key security functions such as device identity,secure configuration, update mechanisms, logging, and data protection.While it also discourages default passwords and supports secure updates,it puts greater emphasis on configurability and audit logging. Forexample, while the UK mentions that devices should be updatable, NISTgoes further by requiring update integrity checks and rollbackcapabilities.
In addition, the UK’s framework is now legally enforced through the PSTIAct. The EU is moving in the same direction with its upcoming CyberResilience Act (CRA). In contrast, NIST standards are not mandatory forthe general market but are required for federal procurement and widelyreferenced in industry.
In summary, the UK standard provides policy direction, the EU standardsupports technical implementation, and the US standard focuses onenterprise-level integration. Each reflects different regionalpriorities for securing consumer IoT devices.
Conclusion
In this report, we analyze and list 10 primary security threats ofhome-use washing machines and provide corresponding technology andpolicy countermeasures. At the same time, we implement comprehensivecomparison analysis for regulations of customer IoT security in UK, EUand USA.