Electric Vehicle Charging Threat Modeling on Smart Grid
Background
This article is part of my ICS security research and analyzes the security risks in smart car scenarios based on the following background research.
Abstract
The rapid development of the electric vehicle industry promotes theinstallations of the private and public EVCS (Electric Vehicle ChargingStation). This kind of equipment connect critical infrastructure such asthe power grid and transportation, which makes them become an importantfactor of the whole society. It is also because of its diversity ofconnections and functions such as cloud management services, third-partyservices, electric vehicle and power grids, which makes it morevulnerable to various types of cyber-attacks and can cause significantsocial impacts. In this paper, we systematically analyze the security ofEV charging systems in a smart grid environment, with a focus on theimpact of attacks on the grid.
Introduction
Governments worldwide are prioritizing climate change, driving rapid EVmarket growth. Smart transportation is a keyagenda, with European and American policies promoting EV adoption andphasing out full-powered cars. To meet rising demand, EVCSs areexpanding quickly.
The ecosystem’s interaction with multiple services and protocolsincreases complexity and attack surfaces. Charging equipment suppliersintegrate various technologies, enabling remote management,user-friendly services, and energy scheduling. CMS (Cloud ManagementServices) allows mobile-controlled charging, increasing spoofing andtampering risks. Third-party services like navigation and billing handlepersonal data, heightening exposure to informationleaks.
While suppliers focus on functionality, security is often overlooked,leading to vulnerabilities in APPs, firmware, and communications.Meanwhile, power grids, as critical infrastructure, face risks fromcoordinated EV charging and dischargingattacks.
In this paper, we focus on a basic architecture of the public and homeEVCS, and analyze its risks from different aspects such ascommunication, firmware, application, supply chains, physical devices,Etc. We also provide some detection methods and mitigation measures ofeach attack.
The remainder of this article is organized as follows. In Section 2, weintroduce the charging ecosystem architecture and some basic concepts.In Section 3, we conduct risk analysis and illustrate the possibleimpacts of attacks based on the system we describe in Section 2. InSection 4, we provide some methods for detection and describe where theyshould be deployed within the system. In Section 5, we discuss somesecurity measures to defend against these attacks and. In Section 6, wediscuss some measures for enhancing system resilience and makeconclusion in In Section 7.
System Architecture and Analysis
System architecture
The following figure are drawn based on the description of case study.
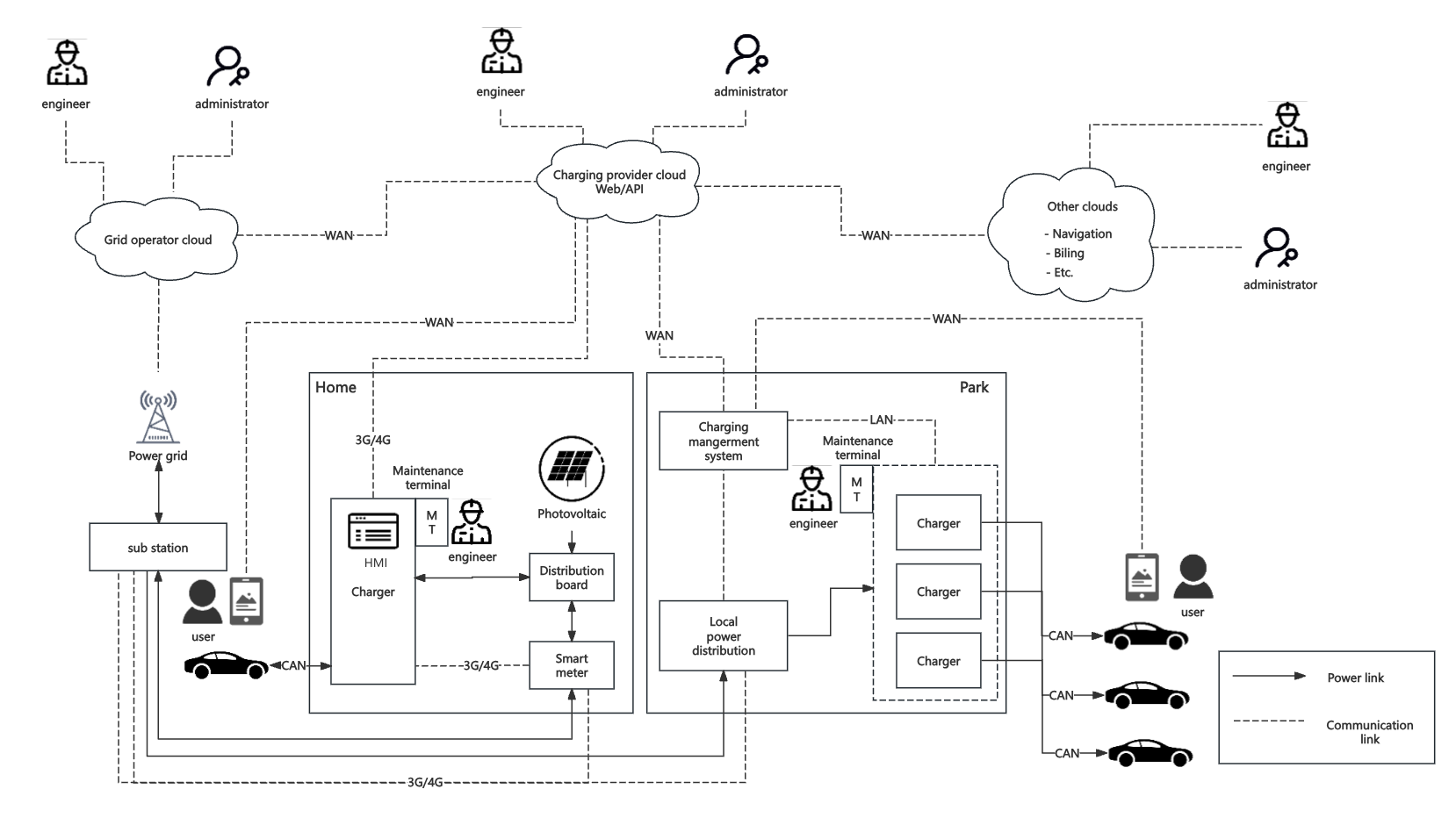
The whole ecosystem can be divided into three parts:
1.Cloud services (Grid cloud, charging cloud and other clouds): Provide services of data storages and data communication and mobilemanagement and control from the applications.
2.Power grid: Maintain the power supply to the EVCSs.
3.EVCS: Supply power to EVs, authenticate users and cars and recordpower usage.
Procedure analysis
In this part, we will discuss the work procedure of this system.
From Home EVCS:
1. User registers and logins to the charger app deployed in thecharging provider cloud and bind the car with the EVCS equipment.
2. User plugs the cable in the car, which can transmit the carinformation by VIN code over the CAN protocol.
3. User starts charging by APP then power comes from distribution boardand can be metered by the smart meter.
4. Smart meter can have communication with the EVCS equipment and thepower substation to transmit the meter record.
5. Distribution board can switch the power source to the photovoltaicpanel or feed excess electricity back into the power substation.
6. EVCS equipment can communicate with the charger provider cloud tosynchronize information and states.
7. Maintenance engineers can access the EVCS equipment with the accessinterface on the equipment locally.
8. Operation engineers and administrators can access the cloud platformto manage the charging cloud system.
From Park EVCS (only discuss differences with the home EVCS):
1.User registers and logins to the charger app deployed in the chargingmanagement system and navigate a free EVCS equipment and can pay thebill by the app.
2.Park has a local power distribution station, which supply the power toall the charger equipment and meter the power usage of each EVCSequipment.
3.Local power distribution station communicates with the chargingmanagement system to synchronize the power usage.
4.Charging management system communicates with EVCS equipment to controlthe start and stop of charging and synchronize the equipment states.
5.Charging management system communicates with charger provider cloud tosynchronize chargers’ information.
6.Operation engineers and administrators can access the cloud platformto manage the third-party system
Threat Analysis
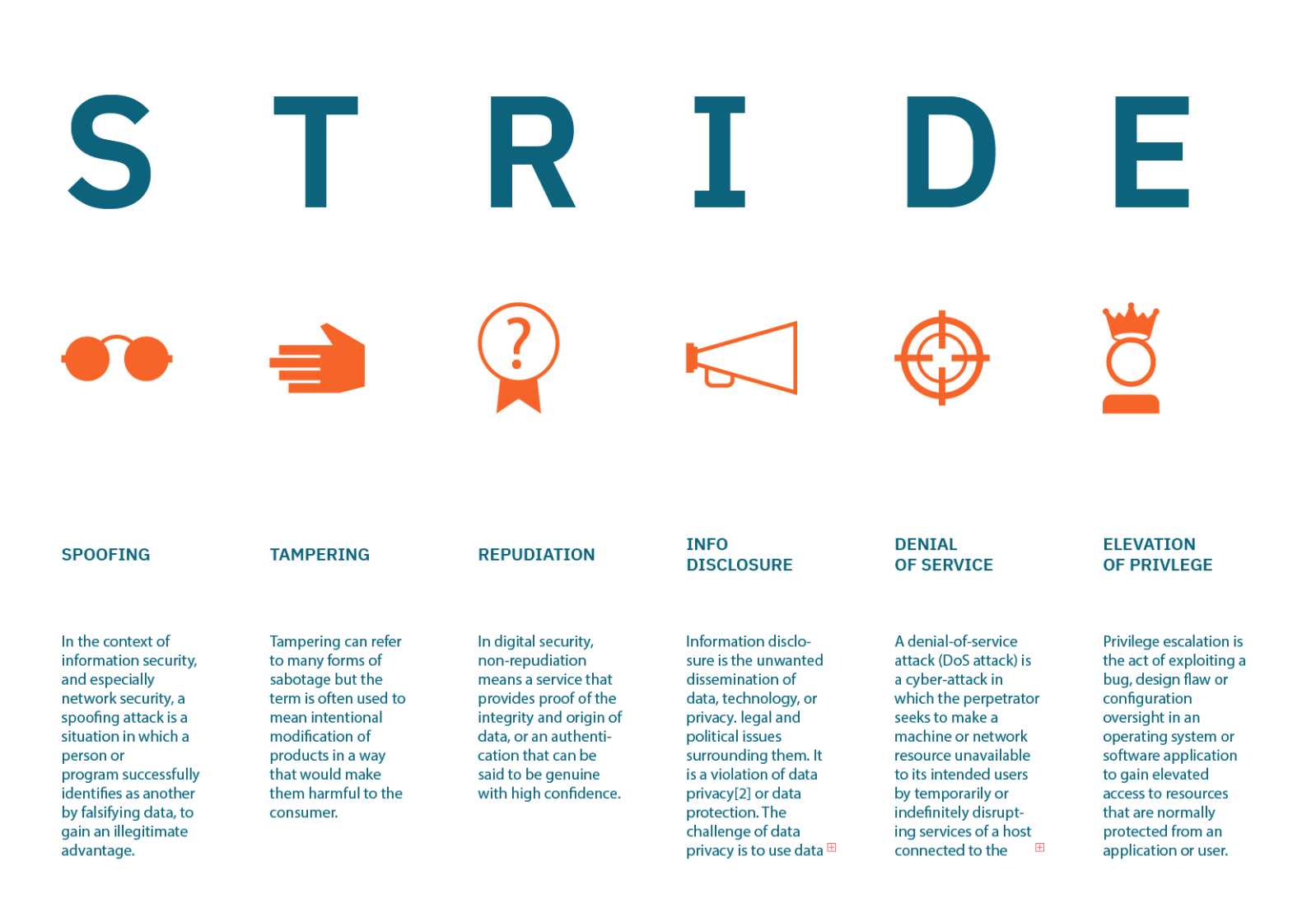
In this section, we will conduct the threat analysis focusing on keyfactors of this ecosystem such as applications, firmware andcommunication, and include physical and human factors even the threat ofthe power grids based on the STRIDE threatmodeling
The following picture is the description of meaning of STRIDE modeling,which can be separated into six parts: Spoofing, Tampering, Repudiation,Info disclosure, Denial of service and Elevation of privilege.
Data flow diagram
To clearly present the data interaction model of the entire ecosystem,making it convenient for us to analyze risks in specific scenarios, weabstract various elements and services in Figure 1, and draw them as thefollowing data flow diagram, where red represents core services and bluerepresents core elements.
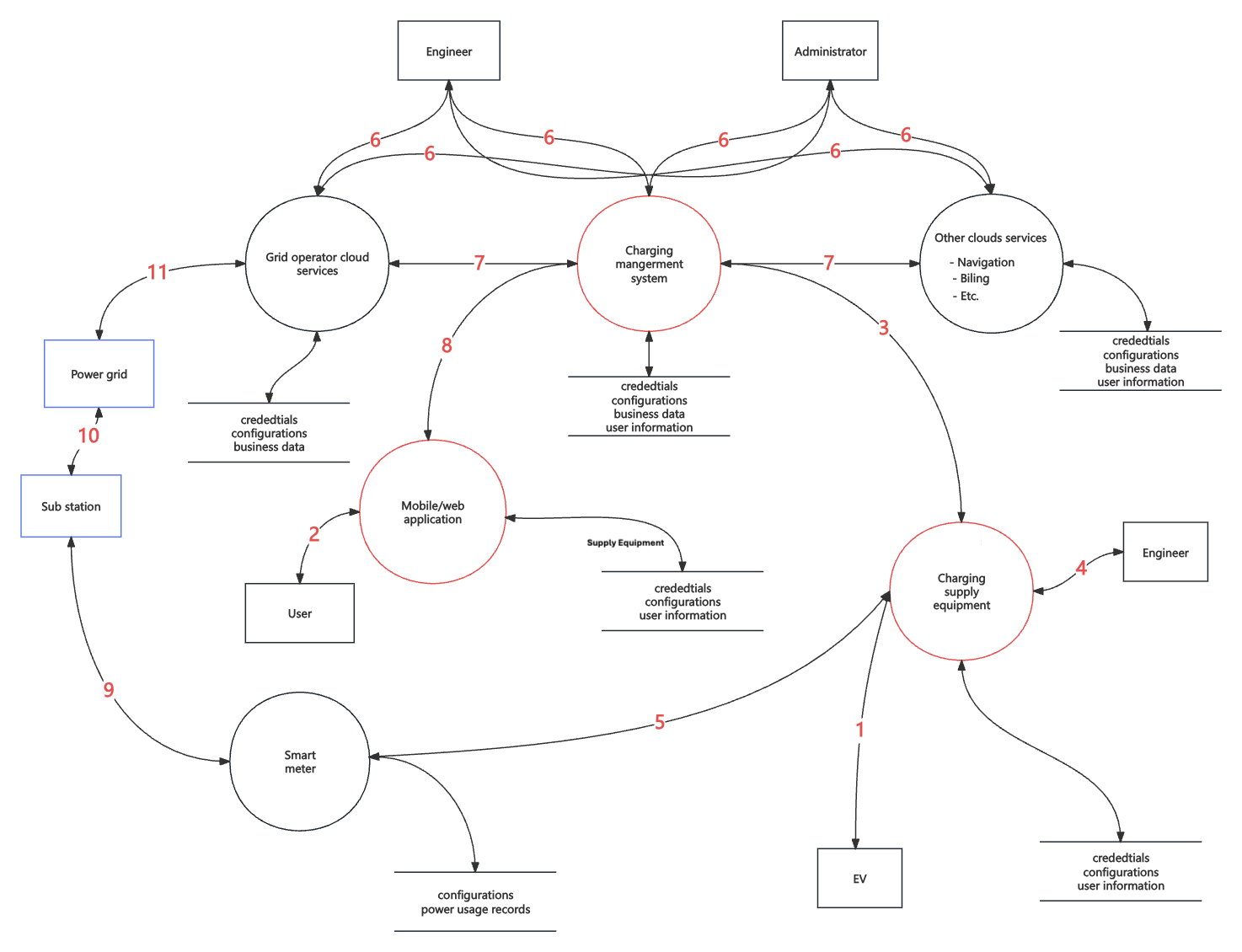
External entities: We use rectangles to represent the externalentities, such as users, maintainers and electric vehicle, who interactwith processes.
Processes: We use circles to represent the processes, includingmobile application, charging provider cloud service, charging managementsystem, charger embedded system and so on, which provide various kindsof services to external entities or interact with them.
Data stores: We use double horizontal lines to represent database,storing data that come from business.
Data flow: We use arrows to represent data flow, and the pointing ofarrows represent the direction of the data flow.
Risk scopes
Due to the complexity of the whole ecosystem, in order to clearlyexpress the risks, we divide risks into different scopes as follows:
(1) EV to CSE (Charging Supply Equipment) interfaces: Thecommunication between the EV and the charging embedded system.
(2) User to EV mobile/web application: The EV user uses thisapplication to navigate, control and pay for the charge.
(3) CSE to CMS (Charging management system): The communicationbetween the Charging Supply Equipment and the Charging managementsystem.
(4) CSE maintenance interface: The interfaces (USB, serial ports, orother physical ports) on the CSE, used by engineers to debug or test theequipment.
(5) CSE to SM (Smart meter): The communication between chargingSupply Equipment and smart meter.
(6) Cloud services management interface: The web interfaces of cloudservices (charging provider operator service or third-party cloudservices), used to manage and config the cloud services.
(7) Cloud to Cloud interfaces: The communication between differentcloud services, such as API requests or software download.
(8) EV mobile/web application to cloud services: The communicationbetween cloud services and EV mobile application.
(9)Smart meter to substation: Smart meters report meter recodes tothe substation.
(10)Substation to power grid: Power grid monitor the states of thesubstations.
(11)Grid operation cloud to power grid: Grid operation cloud cancontrol and monitor the power grid remotely.
Risk analysis
Remote charging session hijacking
1.Scenario: Due to the mobile application’s failure to verifyuser ownership of the target vehicle during charging requests and onlychecking whether the user is a legitimate system user, attackers cancontrol valid accounts and attempt unauthorized charging and dischargingoperations on vehicles not belonging to them, thereby taking overcharging sessions of other vehicles.
2.Flaws:
a.Unverified ownership: Static analysis revealed that users caninitiate control requests to any vehicle connected to the network,indicating that the CMS system lacks a security mechanism to bind andverify the association between users and vehicles, thereby allowingaccess to any vehicle.
b.Improper authorization for a critical function: The controlof key vehicle functions lacks authorization verification, and thecharging and discharging of the vehicle is based solely on the user andcharging device IDs. Therefore, the core functions of charging anddischarging can be taken over by any attacker’s account.
3.Paths: 2-8-3-1-5-9-10
4.Impacts: Research indicates that when an attacker can control abotnet consisting of thousands of vehicles to perform regular chargingand discharging, it can lead to significant waste of power generationcapacity and increased wear on power generation equipment, resulting insubstantial cost waste. Additionally, it may cause overload intransmission lines and instability in the power grid, potentiallyleading to regional blackouts.
Firmware tampering and injection
1.Scenario: Due to the exposure of EVSE in vulnerableenvironments and the presence of local interfaces, such as USB, providedfor engineers to debug and maintain, if the firmware is not encrypted orsubjected to integrity checks, it can be extracted, tampered with, orimplanted with trojans by attackers.
2.Flaws: Lack of physical protection for debugging interfaces, lackof encryption and integrity checks for firmware and data, lack of updatefor firmware, use root privilege to run the process.
3.Paths: 4-1-5-9-10
4.Impacts: If attackers can control a large number of chargingdevices at the same time, form a botnet, and charge and discharge inbatches to attack the power grid, then the power grid will beoverwhelmed and eventually lead to regional power outages.
Remote attacks to charging points
1.Scenario: EVSE uses the OCPP protocol to communicateremotely with CMS, allowing an attacker to act as a man-in-the-middle,eavesdropping on their communication, stealing user information, orconducting a Denial of Service (DoS) attack to disrupt normalcommunication.
2.Flaws: Uses a low OCPP version, lower than 2.0
3.Paths: 3-5-9-10
4.Impacts: Attackers can perform man-in-the-middle attacks to readunprotected or encrypted user plaintext information, resulting in userinformation leakage, and if user information is maliciously used, it maybring economic losses to users. At the same time, if the user accountcan be controlled based on the hijacked user information, then when thenumber of user accounts is large enough, it can launch an attack on thepower grid, and the batch of charging and discharging requests willaffect the stability of the power grid.
SMS phishing attacks targeting users
1.Scenario: The attacker sends phishing SMS messages tousers, providing them with incorrect discount information, deceivingthem into collectively charging and discharging at a specific time,thereby directly impacting the power grid.
2.Flaws: The weakness of liking to take advantage.
3.Paths: 2-8-3-1-5-9-10
4.Impacts: Attackers use phishing SMS messages to trick a largenumber of users into charging at the same time, if this time happens tobe in the peak period of electricity consumption, then the expensiveelectricity price will not only cause economic losses to users, so thatthe brand reputation is damaged, in severe cases, it is a hugeadditional burden for the power supply of the grid, if the grid can notwithstand the huge power use, may cause regional power outages.
Cloud platform and application intrusion
1.Scenario: Attackers can enter the cloud management platformthrough web vulnerabilities or incorrect permission configurations totamper with configurations, steal user data, or even hack into systems,plant Trojans in products, and carry out more stealthy supply chainattacks such as updating EVSE firmware by OTA(Over The Air).
2.Flaws: OWASP flaws
3.Paths: 6-8-2,6-8-3-1-5-9-10,6-7-8-2,6-7-8-3-1-5-9-10,6-7-11
4.Impacts: As a management platform, the cloud platform has a highlevel of control authority and is connected to other cloud platforms,such as the network of the power grid. Attackers can obtain a largeamount of user data, which will not only bring user information leakageand economic losses, but also manipulate a large number of users tocharge and discharge at the same time, causing power outages on thepower grid, and can even directly move laterally to the power grid,further invading the power grid and causing incalculable losses.
Detection Mechanisms
In this section, we will discuss some detection methods for the risksthat we mentioned in the previous section.
Detection for anomalies in charging session
Detect method
To counter attacks like session hijacking, cloud intrusion, and phishingSMS, which enable batch control of vehicle charging, Kern proposes ahybrid intrusion detection method. Combining regression-basedforecasting with anomaly detection, it effectively detects known attackswith a low false positive rate and generalizes well to unknown threats.
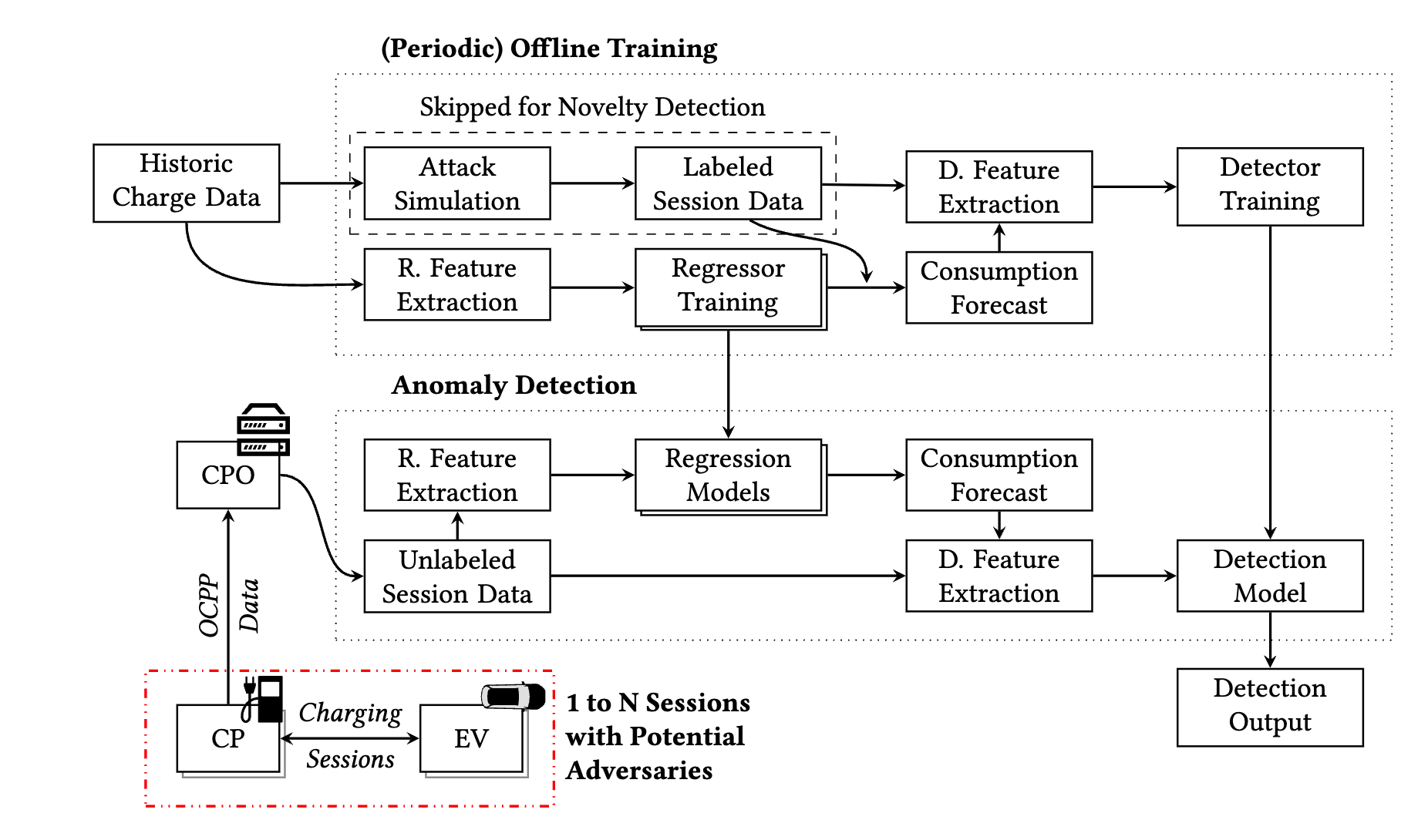
1.Charging behavior prediction: Predict the normal behavior patternsof a charging session from historical data. If the actual charging datadeviates from the predicted value, there may be an attack or anomaly.
2.Anomaly Detection: Artificial Neural Network (ANN) is used toidentify known attacks by training on existing attack samples. At thesame time, Local Outlier Factor (LOF) is used to detect unknown attacksor novel anomalies.
Detect targets
1.Data Tampering: The charging power, current, and voltageare maliciously modified.
2.Fake Charging Sessions: Fake charging sessions, stealingelectricity or tricking the billing system.
3.Load Attacks: Affect grid stability through abnormal chargingbehavior.
Deployment methods
This IDS can be deployed in the backend servers of the CMS services,where it can collect all the session data from the EVSEs in parks or athome.
Detection for SMS phishing attacks
Detection method
In response to the SMS phishing attack, Mehmood propose a kind ofdetection method based on deep learning, which combines convolutionalneural networks (CNNs) and long short-term memory networks (LSTMs) todetect SMS phishing attacks.
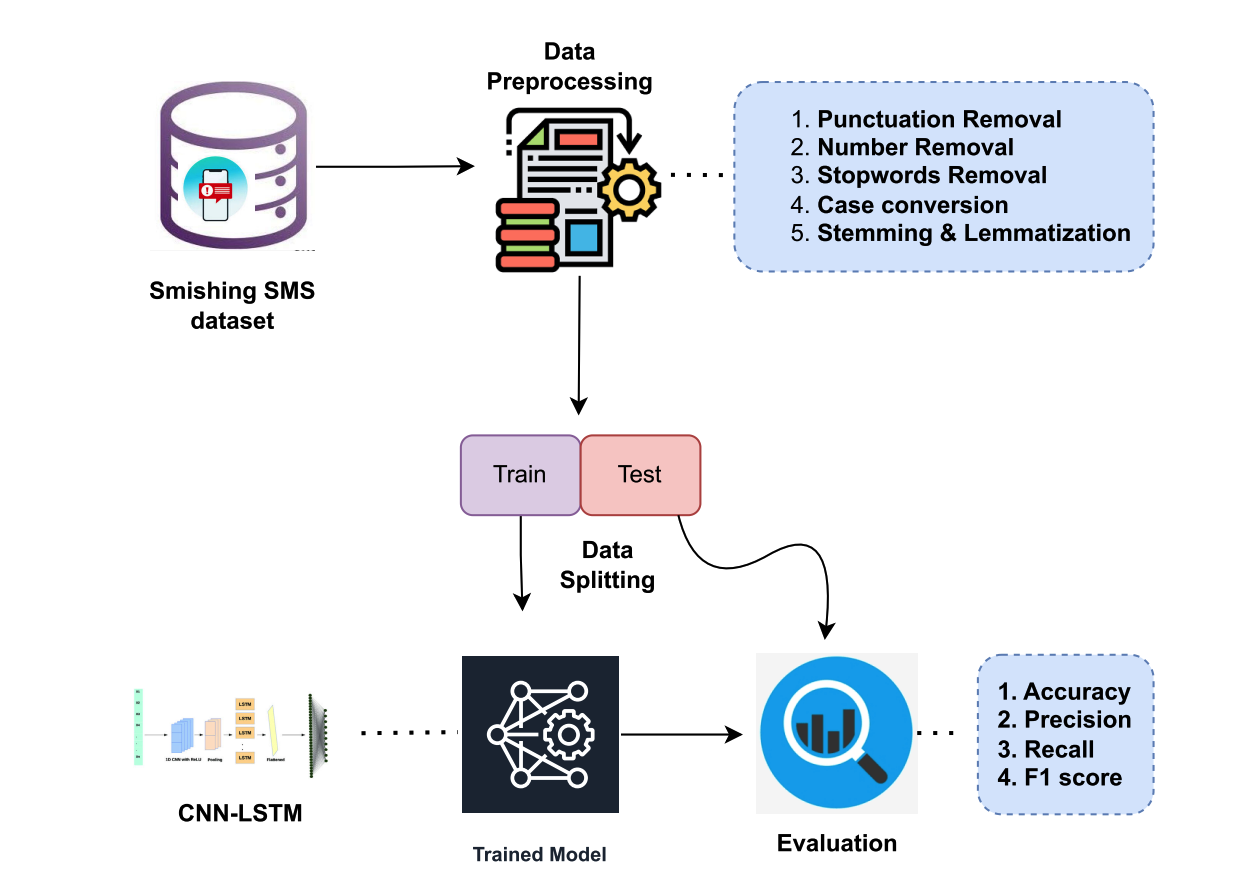
1.Model architecture: Combining CNN with LSTM, CNN is used toextract local features of SMS content, and then long-term dependenciesin SMS sequences are captured through LSTM.
2.Performance: The model achieves an accuracy of 0.9974 in theexperiment, and has high precision, recall, and F1 score, indicatingthat it has excellent performance in detecting smishing attacks andeffectively reduces the false positive rate.
Deployment methods
This model can be deployed on the SMS gateway or operator’s server, itscans and filters incoming SMS messages in real time to preventmalicious information from reaching users’ devices.
Detection for cloud platform intrusion
Detection method
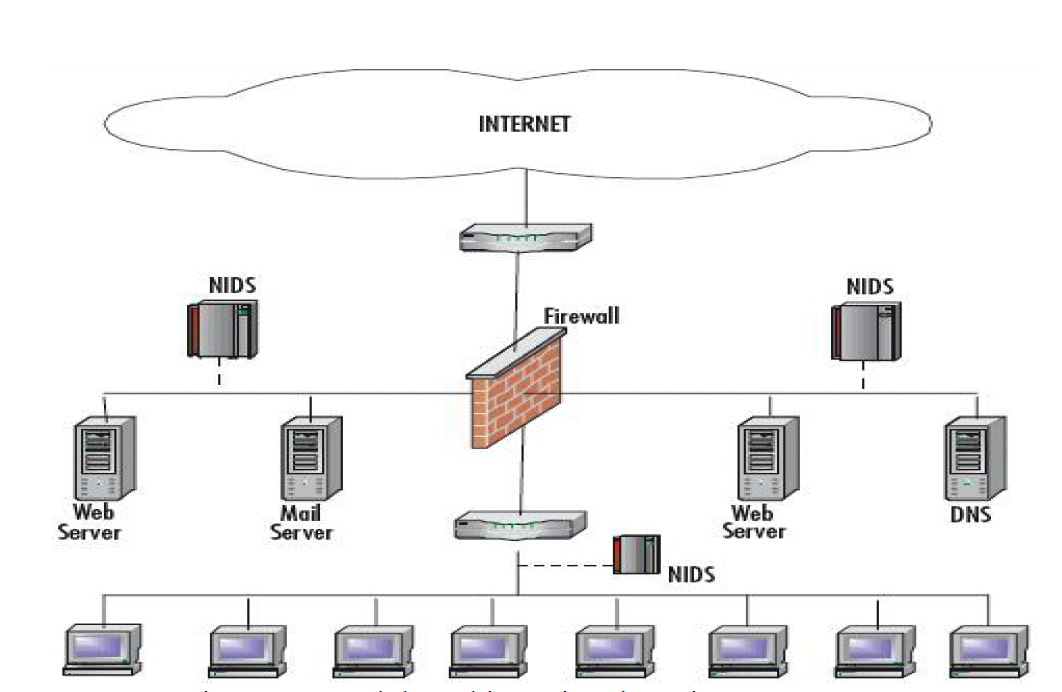
The basic method is to identify malicious activity by monitoring systemactivity and analysing patterns. HIDS (Host based Intrusion DetectionSystems) and NIDS (Network based Intrusion Detection System) are themost common way to detect attacks. We should combine them together anddeploy them in the cloud environment.
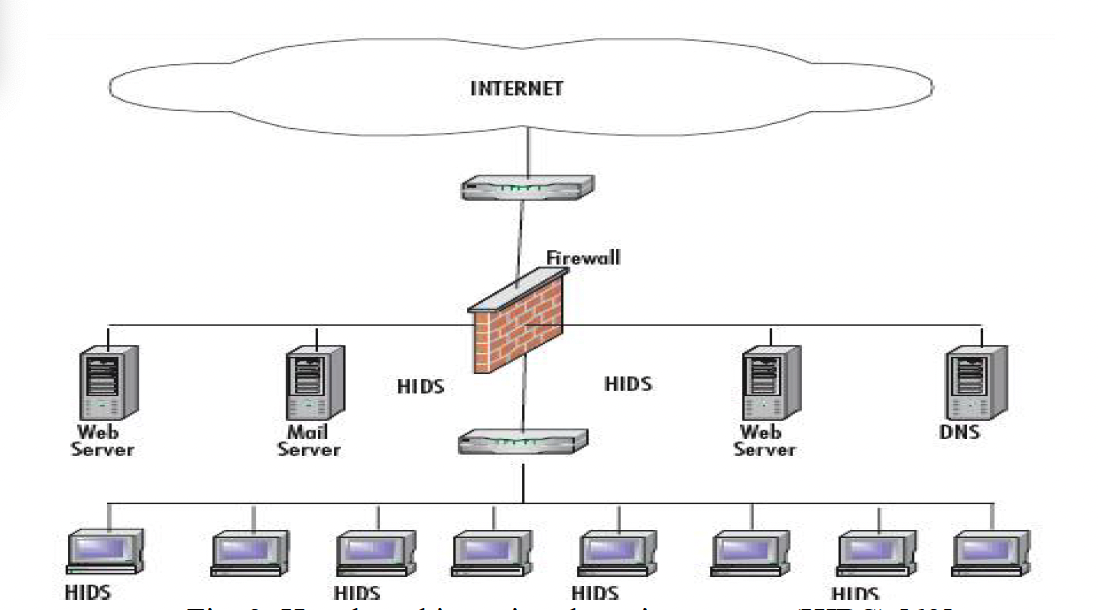
1.HIDS: Detect intrusions by analyzing operating system logs, fileintegrity, process behavior, registry modifications (Windows), andsystem calls. It identifies attacks primarily through signature-baseddetection and anomaly-based detection.
2.NIDS: NIDS listens to and analyzes network traffic, utilizingtraffic pattern analysis (anomaly detection) and signature matching(based on known attack signatures) to detect intrusion activities.Typically employing deep packet inspection (DPI) and traffic statisticalanalysis, NIDS can identify network-level threats such as DDoS attacks,port scanning, and unauthorized access.
Deployment methods
HIDS can be deployed in the cloud server, and NIDS can be deployed atthe edge of the network.
Resilience Enhancements
In this section we will discuss about the mitigation measures for theattacks that we mentioned before based on the power grid and chargingsystem scenarios, not only focusing on the technical methods but alsoincluding policies, management, regulations, and human factors
Technical approaches
1.Encrypt communication: Make sure that all thecommunications are encrypted by strong algorithm such as TLS (TransportLayer Security), ensuring that attacker cannot sniff the plaintext datain the middle, which can mitigate the man in the middle attack and stopthe user information leakage
2.Encrypt data storage: Make sure that all the data stored indatabases are encrypted by strong algorithm, ensuring that attackerscannot extract any useful data from servers even if the servers arecompromised.
3.Check firmware integrity and signature: Make sure that the EVSEfirmware cannot be changed by attackers remotely or locally, which canavoid attacker injecting eval code or conducting supply chain attack.
4.Turn off unnecessary services on the internet: Make sure that theservices that are not provided for customers are closed on the internet.Employees can just access them from the internal network or Sec VPN,which can avoid attackers attacking these web services.
**5.Timely upgrade of architecture and software/hardware versions:**Make sure that the protocol, software version, firmware are latestversion, ensuring that all the known vulnerabilities are patched, whichcan avoid attackers leveraging known vulnerabilities to attack.
6.Use IPS (Intrusion Prevention System) to defend against attack inreal time: IPS can detect and defend against attacks based onanomalies and signatures, Compared to IDS, which only monitors, IPS candirectly block attacks such as blocking IPs or dropping packets.
7.Authentication and authorization controls: Enhance authenticationand authorization control, such as using MFA (Muti-FactorAuthentication) and RBAC (rule-based access control) to make sure thatattackers cannot easily access the system as high privilege.
8.Physical interface protection: Make sure that the debug or testinterfaces on the equipment are protected physically, avoiding attackersaccess these interfaces by cable directly.
9.Abnormal Electricity Usage Detection: Power suppliers shouldmonitor abnormalities in the charging network and take timely action,such as cutting off a large number of abnormal charging requests tomaintain overall electrical stability.
Management approaches
1.Conduct security training periodically: Improvingemployees’ security awareness such as using strong password or identifyphishing emails.
2.Conduct DevSecOps (secure development and operation) and IR(Incident Response) procedure: Make sure that the whole processes ofdevelopment are combined with security monitor, discover vulnerabilitiesin advance and have a standard IR procedure, ensuring that containmentmethod are conducted timely when incident happened.
3.Regular audits and compliance checks: Make sure all the systemscomply with latest security standards and requirements, such as GDPR,ISO 27001, ISO 27002
4.Regular penetration test: Conduct pen test regularly, ensuringthat as many risks as possible can be found in advance.
Policy approaches
1.Establish uniform industry standards: The government andrelevant industry organizations should establish safety requirements andtechnical standards for charging infrastructure to ensure all chargingstations adhere to unified safety protocols.
2.Establish an industry interconnection mechanism: Electricitysuppliers and charging service providers should collaborate on securityand promptly share abnormalities.
Conclusion
This article thoroughly analyzes security vulnerabilities within theholistic architecture of electric vehicle charging services in smartgrids, utilizing the STRIDE model. It unveils risks associated with thecloud platform, users, vehicles, and communication modules, along withtheir significant impacts on the power grid. Drawing upon recentresearch advancements, it proposes advanced detection methods and offerseffective mitigation strategies from technical, managerial, and policyperspectives.